Source: www.techrepublic.com – Author: Cedric Pernet
This QR code phishing campaign is targeting multiple industries and using legitimate services such as Microsoft Bing to increase its efficiency and bypass security.

Cofense, a U.S.-based email security company, released a new report about a massive QR code phishing campaign that targets numerous industries. The campaign has especially focused on one major U.S.-based energy company, though Cofense doesn’t name which one. Cybercriminals are using legitimate services such as Microsoft Bing to increase this campaign’s efficiency and bypass security. Fortunately, there are steps companies can take to mitigate this particularly unusual phishing threat.
Jump to:
- How does this QR code phishing campaign work?
- Which legitimate services are abused in this phishing attack?
- Which industries are at risk of this phishing attack?
- Why this phishing attack is unusual
- How to protect from this QR code phishing threat
How does this QR code phishing campaign work?
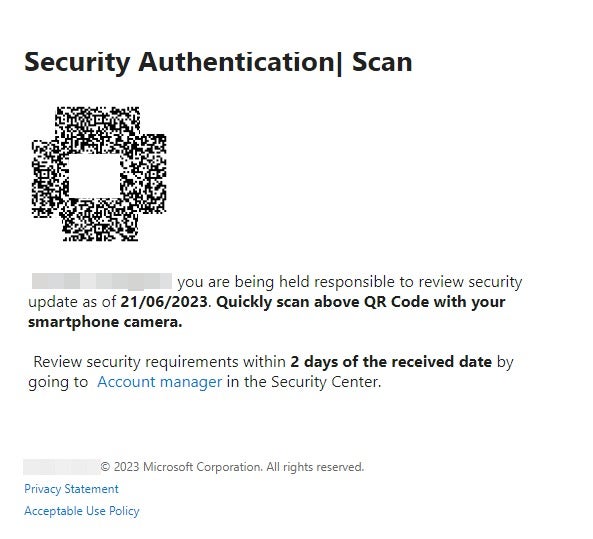
This campaign leverages QR codes as PNG images, which, once scanned, lead to Microsoft credential phishing pages. The email content uses different but similar lures: making the user believe they need to update their account security or activate two-factor authentication/multi-factor authentication within 72 hours (Figure A).
Figure A
Which legitimate services are abused in this phishing attack?
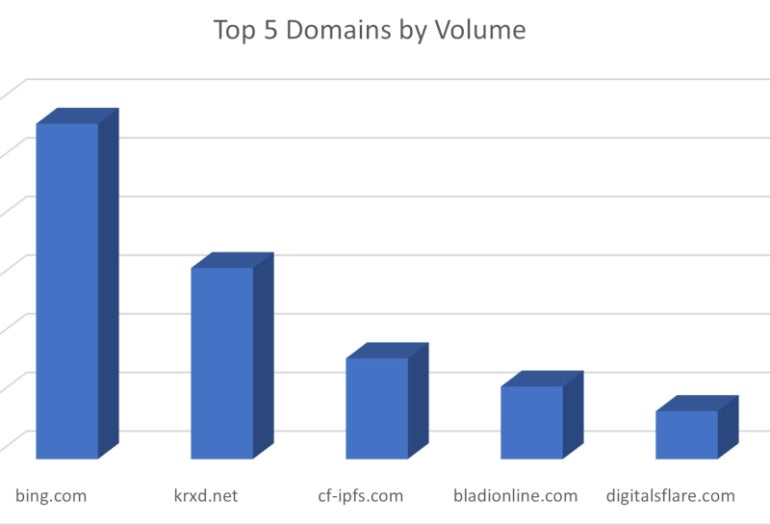
The legitimate services that are abused to improve the efficiency of this phishing attack are Microsoft Bing, Salesforce via a domain (i.e., krdx.net) that belongs to the company and was used for redirection, two legitimate websites (i.e., digitalsflare.com and bladionline.com) and the InterPlanetary File System.
Bing
In this phishing campaign, most of the malicious QR codes included Bing redirections that contained the victim’s email and a Base64-encoded phishing link (Figure B).
Figure B
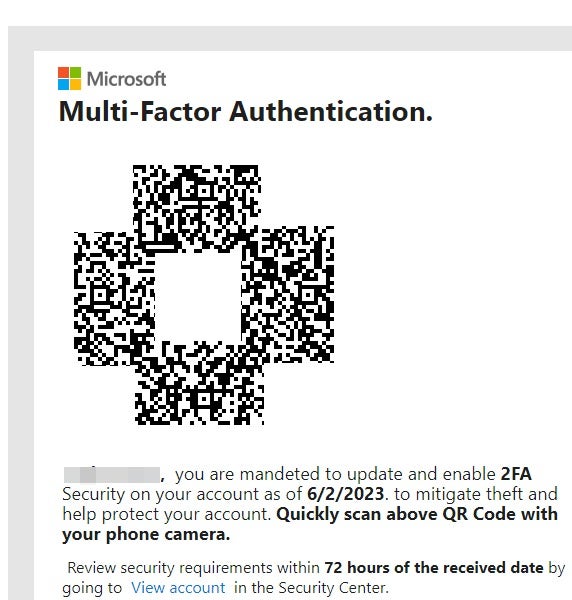
In this case, cybercriminals used Bing — a legitimate Microsoft domain with redirection functionalities that were implemented for marketing purposes — to redirect users to a phishing website they control. Just like with the QR code, the benefit of this redirection method is to help bypass security because no malicious domain is directly exposed — the malicious domain is Base64-encoded.
IPFS
The cybercriminals used the InterPlanetary File System to host phishing content and sent phishing links that used CloudFlare’s gateway to the IPFS system (Figure C).
Figure C
Which industries are at risk of this phishing attack?
The phishing campaign heavily focused on one major U.S.-based energy company, followed by the manufacturing, insurance, technology, financial services and healthcare industries (Figure D).
Figure D
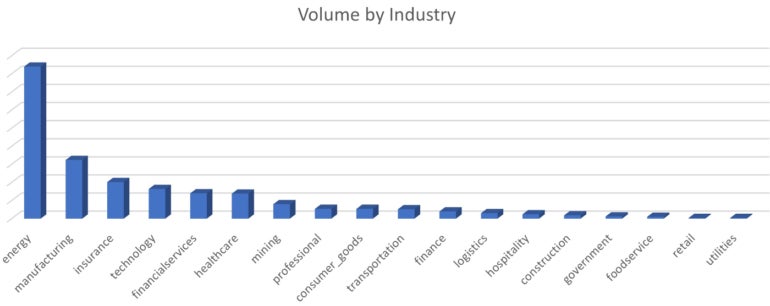
Cofense’s Nathaniel Raymond reports that, from the beginning of the campaign in May 2023, the average month-to-month growth percentage has been more than 270%. Since May 2023, there has been an increase in QR codes in emails of more than 2,400%.
Why this phishing attack is unusual
QR codes are not often used in phishing campaigns; cybercriminals tend to use them more in day-to-day life, leaving QR codes in different places so curious people will scan them and possibly get scammed or infected by malware.
There is at least one benefit for cybercriminals to use QR codes in emails, especially for launching phishing campaigns: There are a lot more chances to bypass security and land in the user’s mailboxes because the phishing link is hiding inside the QR image.
How this phishing campaign could fail
As stated by Raymond, “although QR codes are advantageous for getting malicious emails into user’s inbox, they may fall short of being efficient in getting the user to the phish.”
QR codes need a scanning device to be used, which in most cases will be a mobile phone, as those devices now usually embed a QR code scanner that works with their camera. Additionally, those mobile phone scanners generally show the link contained in the QR code to the user, who decides if he/she clicks on it or not.
How to protect from this QR code phishing threat
To enhance email security and protect themselves from the QR code threat, organizations should follow these steps.
- Consider implementing advanced threat protection solutions. Ideally, those solutions should resolve the QR code and have the link analyzed by security solutions.
- On mobile devices, only allow QR codes to be opened by security applications such as antivirus that include QR code scanning as a feature. Then, the QR code link should be checked for safety.
- Educate users so they’re aware of the risks associated with QR codes. In companies where no QR code is used, employees should never scan any QR code from any source that pretends to come from the organization.
- Provide users with a quick way to report suspicious emails to your IT or security department. This could be a button in their email client software.
- Deploy multifactor authentication for the company’s email accounts. Even if the phishing is successful, the attacker will still not be able to log into the email account.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
Original Post URL: https://www.techrepublic.com/article/major-us-energy-company-hit-by-qr-code-phishing-campaign/
Category & Tags: Microsoft,Security,cybersecurity,microsoft bing,phishing,qr codes – Microsoft,Security,cybersecurity,microsoft bing,phishing,qr codes




















































