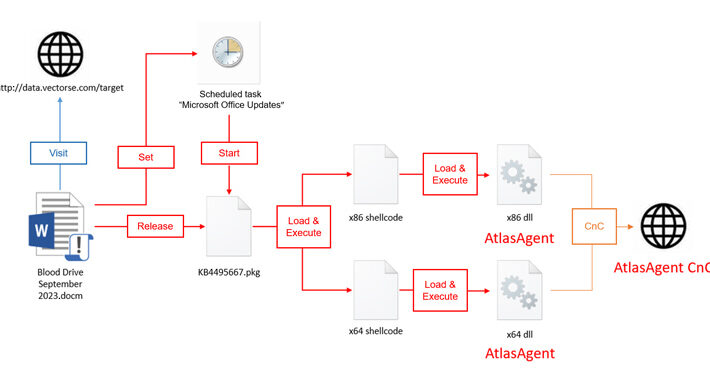
Source: thehackernews.com – Author: . Sep 27, 2023THNMalware / Cyber Attack A new threat actor known as AtlasCross has been observed leveraging Red Cross-themed phishing lures...
Day: September 27, 2023
Researchers Uncover New GPU Side-Channel Vulnerability Leaking Sensitive Data – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 27, 2023THNVulnerability / Endpoint Security A novel side-channel attack called GPU.zip renders virtually all modern graphics processing units (GPU) vulnerable...
New Survey Uncovers How Companies Are Confronting Data Security Challenges Head-On – Source:thehackernews.com
Source: thehackernews.com – Author: . Data security is in the headlines often, and it’s almost never for a positive reason. Major breaches, new ways to hack...
Predicting the next wave of emerging threats in neobank security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Tamas Kadar, CEO of SEON, shares his expert insights into what neobanks need to look out for when it comes to...
Must-know insights when navigating the CISO career path – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: The CISO career path is as exciting as it is fraught with perils. Modern CISOs reside at the intersection...
Breaking News Q&A: What Cisco’s $28 billion buyout of Splunk foretells about cybersecurity – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido There’s a tiny bit more to Cisco’s acquisition of Splunk than just a lumbering hardware giant striving...
Sony`s Systems Breached. Ransomed.vc Claims Stealing 260 GB of Data – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Ransomed.vc threat group claims they`re responsible for an alleged Sony data breach and attempt to sell the stolen data on...
Phobos Ransomware: Everything You Need to Know and More – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Alina Georgiana Petcu In the ever-evolving landscape of cyber threats, ransomware remains a pervasive and destructive weapon in the arsenal of cybercriminals....
QR codes in email phishing – Source: securelist.com
Source: securelist.com – Author: Roman Dedenok QR codes are everywhere: you can see them on posters and leaflets, ATM screens, price tags and merchandise, historical buildings...
Microsoft now rolling out AI-powered Paint Cocreator to Insiders – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft’s new AI image generation Paint tool powered by OpenAI’s DALL-E text-to-image model is now rolling out to Windows Insiders...
US and Japan warn of Chinese hackers backdooring Cisco routers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas US and Japanese law enforcement and cybersecurity agencies warn of the Chinese ‘BlackTech’ hackers breaching network devices to install custom...
Modern GPUs vulnerable to new GPU.zip side-channel attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Researchers from four American universities have developed a new GPU side-channel attack that leverages data compression to leak sensitive visual...
GitHub repos bombarded by info-stealing commits masked as Dependabot – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers are breaching GitHub accounts and inserting malicious code disguised as Dependabot contributions to steal authentication secrets and passwords from...
Simple Membership Plugin Flaws Expose WordPress Sites – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Two new security flaws in the popular Simple Membership plugin for WordPress, affecting versions 4.3.4 and below, have been identified, leading...
Ransomed.vc Group Hits NTT Docomo After Sony Breach Claims – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 In a recent development following the recent data leak from Sony, the notorious ransomware syndicate Ransomed.vc has targeted Japan’s largest telecommunication...
BEC Attacks Increase By 279% in Healthcare – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Business Email Compromise (BEC) attacks in the healthcare sector have seen a 279% increase this year, shows a new report published by...
Watch out! CVE-2023-5129 in libwebp library affects millions applications – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Watch out! CVE-2023-5129 in libwebp library affects millions applications Pierluigi Paganini September 27, 2023 Google assigned a maximum score to...
DarkBeam leaks billions of email and password combinations – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini DarkBeam leaks billions of email and password combinations Pierluigi Paganini September 27, 2023 DarkBeam left an Elasticsearch and Kibana interface...
‘Ransomed.vc’ in the Spotlight – What is Known About the Ransomware Group Targeting Sony and NTT Docomo – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini ‘Ransomed.vc’ in the Spotlight – What is Known About the Ransomware Group Targeting Sony and NTT Docomo Pierluigi Paganini September...
Top 5 Problems Solved by Data Lineage – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Top 5 Problems Solved by Data Lineage Pierluigi Paganini September 27, 2023 Data lineage is the visualization and tracking of...
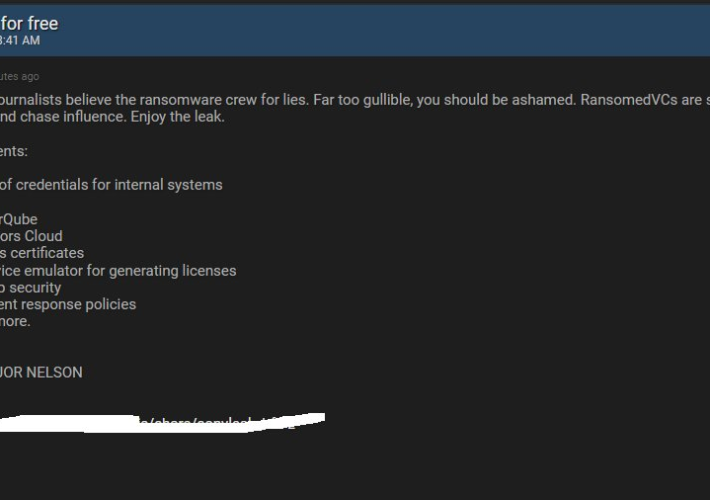
Threat actors claim the hack of Sony, and the company investigates – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors claim the hack of Sony, and the company investigates Pierluigi Paganini September 26, 2023 Sony launched an investigation...
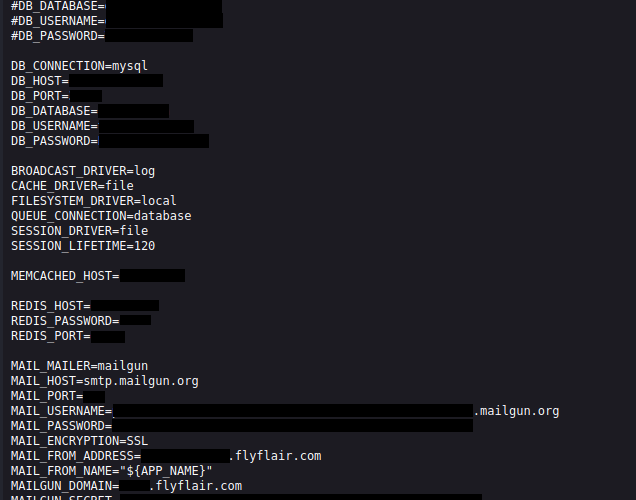
Canadian Flair Airlines left user data leaking for months – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Canadian Flair Airlines left user data leaking for months Pierluigi Paganini September 26, 2023 Researchers discovered that Canadian Flair Airlines...
Sony Investigating Potential Data Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime 2 Online Threat Actors Claim Responsibility David Perera (@daveperera) • September 26, 2023 ...
US, South Korea Pledge Strengthened Tech Collaboration – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Geo Focus: Asia , Geo-Specific Officials Discuss Governance for AI, 5G, Cloud Computing Rashmi Ramesh...
Xenomorph Android Malware Campaign Targets US Banks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Malware as-a-Service , Social Engineering Enhanced Malware Exerts Even More Control Over Mobile Devices Prajeet Nair...
CISA Urges Americans to Apply MFA, ‘Think Before They Click’ – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Multi-factor & Risk-based Authentication , Security Operations Director Jen Easterly: Password Managers, Automatic Software Updates Key to Defense Michael Novinson (MichaelNovinson)...
Gem Security Lands $23 Million Series A Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Gem Security, an Israeli startup with operations in New York, has attracted $23 million in venture capital investment to build...
Misconfigured TeslaMate Instances Put Tesla Car Owners at Risk – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Misconfigured TeslaMate instances can leak tons of data on the internet, potentially exposing Tesla cars and their drivers to malicious...
Firefox 118 Patches High-Severity Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Mozilla on Tuesday announced security updates for both Firefox and Thunderbird, addressing a total of nine vulnerabilities in its products,...
Stolen GitHub Credentials Used to Push Fake Dependabot Commits – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat actors have been observed pushing fake Dependabot contributions to hundreds of GitHub repositories in an effort to inject malicious...