Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Footage of Black-Eyed Squid Brooding Her Eggs Amazing footage of a black-eyed squid (Gonatus onyx) carrying...
Day: January 27, 2024
NRC Issues Recommendations for Better Network, Software Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer Source: Olivier Le Moal via Alamy Stock Photo The Network Resilience Coalition issued recommendations intended to improve network security infrastructure...
CISO Corner: Deep Dive Into SecOps, Insurance, & CISOs’ Evolving Role – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Panther Media GmbH via Alamy Stock Photo Welcome to CISO Corner, Dark Reading’s weekly...
Google Kubernetes Clusters Suffer Widespread Exposure to External Attackers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Artemis Diana via Alamy Stock Photo The authentication mechanism within the Google Kubernetes Engine (GKE) has a...
Hackers Blast Violent Gaza Message at a Popular Israeli Movie Theater – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Bildagentur-online/Schoening via Alamy Stock Photo On Jan. 23, Turkish hacktivists projected political messages about the war in...
The CISO Role Undergoes a Major Evolution – Source: www.darkreading.com
Source: www.darkreading.com – Author: Mark Bowling Source: Panther Media GmbH via Alamy Stock Photo COMMENTARY We are in a time of major evolution for the chief...
Hook Younger Users With Cybersecurity Education Designed for Them – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tatiana Walk-Morris Source: Andrey Popov via Adobe Stock Photo Even though baby boomers have garnered a reputation for being less digitally savvy...
The Week in Ransomware – January 26th 2024 – Govts strike back – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Governments struck back this week against members of ransomware operations, imposing sanctions on one threat actor and sentencing another to...
Kansas public transportation authority hit by ransomware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Kansas City Area Transportation Authority (KCATA) announced it was targeted by a ransomware attack on Tuesday, January 23. KCATA...
Pro-Ukraine hackers wiped 2 petabytes of data from Russian research center – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pro-Ukraine hackers wiped 2 petabytes of data from Russian research center The Main Intelligence Directorate of Ukraine’s Ministry of Defense...
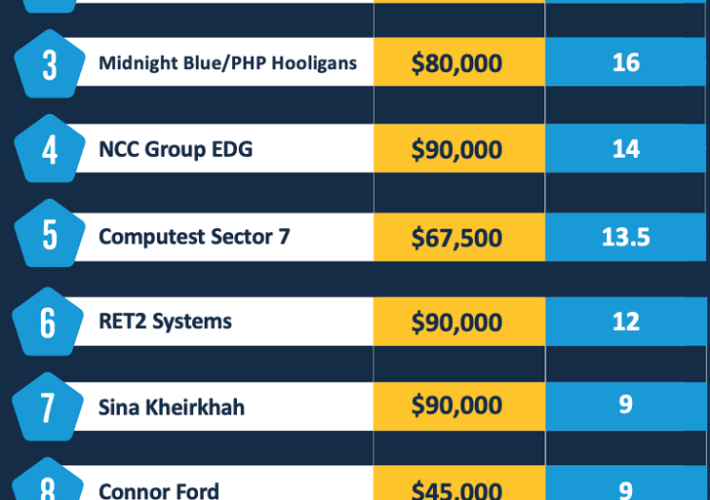
Participants earned more than $1.3M at the Pwn2Own Automotive competition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Participants earned more than $1.3M at the Pwn2Own Automotive competition Bug bounty hunters earned more than $1.3 million for hacking...
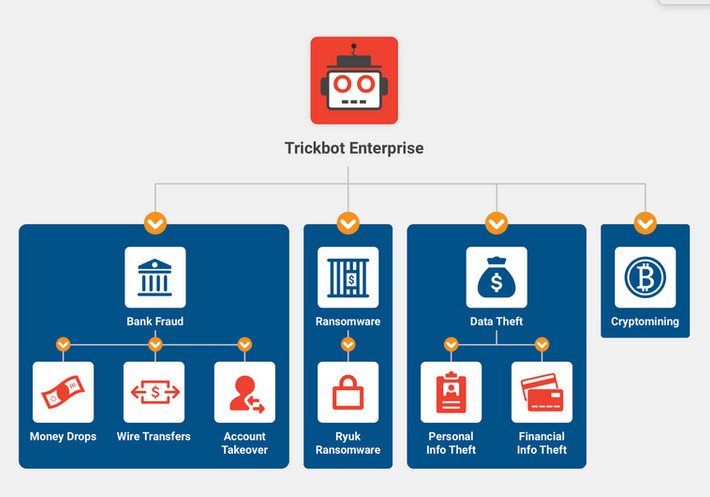
A TrickBot malware developer sentenced to 64 months in prison – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A TrickBot malware developer sentenced to 64 months in prison The Russian national malware developer Vladimir Dunaev was sentenced to...
AllaKore RAT Malware Targeting Mexican Firms with Financial Fraud Tricks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jan 27, 2024NewsroomMalware / Software Update Mexican financial institutions are under the radar of a new spear-phishing campaign that delivers a...
Malwarebytes vs. Norton (2024): Which Antivirus Solution Is Better? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jonathan Kalibbala We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
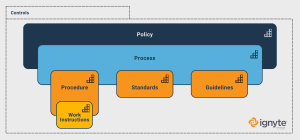
Cybersecurity Standards vs Procedures vs Controls vs Policies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Max Aulakh Cybersecurity is a vast and complex field, and it’s made more complicated as technology – both infrastructure and in terms...
USENIX Security ’23 – Yue Xiao, Zhengyi Li, Yue Qin, Xiaolong Bai, Jiale Guan, Xiaojing Liao, and Luyi Xing – Lalaine: Measuring and Characterizing Non-Compliance of Apple Privacy Labels – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Yue Xiao, Zhengyi Li, Yue Qin, Xiaolong...
DevSecOps maturity model: A beginner’s guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens In recent years, DevSecOps swiftly emerged as a crucial new paradigm in software development, prioritizing the integration of security into...
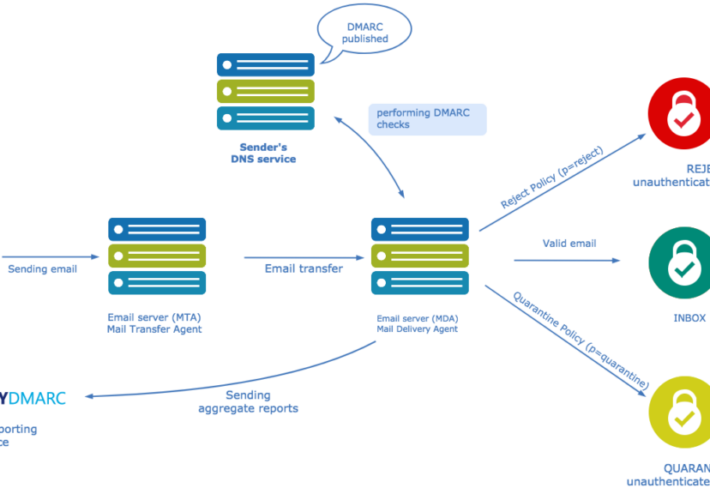
What is DMARC? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ani Avetisyan With the rising volume of fraudulent emails and AI-enhanced phishing scams, industry giants such as Google, Yahoo, and Microsoft have...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #276 – Bringing Business and IT Together – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics Cybersecurity Standards vs Procedures vs Controls vs Policies USENIX Security ’23 – Yue Xiao, Zhengyi Li, Yue Qin,...
Cyber security and AI: Should machines be included in your training program? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Scott Wright The way AI stores data is a huge concern. As security managers, it makes sense that we are hesitant to...
USENIX Security ’23 – POLICYCOMP: Counterpart Comparison of Privacy Policies Uncovers Overbroad Personal Data Collection Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics Cybersecurity Standards vs Procedures vs Controls vs Policies USENIX Security ’23 – Yue Xiao, Zhengyi Li, Yue Qin,...
QR Code Scammers are Changing Tactics to Evade Detection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Check Point researchers last year saw a 587% increase between August and September of phishing attacks enticing unsuspecting targets to...
90 Days of Learning, Good Surprises and Extreme Optimism – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Callahan January is often a time for reflection, and setting goals and aspirations for the months and the year ahead. It’s...
Why We Need to Cultivate a Confidential Computing Ecosystem – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ijlal Loutfi Researchers have been working on solutions for runtime security for years now. Computing data and deriving value from it —...
Developers Hold the New Crown Jewels. Are They Properly Protected? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Aaron Bray, CEO. Phylum Cybersecurity has changed dramatically in the last four years. During the pandemic, organizations around the...
Civil Society Sounds Alarms on UN Cybercrime Treaty – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Government Final Round of Negotiations Set to Begin on Monday Akshaya Asokan (asokan_akshaya) •...
Therapy Provider Notifying 4 Million Patients of PJ&A Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Breach Notification , Cybercrime Concentra Health Services Joins List of Those Affected in Transcriber’s Data Breach...
ISMG Editors: Emerging AI Tech for Cloud Security in 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Security Operations , Video Payments Expert Troy Leach Joins the Panel to Cover AI, Zero Trust and IoT...
CISA Aiming to Improve SBOM Implementation With New Guidance – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Government , Industry Specific , Software Bill of Materials (SBOM) US Cyber Agency Issues Step-by-Step Guide to Build Software Bills of...
Wyden Releases Documents Confirming the NSA Buys Americans’ Internet Browsing Records – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Washington, D.C. – U.S. Senator Ron Wyden, D-Ore., released documents confirming the National Security Agency buys Americans’ internet records, which can...