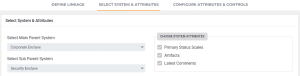
Source: securityboulevard.com – Author: Ignyte Team If you are managing multiple GRC frameworks for multiple environments, then you know how powerful it is to have clearly-defined...
Month: February 2024
Making Companies Whole: The Impact of Cyber Insurance on Materiality – Source: securityboulevard.com
Source: securityboulevard.com – Author: Axio Hot Topics Malicious Packages in npm, PyPI Highlight Supply-Chain Threat USENIX Security ’23 – Synchronization Storage Channels (S2C): Timer-less Cache Side-Channel...
Randall Munroe’s XKCD ‘Light Leap Years’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
USENIX Security ’23 – Daniel Katzman, William Kosasih, Chitchanok Chuengsatiansup, Eyal Ronen, Yuval Yarom – The Gates of Time: Improving Cache Attacks with Transient Execution – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
LockBit Ransomware Group Returns After Law Enforcement Operation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The LockBit ransomware group is swinging back days after U.S. and UK law enforcement agencies announced they had disrupted the...
The xSPM Trend: Security Posture Management for Everything – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gilad David Maayan Before we dive into the xSPM trend, let’s define what security posture management (SPM) is. SPM refers to the...
Profiling the xDedic Cybercrime Service Enterprise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dancho Danchev The popular cybercrime-friendly xDedic service was recently shut down and in this analysis we’ll take an in-depth look inside the...
Lost to the Highest Bidder: The Economics of Cybersecurity Staffing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maria Chachas Mastakas For about a decade, much has been written about the scarcity of qualified cybersecurity talent. There’s no lack of...
North Korean Group Seen Snooping on Russian Foreign Ministry – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Government Espionage Groups Deploy Info Stealer to Monitor Russia’s Diplomatic Moves...
SSH Exec Rami Raulas Named Interim CEO in Finnish Shakeup – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Encryption & Key Management , Governance & Risk Management , Operational Technology (OT) Teemu Tunkelo Left SSH Abruptly After License Sales...
Groups Warn Health Sector of Change Healthcare Cyber Fallout – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Fraud Management & Cybercrime , Governance & Risk Management Some Researchers Confident ConnectWise ScreenConnect Flaw Was...
NIST Unveils Second Iteration of Cybersecurity Framework – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management New CSF Adds ‘Governance’ to Core Functions Chris Riotta (@chrisriotta) • February 26,...
China Launches New Cyber-Defense Plan for Industrial Networks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: NicoElNino via Shutterstock China’s Ministry of Industry and Information Technology (MIIT) this week released a new strategy for...
UnitedHealth subsidiary Optum hack linked to BlackCat ransomware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan A cyberattack on UnitedHealth Group subsidiary Optum that led to an ongoing outage impacting the Change Healthcare payment exchange platform was linked...
New IDAT loader version uses steganography to push Remcos RAT – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A hacking group tracked as ‘UAC-0184’ was observed utilizing steganographic image files to deliver the Remcos remote access trojan (RAT)...
Mowing down demons: DOOM comes to Husqvarna smart lawnmowers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Image: Midjourney If you ever wanted to play DOOM on a lawnmower, you will soon have your chance with a...
White House urges devs to switch to memory-safe programming languages – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney The White House Office of the National Cyber Director (ONCD) urged tech companies today to switch to memory-safe...
Hackers exploit 14-year-old CMS editor on govt, edu sites for SEO poisoning – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Threat actors are exploiting a CMS editor discontinued 14 years ago to compromise education and government entities worldwide to poison...
Russian hackers shift to cloud attacks, US and allies warn – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney Members of the Five Eyes (FVEY) intelligence alliance warned today that APT29 Russian Foreign Intelligence Service (SVR) hackers...
Steel giant ThyssenKrupp confirms cyberattack on automotive division – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Steel giant ThyssenKrupp confirms that hackers breached systems in its Automotive division last week, forcing them to shut down IT systems...
Cybersecurity Training Not Sticking? How to Fix Risky Password Habits – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software Organizations recognize the cybersecurity risks posed by their end-users, so they invest in security and awareness training programs...
Hijacked subdomains of major brands used in massive spam campaign – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A massive ad fraud campaign named “SubdoMailing” is using over 8,000 legitimate internet domains and 13,000 subdomains to send up...
Annual Report – Vulnerability Intelligence
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The IoTSI SCCI Framework
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Booking.com refund request? It might be an Agent Tesla malware attack – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Always be wary of opening unsolicited attachments – they might harbour malware. That’s a message that is being strongly underlined...
The LockBit ransomware gang rears its ugly head again, after law enforcement takedown – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Surprise! The LockBit ransomware group has re-emerged, just days after a high-profile law enforcement operation seized control of its infrastructure...
The Essential Guide to Secure Al
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Art of Balancing Cybersecurity and Business Growth
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
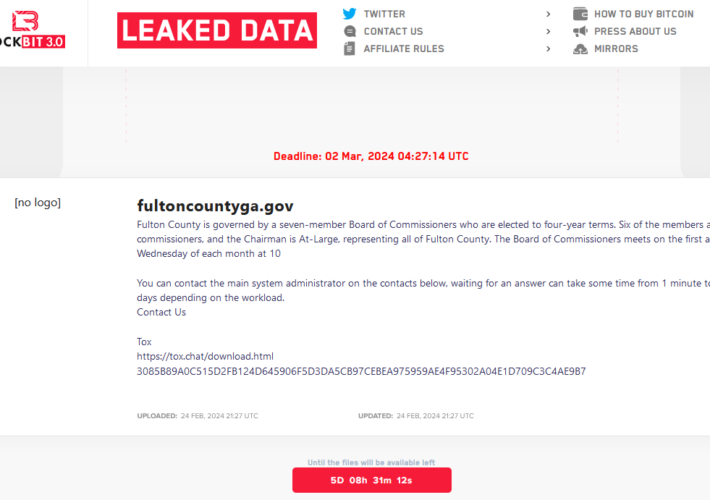
FBI’s LockBit Takedown Postponed a Ticking Time Bomb in Fulton County, Ga. – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The FBI’s takedown of the LockBit ransomware group last week came as LockBit was preparing to release sensitive data stolen from...
Challenging password dogma – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Palmer Passwords should be the easiest area of security. Every organisation has a password policy. Every organisation used passwords. Everyone at...