The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Year: 2023
NIST Cloud Computing Forensic Reference Architecture
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Private APIs at Risk
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
New Vulnerability Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Investigate FakeGPT web extension
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Optimizing Cybersecurity Costs
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
NMAP CHEAT SHEET
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Adzapier Consent Management Platform
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Data Breach Response
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
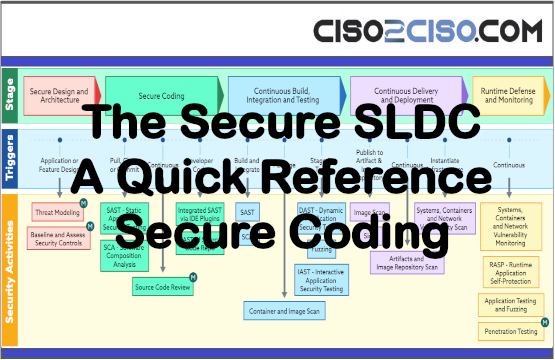
The Secure SLDC – A Quick Reference Secure Coding
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Are you preparing for the Security+ certification exam
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Bitdefender-PR-Whitepaper-S1deloadStealer-creat6669-en-EN
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Brute Force Attack Explained
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
HOW GENERATIVE AI IS CHANGING SECURITY RESEARCH
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
AWS Security Maturity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Windows Event Log Analysis
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
AWS Security Incident Response Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Risk Management amp Governance Knowledge Area
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Malware Analysis By ChatGPT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
AD Security Checklist
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
MOVEIT ADVISORY NOTE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
TACFAM DB-120WL
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Ultimate Cheatsheet for Critical Thinking_Pro Vs Anti AI PDF
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SAML (Security Assertion Markup Language
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Securing Java apps with OAuth2, OIDC and Spring Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Threat Intelligence and Darkweb Monitoring
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Network Security Checklist
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Playbook para Respuesta a Incidente Cibernetic
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
IRIS 2022 Cyentia
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ASPI
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...