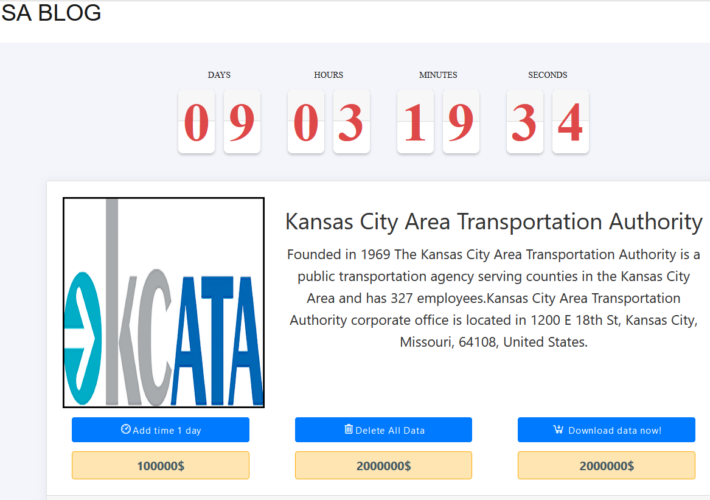
Source: www.bleepingcomputer.com – Author: Bill Toulas The Kansas City Area Transportation Authority (KCATA) announced it was targeted by a ransomware attack on Tuesday, January 23. KCATA...
Month: January 2024
NASCIO, PTI on What’s Coming in 2024 for State and Local IT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity Every January, NASCIO and PTI release their forecasts for the coming year based on what government leaders are saying....
Navigating the Future: DevOps Predictions for 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Esther Han As technology continues to evolve at an unprecedented pace, the field of DevOps is no exception. DevOps, the cultural and...
Doubling Down on Security: The Critical Role of Two-Factor Authentication – Source: securityboulevard.com
Source: securityboulevard.com – Author: Leigh Dow Safeguarding our online accounts has never been more crucial. One of the most effective tools at our disposal is Two-Factor...
Zero-day Confluence RCE Vulnerability Blocked by Contrast Runtime Security | CVE-2023-22527 | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joseph Beeton, Senior Application Security Researcher, Contrast Security Security Bloggers Network Home » Security Bloggers Network » Zero-day Confluence RCE Vulnerability Blocked...
Medusa ransomware attack hit Kansas City Area Transportation Authority – Source: securityaffairs.com
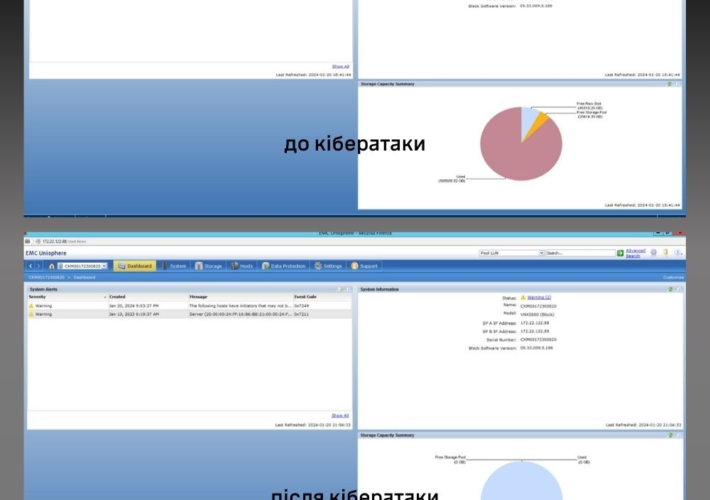
Source: securityaffairs.com – Author: Pierluigi Paganini Medusa ransomware attack hit Kansas City Area Transportation Authority Medusa ransomware gang claimed responsibility for the attack against the Kansas...
Security Affairs newsletter Round 456 by Pierluigi Paganini – INTERNATIONAL EDITION – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Medusa ransomware attack hit Kansas City Area Transportation Authority | Security Affairs newsletter Round 456 by Pierluigi Paganini – INTERNATIONAL...
Weekly Update 384 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt I spent longer than I expected talking about Trello this week, in part because I don’t feel the narrative they...
How Kratikal Helps Businesses Prevent Cyber Attacks? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover The rise in cyber attacks has become a major worry. This issue is for organizations where data storage and technical...
New Ransomware Reporting Requirements Kick in as Victims Increasingly Avoid Paying – Source: securityboulevard.com
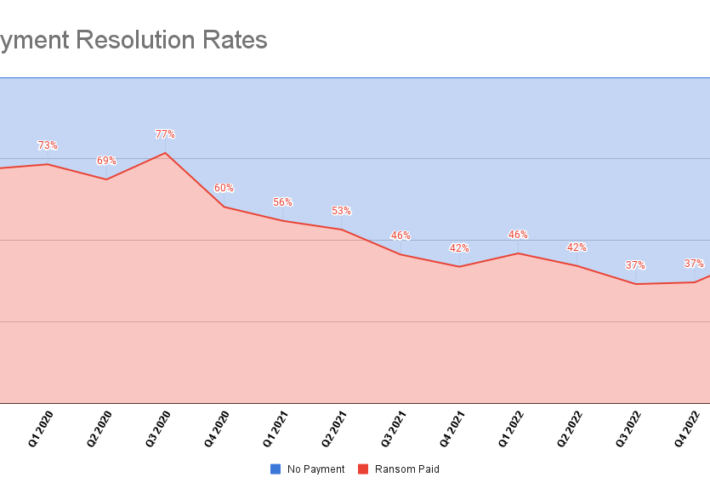
Source: securityboulevard.com – Author: Bill Siegel Table of Contents Ransomware Bans Payment Rates Types of Ransomware Attack Vectors & TTPs Industries Impacted As the year turns,...
Novel Threat Tactics, Notable Vulnerabilities, Current Trends, and Data Leaks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pondurance Every month, the Pondurance team hosts a webinar to keep clients current on the state of cybersecurity. In December, the team...
Friday Squid Blogging: Footage of Black-Eyed Squid Brooding Her Eggs – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Footage of Black-Eyed Squid Brooding Her Eggs Amazing footage of a black-eyed squid (Gonatus onyx) carrying...
NRC Issues Recommendations for Better Network, Software Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: Olivier Le Moal via Alamy Stock Photo The Network Resilience Coalition issued recommendations intended to improve network security infrastructure...
CISO Corner: Deep Dive Into SecOps, Insurance, & CISOs’ Evolving Role – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Panther Media GmbH via Alamy Stock Photo Welcome to CISO Corner, Dark Reading’s weekly...
Google Kubernetes Clusters Suffer Widespread Exposure to External Attackers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Artemis Diana via Alamy Stock Photo The authentication mechanism within the Google Kubernetes Engine (GKE) has a...
Hackers Blast Violent Gaza Message at a Popular Israeli Movie Theater – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Bildagentur-online/Schoening via Alamy Stock Photo On Jan. 23, Turkish hacktivists projected political messages about the war in...
The CISO Role Undergoes a Major Evolution – Source: www.darkreading.com
Source: www.darkreading.com – Author: Mark Bowling Source: Panther Media GmbH via Alamy Stock Photo COMMENTARY We are in a time of major evolution for the chief...
Hook Younger Users With Cybersecurity Education Designed for Them – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tatiana Walk-Morris Source: Andrey Popov via Adobe Stock Photo Even though baby boomers have garnered a reputation for being less digitally savvy...
The Week in Ransomware – January 26th 2024 – Govts strike back – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Governments struck back this week against members of ransomware operations, imposing sanctions on one threat actor and sentencing another to...
Kansas public transportation authority hit by ransomware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Kansas City Area Transportation Authority (KCATA) announced it was targeted by a ransomware attack on Tuesday, January 23. KCATA...
Pro-Ukraine hackers wiped 2 petabytes of data from Russian research center – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pro-Ukraine hackers wiped 2 petabytes of data from Russian research center The Main Intelligence Directorate of Ukraine’s Ministry of Defense...
Participants earned more than $1.3M at the Pwn2Own Automotive competition – Source: securityaffairs.com
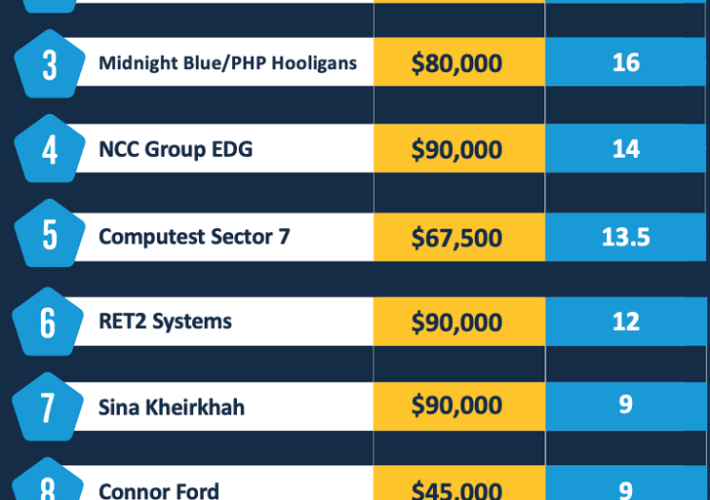
Source: securityaffairs.com – Author: Pierluigi Paganini Participants earned more than $1.3M at the Pwn2Own Automotive competition Bug bounty hunters earned more than $1.3 million for hacking...
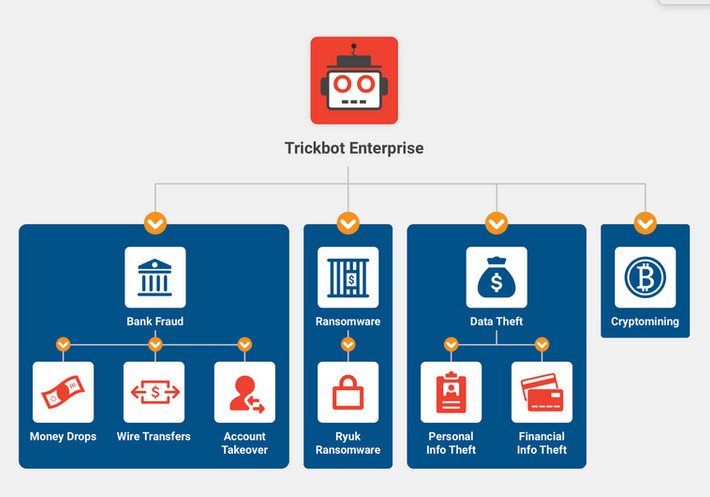
A TrickBot malware developer sentenced to 64 months in prison – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A TrickBot malware developer sentenced to 64 months in prison The Russian national malware developer Vladimir Dunaev was sentenced to...
AllaKore RAT Malware Targeting Mexican Firms with Financial Fraud Tricks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 27, 2024NewsroomMalware / Software Update Mexican financial institutions are under the radar of a new spear-phishing campaign that delivers a...
Malwarebytes vs. Norton (2024): Which Antivirus Solution Is Better? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jonathan Kalibbala We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
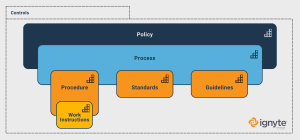
Cybersecurity Standards vs Procedures vs Controls vs Policies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Max Aulakh Cybersecurity is a vast and complex field, and it’s made more complicated as technology – both infrastructure and in terms...
USENIX Security ’23 – Yue Xiao, Zhengyi Li, Yue Qin, Xiaolong Bai, Jiale Guan, Xiaojing Liao, and Luyi Xing – Lalaine: Measuring and Characterizing Non-Compliance of Apple Privacy Labels – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Yue Xiao, Zhengyi Li, Yue Qin, Xiaolong...
DevSecOps maturity model: A beginner’s guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens In recent years, DevSecOps swiftly emerged as a crucial new paradigm in software development, prioritizing the integration of security into...
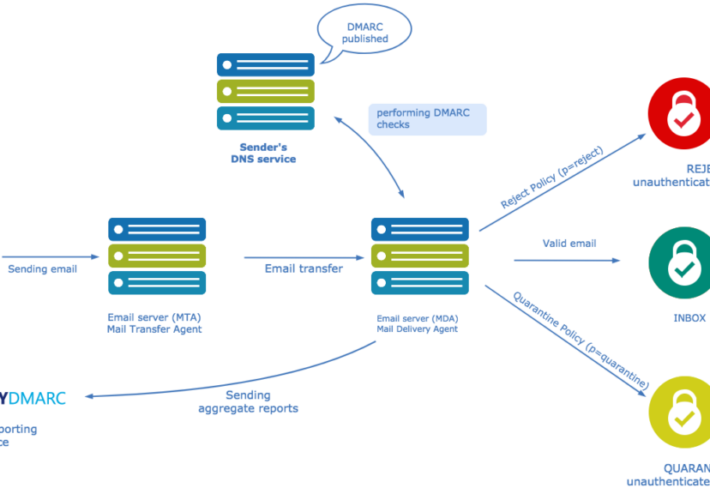
What is DMARC? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ani Avetisyan With the rising volume of fraudulent emails and AI-enhanced phishing scams, industry giants such as Google, Yahoo, and Microsoft have...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #276 – Bringing Business and IT Together – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics Cybersecurity Standards vs Procedures vs Controls vs Policies USENIX Security ’23 – Yue Xiao, Zhengyi Li, Yue Qin,...