Source: www.securityweek.com – Author: Ionut Arghire Google has announced that BinDiff, a popular file comparison tool maintained by the company for more than a decade, is...
Day: September 27, 2023
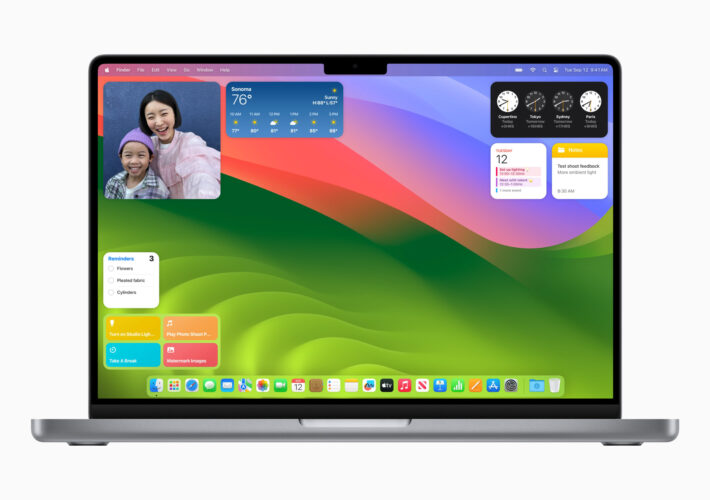
macOS 14 Sonoma Patches 60 Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Apple on Tuesday announced the release of macOS 14 Sonoma. A security advisory published by the tech giant shows that...
New GPU Side-Channel Attack Allows Malicious Websites to Steal Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Nearly all modern graphics processing units (GPUs) are vulnerable to a new type of side-channel attack that could be leveraged...
Microsoft Adding New Security Features to Windows 11 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Microsoft on Tuesday announced the new security features that will be available in the latest version of Windows 11. Windows...
Will Government Secure Open Source or Muck It Up? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Can open source software be regulated? Should it be regulated? And if so, will it lead...
Research From IANS and Artico Search Reveals Cybersecurity Budgets Increased Just 6% for 2022-2023 Cycle – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Boston, MA – September 26, 2023 – Today, IANS Research and Artico Search released their 2023 Security Budget Benchmark Report, an annual research study that...
Cyemptive Technologies Expands Operations in the Middle East and the Americas – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SNOHOMISH, Wash. (September 26, 2023) — Cyemptive Technologies, an award-winning provider of preemptive cybersecurity solutions for business and government, today announced international...
Catalyte Leverages Google Career Certificates to Expand Cybersecurity Apprenticeship Opportunities – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 BALTIMORE, Sept. 26, 2023 /PRNewswire-PRWeb/ — Catalyte is partnering to use Google’s Cybersecurity Certificate to prepare apprentices for a new career in the high-growth field...
Suspicious New Ransomware Group Claims Sony Hack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading A new threat actor is offering files purportedly stolen from Sony on the Dark Web, but...
Researchers Uncover RaaS Affiliate Distributing Multiple Ransomware Strains – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A new threat group is leveraging a relatively large network of malicious servers to distribute and...
Delinea Secret Server Introduces MFA Enforcement at Depth to Meet Cyber Insurance Requirements – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO, Sept. 26, 2023 /PRNewswire/ — Delinea, a leading provider of solutions that seamlessly extend Privileged Access Management (PAM), today announced an update...
Maine Department of Labor to Announce the Launch of University of Maine at Augusta Cybersecurity and IT Registered Apprenticeship Program – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 HOUSTON, Sept. 25, 2023 /PRNewswire/ — On September 28th from 1-3pm ET, the Maine Department of Labor (MDOL) and its Commissioner, Laura Fortman, will announce the launch...
HD Moore’s Discovery Journey – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer, Dark Reading For as long as he can remember it, HD Moore has loved discovering unexplored connections between...
Australian Government’s ‘Six Cyber Shields’ Is Potentially a Well-Meaning Skills Crisis – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Matthew Sainsbury The Australian government is displaying great interest and urgency in addressing the deficiencies in security and regulation that have led...
Identity Theft Protection Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Help protect your employees and customers from identity theft. This policy from TechRepublic Premium outlines precautions for reducing risk, signs to watch...
Quick Glossary: Malware – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Malware is an insidious infection that will steal productivity from your enterprise and potentially wreak havoc on your network. To prevent and...
Cyber-Attacks on Ukraine Surge 123%, But Success Rates Plummet – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Russian cyber-attacks against Ukraine skyrocketed in the first half of 2023, with 762 incidents observed by Ukraine’s State Service of Special...
Regulator Warns Breaches Can Cost Lives – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s privacy regulator has warned organizations handling the personally identifiable information (PII) of domestic abuse victims that data breaches could...
Attacks on European Financial Services Double in a Year – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cyber-attacks on European financial services firms more than doubled between Q2 2022 and Q2 2023, surging 119% in the period, according...
NCSC Launches Cyber Incident Exercise Scheme – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s National Cyber Security Centre (NCSC) has ramped up efforts to encourage firms to run incident response exercises, with a...
New ZenRAT Malware Targeting Windows Users via Fake Password Manager Software – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 27, 2023THNMalware / Cyber Threat A new malware strain called ZenRAT has emerged in the wild that’s distributed via bogus...
Critical libwebp Vulnerability Under Active Exploitation – Gets Maximum CVSS Score – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 27, 2023THNZero Day / Vulnerability Google has assigned a new CVE identifier for a critical security flaw in the libwebp...
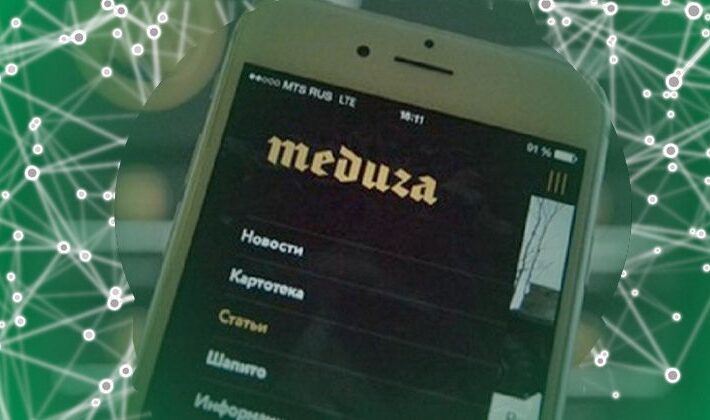
Exiled Russian journalist claims “European state” hacked her iPhone with Pegasus spyware – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The co-founder and publisher of Meduza, a news outlet outlawed in Russia for its independent reporting and stance on the...
Signal Will Leave the UK Rather Than Add a Backdoor – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Totally expected, but still good to hear: Onstage at TechCrunch Disrupt 2023, Meredith Whittaker, the president of the Signal Foundation,...
Xenomorph Android Banking Trojan Makes Landfall in US – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A sophisticated Android banking trojan that was first seen last year targeting banking apps in several European countries has made...
Cyber Week 2023 & The Israel National Cyber Directorate Presents – Embracing the Quantum Computing Revolution: Unleashing the Opportunities for Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/cyber-week-2023-the-israel-national-cyber-directorate-presents-embracing-the-quantum-computing-revolution-unleashing-the-opportunities-for-cybersecurity/ Category & Tags: CISO Suite,Governance, Risk &...
RagnarLocker Ransomware, LokiLocker Ransomware, and More: Hacker’s Playbook Threat Coverage Round-up: September 27th, 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach In this version of the Hacker’s Playbook Threat Coverage round-up, we are highlighting...
Exposing A Portfolio of Personally Identifiable Email Address Accounts from An E-Shop for Stolen Credit Card Details – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dancho Danchev collinsescober[.]yahoo.com kerrybarness[.]gmail.com wolk48[.]bk.ru bosssss[.]bossy.cc smokinwetmarley[.]gmail.com elenakrasotka[.]gmx.com roger.moon[.]post.com frr[.]frr.ru varmer1982[.]gmail.com r0[.]r0.ru micheal1717[.]yahoo.com karlsonas[.]safe-mail.net elhenawy5[.]yahoo.com naemnik1777[.]qip.ru erwinfontilla[.]yahoo.com makteejay112[.]yahoo.com darkman135[.]gmail.com elisasuiter[.]yahoo.com lob[.]ya.ru suetrel93[.]gmail.com...
3 Key Telltales That Unmask the Reach of SMS Fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Luke Stork The cyberattack known as SMS toll fraud, or SMS traffic pumping, has officially become a big problem for many businesses...
Can You Recognize This Guy? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dancho Danchev Dear blog readers, There was a speculation approximately a decade ago that I went missing. Can you recognize this guy...