Source: www.techrepublic.com – Author: TechRepublic Academy Published April 3, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Day: April 3, 2024
xz Utils Backdoor – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier xz Utils Backdoor The cybersecurity world got really lucky last week. An intentionally placed backdoor in xz Utils, an open-source...
Declassified NSA Newsletters – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Through a 2010 FOIA request (yes, it took that long), we have copies of the NSA’s KRYPTOS Society Newsletter, “Tales...
Customer Story | Content Filter Protects Student Safety, Data Security, and CIPA Compliance At Azusa Unified School District – Source: securityboulevard.com
Source: securityboulevard.com – Author: Katie Fritchen How Azusa’s technology team makes web filtering and online safety for students easy with Content Filter by ManagedMethods Like many...
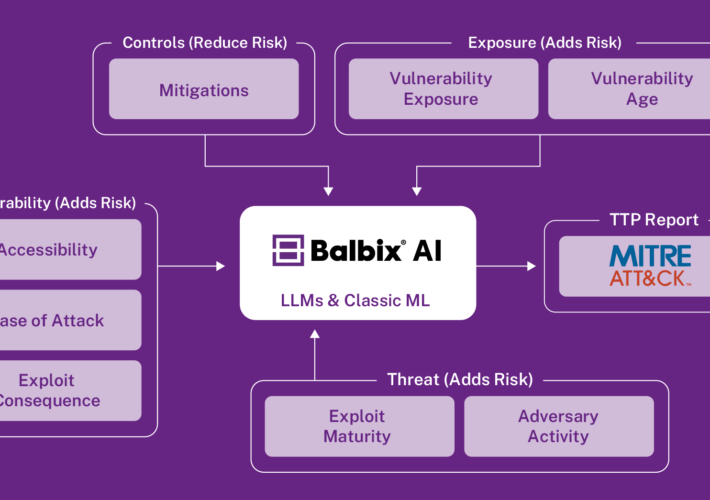
Prioritizing Cyber Risk: Get a leg up with AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aravind Iyengar In the previous blog post, we described how Balbix leverages AI to provide a unified and comprehensive visibility into your...
Guide to New CSRD Regulation for Data Center Operators – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi In the ever-evolving landscape of corporate sustainability, the European Union’s Corporate Sustainability Reporting Directive (CSRD) stands as a landmark regulation,...
How to Escape the 3 AM Page as a Kubernetes Site Reliability Engineer – Source: securityboulevard.com
Source: securityboulevard.com – Author: Stevie Caldwell It’s Saturday night. You’re out to dinner with friends. Suddenly, a familiar tune emits from your pocket. Dread fills you...
A Deep Dive on the xz Compromise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joao Correia xz is a widely distributed package that provides lossless compression for both users and developers, and is included by default...
xz Utils Backdoor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier The cybersecurity world got really lucky last week. An intentionally placed backdoor in xz Utils, an open-source compression utility, was...
Chrome’s Incognito Mode Isn’t as Private as You Think — but Google’s Not Sorry – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Class action attorney David Boies asked for $5,000 per user, but got nothing—except some assurances Google will delete data it...
Declassified NSA Newsletters – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier Through a 2010 FOIA request (yes, it took that long), we have copies of the NSA’s KRYPTOS Society Newsletter, “Tales...
The Challenges of Zero Trust 800-207 and Advocating for Prescriptive Controls – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Allers In the rapidly evolving cybersecurity landscape, a Zero Trust (ZT) model has emerged as a beacon of hope, promising enhanced...
Report Slams Microsoft for Security Blunders in Chinese Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Email Threat Protection , Fraud Management & Cybercrime Hack Targeting Top Government Officials ‘Was Preventable,’ Scathing...
New Regulations Pose Compliance Challenges – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 CISO Trainings , Standards, Regulations & Compliance , Training & Security Leadership How to Navigate New SEC Rules Information Security Media...
How to Hire, Retain and Inspire Exceptional Employees – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Professional Certifications & Continuous Training , Training & Security Leadership Leading Means Admitting What You Don’t Know – And Other Tips...
Sam Altman Out as OpenAI Startup Fund Owner – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Altman’s Role as Fund’s Sole Owner Was Meant to Be...
Live Webinar | The CISO’s Guide to a Strong Security Culture – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Security Awareness Programs & Computer-Based Training , Training & Security Leadership Presented by KnowBe4 60 Minutes Let’s...
Rubrik IPO Filing Reveals Sales Acceleration, Growing Losses – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Next-Generation Technologies & Secure Development , Privacy In First Cybersecurity IPO Filing Since 2021, Rubrik Describes...
Hackers Update Vultur Banking Malware With Remote Controls – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management Attackers Can Now Download, Alter and Delete Files – Plus...
Ransomware, Junk Bank Accounts: Cyber Threats Proliferate in Vietnam – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Jose Vilchez via Alamy Stock Photo For one week last month, Vietnamese brokerage VNDirect Cyber Systems shut...
China-Linked Threat Actor Taps ‘Peculiar’ Malware to Evade Detection – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Panchenko Vladimir via Shutterstock Researchers have spotted Earth Freybug, a China-linked threat actor, using a new malware...
Fortanix Builds Private Search for AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer The inner-functioning of AI-powered search is more complex than plain-text search via Google when it comes to extracting...
NIST Wants Help Digging Out of Its NVD Backlog – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Senior Editor, Dark Reading Source: GK Images via Alamy Stock Photo After warning it can’t keep up with the exploding...
HHS Plans for Cyber ‘One-Stop Shop’ After United Healthcare Attack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Olekcii Mach via Alamy Stock Photo The Department of Health and Human Services (HHS) has...
Attackers Abuse Google Ad Feature to Target Slack, Notion Users – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Bits and Splits via Shutterstock Attackers are once again abusing Google Ads to target people with info-stealing...
Instilling the Hacker Mindset Organizationwide – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tim Chase Tim Chase, Global Field CISO, Lacework April 2, 2024 3 Min Read Source: Anna Berkut via Alamy Stock Photo COMMENTARY...
Cyberattacks Wreaking Physical Disruption on the Rise – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Imagebroker via Alamy Stock Photo At least 68 cyberattacks last year caused physical consequences to operational technology...
Funding the Organizations That Secure the Internet – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jennifer Lawinski 5 Min Read Source: Nico El Nino via Alamy Stock Photo Much of our everyday lives, from banking to turning...
Iran’s Evolving Cyber-Enabled Influence Operations to Support Hamas – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security 4 Min Read Source: Ruma Aktar via Alamy Stock Photo When the war between Israel and Hamas began on Oct....
Proofpoint Named an Overall Leader in KuppingerCole Leadership Compass for Email Security – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Proofpoint’s Threat Protection platform achieves a “Strong Positive” rating in all categories and is recognized as a Product Leader, Innovation Leader,...