Source: www.darkreading.com – Author: 1 SEATTLE (BUSINESS WIRE) ‒ Critical Insight, the Cybersecurity-as-a-Service provider specializing in helping critical organizations Prepare, Detect, and Respond in today’s threat environment, today...
Day: August 25, 2023
Black Hat USA 2023 Closes on Record-Breaking Event in Las Vega – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO — (BUSINESS WIRE) — Black Hat, the producer of the cybersecurity industry’s most established and in-depth security events, today...
Cypago Raises $13M and Unveils its Cyber GRC Automation (CGA) Platform to Simplify GRC Processes – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 [Tel Aviv, 24th August, 2023] – Cypago announced the release of its Cyber GRC Automation (CGA) platform today, revolutionizing the GRC space by...
Kyndryl and Cisco Expand Partnership Focusing on Cyber Resilience – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 NEW YORK, August 24, 2023 — Kyndryl (NYSE: KD), the world’s largest IT infrastructure services provider, today announced an expanded technology partnership with...
US Space Industry More Prone to Foreign Espionage, US Agencies Warn – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading In coordination with the FBI, the National Counterintelligence and Security Center (NCSC), and the Air Force Office...
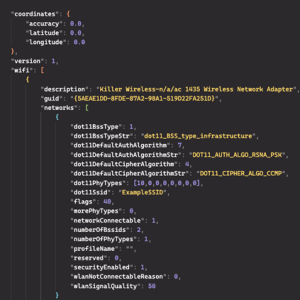
Major US Energy Company Hit by QR Code Phishing Campaign – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet This QR code phishing campaign is targeting multiple industries and using legitimate services such as Microsoft Bing to increase its...
Google AI in Workspace Adds New Zero-Trust and Digital Sovereignty Controls – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Urupong/Adobe Stock At a Google Cloud press event on Tuesday, the company announced Google Cloud’s rollout over the course...
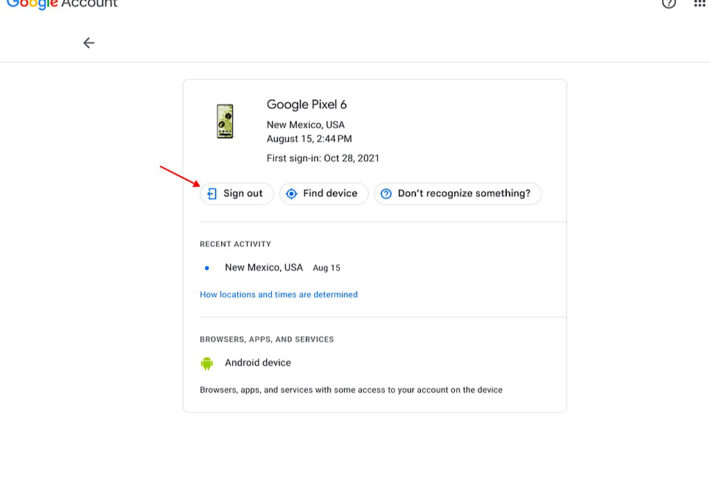
How to Remove a Lost Device From Your Google Account – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Andy Wolber on August 24, 2023, 9:48 AM EDT How to Remove a Lost Device From Your Google Account Follow this guide...
How Does XDR Software Help Security Teams – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși XDR software collects and processes data from various security layers, networks, and endpoints in an organization`s IT environment. It is...
What Is a Host Intrusion Detection System (HIDS) and How It Works – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Dora Tudor HIDS stands for host-based intrusion detection system and is an application that monitors a computer or network for suspicious activities....
How AI turbocharges your threat hunting game – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Over 90 percent of organizations consider threat hunting a challenge. More specifically, seventy-one percent say that both prioritizing alerts...
FBI warns of patched Barracuda ESG appliances still being hacked – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The Federal Bureau of Investigation warned that patches for a critical Barracuda Email Security Gateway (ESG) remote command injection flaw...
Ransomware hackers dwell time drops to 5 days, RDP still widely used – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Ransomware threat actors are spending less time on compromised networks before security solutions sound the alarm. In the first half of...
Jupiter X Core WordPress plugin could let hackers hijack sites – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Two vulnerabilities affecting some version of Jupiter X Core, a premium plugin for setting up WordPress and WooCommerce websites, allow...
Privacy Regulator Warns of Surge in “Text Pest” Cases – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s data protection watchdog is urging victims of so-called “text pests” to come forward after revealing that nearly a third...
Researchers Discover Reply URL Takeover Issue in Azure – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers are urging Azure Active Directory (AD) users to monitor for abandoned reply URLs after revealing a critical vulnerability in...
FBI: Barracuda Appliances Still Being Exploited By China – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The FBI has urged users of affected Barracuda appliances to replace them immediately, after warning that they’re still being targeted by...
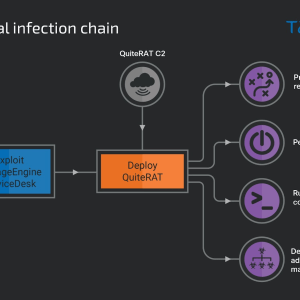
Lazarus Group Targets Internet Infrastructure and Healthcare with ‘QuiteRAT’ Malware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The North Korean state-sponsored actor Lazarus Group recently started a new campaign targeting internet backbone infrastructure and healthcare entities in Europe...
Creative QakBot Attack Tactics Challenge Security Defenses – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 QukBot was one of the most active malware families in Q2 of 2023, according to the latest HP Wolf Threat Insights...
Whiffy Recon malware triangulates the position of infected systems via Wi-Fi – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts observed the SmokeLoader malware delivering a new Wi-Fi scanning malware strain dubbed Whiffy Recon. Secureworks Counter Threat Unit (CTU) researchers...
FBI: Patches for Barracuda ESG Zero-Day CVE-2023-2868 are ineffective – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The FBI warned that patches for a critical Barracuda ESG flaw CVE-2023-2868 are “ineffective” and patched appliances are still being...
Researchers released PoC exploit for Ivanti Sentry flaw CVE-2023-38035 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Proof-of-concept exploit code for critical Ivanti Sentry authentication bypass flaw CVE-2023-38035 has been released. Researchers released a proof-of-concept (PoC) exploit...
Lazarus APT exploits Zoho ManageEngine flaw to target an Internet backbone infrastructure provider – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The North Korea-linked Lazarus group exploits a critical flaw in Zoho ManageEngine ServiceDesk Plus to deliver the QuiteRAT malware. The...
Urgent FBI Warning: Barracuda Email Gateways Vulnerable Despite Recent Patches – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 25, 2023THNEmail Security / Vulnerability The U.S. Federal Bureau of Investigation (FBI) is warning that Barracuda Networks Email Security Gateway...
Parmesan Anti-Forgery Protection – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Ted • August 24, 2023 8:01 AM Will the real Parmigiano Reggiano please stand up? https://p-chip.com With a...
Too good to be true? That online auction price could be triangulation fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
Hacker in Residence, on Black Hat USA 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jason Kent Attending many of the HackerSummerCamp activities involves attending a bunch of small meetups and social gatherings. Much of my peer...
Do we really need another cybersecurity tool? – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach Research shows many companies now own and operate more than 60 disparate security tools, yet breaches continue to make headlines. Throwing...
BSidesTLV 2023 – Keren Elazari BSidesTLV 2023: Closing Words – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
Deepfactor 3.3 Includes Enhanced Prioritization of SCA Findings and New Free-Trial Offer – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepfactor Deepfactor Release 3.3 Overview In Release 3.3 of Deepfactor Developer Security, we have made significant enhancements to the platform’s artifact scanner...