Source: securityaffairs.com – Author: Pierluigi Paganini
Participants earned more than $1.3M at the Pwn2Own Automotive competition

Bug bounty hunters earned more than $1.3 million for hacking Teslas, infotainment systems, and electric vehicle chargers at the Pwn2Own Automotive competition.
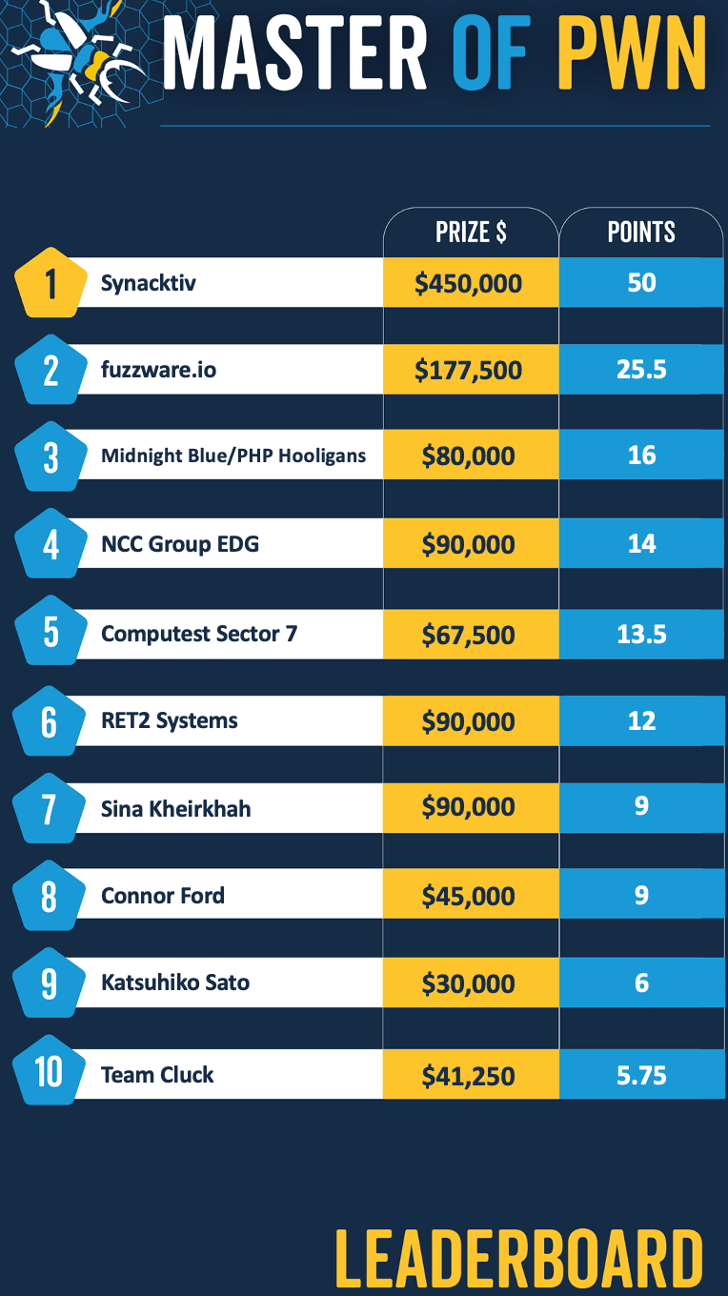
The Zero Day Initiative’s Pwn2Own Automotive competition has ended, participants demonstrated 49 zero-day vulnerabilities affecting automotive products earning a total of $1,323,750.
The amazing Synacktiv team won the competition and earned a total of $450,000. The team demonstrated successful attacks against Tesla’s modem and the infotainment system.
The first ever #Pwn2Own Automotive is in the books! We awarded $1,323,750 throughout the event and discovered 49 unique zero-days. A special congratulations to @synacktiv, the Masters of Pwn! Stay with us here and at the ZDI blog as we prepare for Pwn2Own Vancouver in March. pic.twitter.com/ov2B1rtA8c
— Zero Day Initiative (@thezdi) January 26, 2024
In second place is the team fuzzware.io with $177,500, followed by the team Midnight Blue/PHP Hooligans with $80,000.
The biggest payout was awarded to the team fuzzware.io that exploited a buffer overflow to hack the EMPORIA EV Charger Level 2. They earned $60,000 and 6 Master of Pwn Points.
The team fuzzware.io also chained to flaws to hack the Phoenix Contact CHARX SEC-3100. However, one of the bugs was previously known, for this reason, the attempt was classified as a a bug collision. They earned $22,500 and 4.5 Master of Pwn Points.
The researcher Connor Ford of Nettitude demonstrated a stack-based buffer overflow to hack the JuiceBox 40 Smart EV Charging Station. He earned $30,000 and 6 Master of Pwn Points.
The full list of the exploits demonstrated on day three of PWN2OWN AUTOMOTIVE 2024 is available here.
https://www.zerodayinitiative.com/blog/2024/1/25/pwn2own-automotive-2024-day-three-results
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Pwn2Own)
Original Post URL: https://securityaffairs.com/158202/hacking/pwn2own-automotive-day-three.html
Category & Tags: Breaking News,Hacking,hacking news,information security news,IT Information Security,Pierluigi Paganini,Pwn2Own Automotive,Security Affairs,Security News – Breaking News,Hacking,hacking news,information security news,IT Information Security,Pierluigi Paganini,Pwn2Own Automotive,Security Affairs,Security News