The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: October 31, 2023
The Ultimate Guide to Information Security and Continuity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Professional Penetration Testing – Creating and Operating a Formal Hacking Lab
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DoD Cyber Strategy Summary 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 – Cyber Strategy of The Departament of Defence
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Active Directory Handbook
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
COSO Guidance Risk Appetite Critical to Success
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CybersecurityFrameworks
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SOFTWARE SUPPLY CHAIN SECURITY THREAT LANDSCAPE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Windows forensic Commands
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Positionspapier Zero Trust 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Information Security Policy Template
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THREAT INTELLIGENCE REPORT – Shadow Syndicate: A Global Ransomware-as-a-Service Player?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
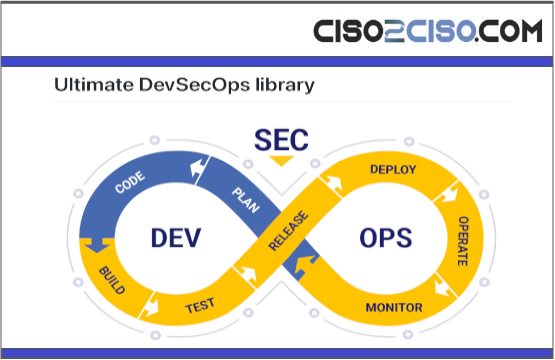
Ultimate DevSecOps library
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Common TTPsof attacks againstindustrial organizations. Implantsfor uploading data
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Threat Intel Roundup: DeadGlypH, T-Mobile, Juniper SRX, JetBrains TeamCity
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
STUXNET – TECHNIQUES USED REVIEW
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Art of Hiding in Windows
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Shodan Pentesting Guide – Delving deep into Shodan’s mine
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Reducing Cyber Risks for Industrial Control Systems (ICS) Professional Supplementary Document
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The ultimate Guide to Threat Profiling
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Guide to Security Operations
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Open Source Software Security Roadmap
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
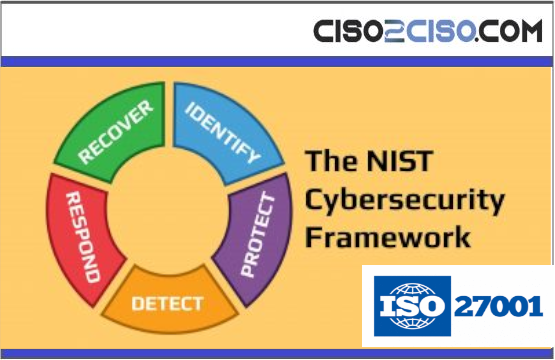
NIST Cybersecurity Framework (5 Core Functions)
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Spotlight Report – Cyber-attacks the apex of crime-as-a-service
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Network Security Best Practices
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Dark Web: Myths and Realities
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Malware Reverse Engineering Handbook
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2023 National Intelligence Strategy
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...