Source: securityboulevard.com – Author: Ani Avetisyan
With the rising volume of fraudulent emails and AI-enhanced phishing scams, industry giants such as Google, Yahoo, and Microsoft have doubled their email security efforts. This shift, in turn, has significantly amplified the demand for email security solutions like DMARC.
What is DMARC? DMARC stands for “Domain-based Message Authentication, Reporting, and Conformance.” It is an email authentication protocol that helps protect organizations and their email recipients from phishing and spoofing.
DMARC builds on two existing email authentication technologies: Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM). SPF allows a domain owner to specify which mail servers are authorized to send emails on behalf of their domain, while DKIM allows the sender to digitally sign their emails, providing a means for the recipient to verify the message’s authenticity.
How Does DMARC Work?
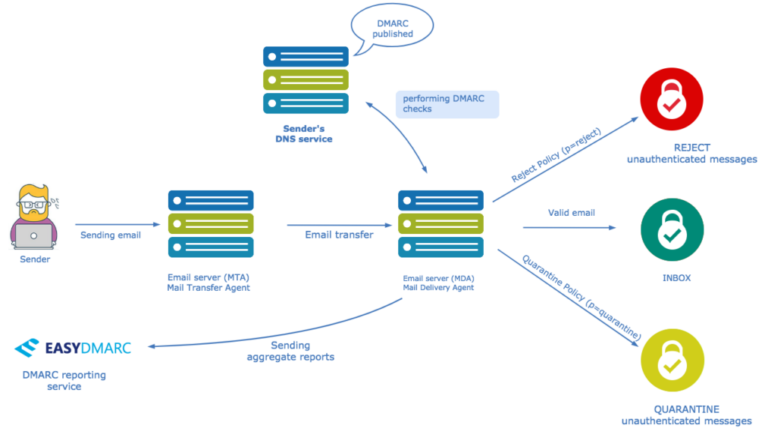
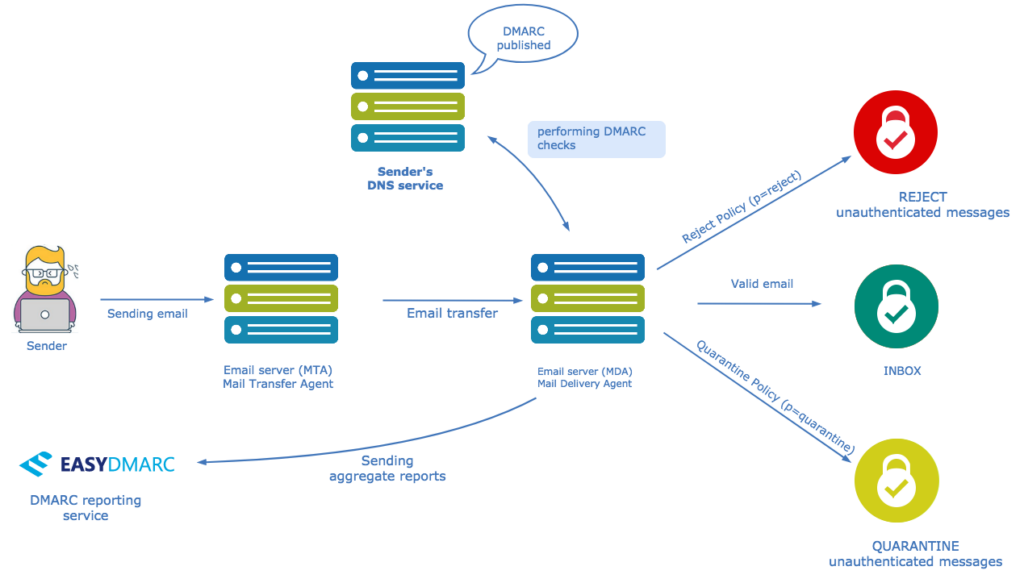
DMARC allows domain owners to publish policies in their DNS (Domain Name System) records specifying how email receivers should handle messages that claim to be from their domain.
There are three main DMARC policies that a domain owner can specify:
None (p=none)
This policy is used for monitoring purposes. With this policy, email receivers do not take specific action based on the DMARC results. Instead, the domain owner receives reports about the authentication status of emails claiming to be from their domain. This allows them to assess the impact of implementing DMARC without impacting the delivery of emails.
Quarantine (p=quarantine)
With this policy, if an incoming email fails DMARC authentication, the email receiver is instructed to treat it with suspicion and may choose to move it to the recipient’s spam or junk folder. The email is not outright rejected, but it is flagged as potentially suspicious.
Reject (p=reject)
This is the strictest DMARC policy. If an incoming email fails DMARC authentication, the email receiver is instructed to reject the message outright, preventing it from reaching the recipient’s inbox. This policy provides the highest level of protection against email spoofing and phishing.
Organizations are advised to start with a “p=none” policy for monitoring, analyze their email activity and then gradually move to a more restrictive policy like “p=quarantine” or “p=reject”.
Here’s an example illustration of how DMARC works:
What Are the Advantages of DMARC?
Implementing DMARC comes with several advantages:
- Phishing and spoofing prevention: DMARC helps prevent phishing attacks by allowing email recipients to verify that the sender is legitimate and hasn’t been spoofed.
- Increased email deliverability: DMARC can positively impact email deliverability by clearly indicating to email providers that your messages are legitimate.
- Brand protection: DMARC helps protect your brand’s reputation by reducing the risk of attackers using your domain to send fraudulent emails.
- Reporting and visibility: DMARC generates reports that provide insights into email traffic, which allows you to monitor and fine-tune your email security policies.
- Regulatory compliance: DMARC adoption may align with certain regulatory requirements and industry standards related to email security, contributing to overall compliance efforts.
- Improved customer trust: By securing your email communication, you can enhance customer trust and confidence in your online communications.
Implementing DMARC requires careful configuration and ongoing monitoring, but the benefits in terms of email security and trustworthiness can be substantial.
Did You Know? 85% of consumers will not do business with a company if they have concerns about its security practices.
The Structure of DMARC Records
The structure of DMARC records includes several key components or tags specifying how to handle messages claiming to be from the organization’s domain.
| Tag Name | Purpose | Sample |
| v | Protocol version | v=DMARC1 |
| p | Policy for organizational domain | p=quarantine |
| pct | Percentage of messages subjected to filtering | pct=20 |
| rua | Reporting URI of aggregate reports | rua=mailto:[email protected] |
| ruf | Reporting URI for forensic reports | ruf=mailto:[email protected] |
| adkim | Alignment mode for DKIM | adkim=s |
| aspf | Alignment mode for SPF | aspf=r |
| sp | Policy for subdomains | sp=reject |
Here’s an example of a simple DMARC TXT record:
“v=DMARC1; p=reject; rua=mailto:[email protected]; ruf=mailto:[email protected]; pct=90; adkim=s; aspf=r”
In this example, the organization has implemented DMARC with the strongest policy of “p=reject,” requests aggregate reports to be sent to “[email protected],” forensic reports to “[email protected],” allows for 90% flexibility in applying the policy, and uses strict DKIM and SPF alignment.
Your DMARC Journey Made Simple
While DMARC implementation requires technical expertise, EasyDMARC has designed various tools to make your DMARC journey a breeze. We provide comprehensive guidance and walk you through every stage of email authentication to ensure you have the knowledge and tools necessary for smooth compliance.
The post What is DMARC? appeared first on EasyDMARC.
*** This is a Security Bloggers Network syndicated blog from EasyDMARC authored by Ani Avetisyan. Read the original post at: https://easydmarc.com/blog/what-is-dmarc-overview/
Original Post URL: https://securityboulevard.com/2024/01/what-is-dmarc/
Category & Tags: Security Awareness,Security Bloggers Network,Blog,dmarc,email security – Security Awareness,Security Bloggers Network,Blog,dmarc,email security