Source: www.infosecurity-magazine.com – Author: 1 The US Department of Justice (DoJ) is doubling the size of the team investigating cryptocurrency crime, with the fight against ransomware...
Day: July 21, 2023
Plurilock Launches Generative AI ‘Guardrails’ Product for Workforces – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Generative AI tools have conquered the workplace, especially large language model-based (LLM) chatbots like OpenAI’s ChatGPT and Google’s Bard. These powerful...
Russian Prosecutor Asks for 18 Years in Jail for Group-IB Founder – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Russian state prosecution asked the Moscow City Court to impose 18 years in a strict colony regime on Ilya Sachkov,...
Chinese Hackers Breached Ambassador’s Email – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A Chinese cyber-espionage campaign revealed by Microsoft last week compromised the government email account of the US ambassador to China and...
Clop Drives Record Ransomware Activity in June – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Ransomware attacks in June soared 221% year-on-year to hit a record 434 for the month, according to an analysis from NCC...
GitHub Warns Devs of North Korean Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 GitHub has warned of a new North Korean threat campaign designed to compromise victims via malicious npm package dependencies. The development...
Europol’s IOCTA 2023 Report Reveals Cybercriminals are Increasingly Interdependent – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet Image: SomYuZu/Adobe Stock The Europol report reported on cybercriminals’ use of cryptocurrencies and how their techniques are more sophisticated. However,...
8 Best Enterprise Password Managers for 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke LastPass: Best overall 1Password: Best for a single-user account BitWarden: Best for free password management ManageEngine Password Manager Pro: Best...
How to Access Your iPhone if You Forget Your Passcode – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Lance Whitney There are ways to unlock your iPhone even without the right passcode, but you’ll need a PC with iTunes or...
Intrusion Detection Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: All modern enterprises must accept the fact that at some point their systems or networks will very likely experience an unauthorized intrusion...
Mallox Ransomware Witnessing Alarming Surge in Activity – Source: heimdalsecurity.com
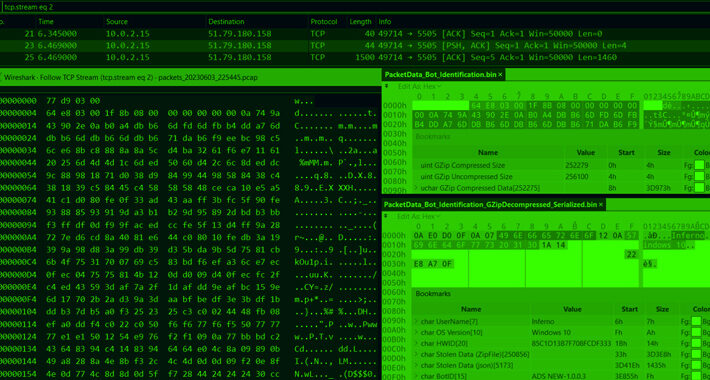
Source: heimdalsecurity.com – Author: Mihaela Marian The Mallox ransomware group, also known as TargetCompany, Fargo, and Tohnichi, has become increasingly active, signaling a significant shift in...
New Severe Vulnerabilities Found in AMI MegaRAC BMC Software – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Security Researchers warn about finding new vulnerabilities in the AMI MegaRAC Baseboard Management Controller (BMC) software. The flaws, rated from...
Critical Zyxel Firewall Vulnerability Exploited in DDOS Attacks – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian Multiple DDoS botnets have actively exploited a critical vulnerability discovered in Zyxel firewall models, as revealed by cybersecurity researchers. Tracked...
Why Removing Admin Rights Closes Critical Vulnerabilities in Your Organization – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian You have surely heard before about admin rights. This article will shed some light on what are admin rights, what...
Sophisticated BundleBot Malware Disguised as Google AI Chatbot and Utilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 21, 2023THNCyber Threat / Malware A new malware strain known as BundleBot has been stealthily operating under the radar by...
Local Governments Targeted for Ransomware – How to Prevent Falling Victim – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 21, 2023The Hacker NewsPassword Security / Cybersecurity Regardless of the country, local government is essential in most citizens’ lives. It...
DDoS Botnets Hijacking Zyxel Devices to Launch Devastating Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 21, 2023THNVulnerability / Botnet Several distributed denial-of-service (DDoS) botnets have been observed exploiting a critical flaw in Zyxel devices that...
Citrix NetScaler ADC and Gateway Devices Under Attack: CISA Urges Immediate Action – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 21, 2023THNVulnerability / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory on Thursday warning that...
VirusTotal apologizes for data leak affecting 5,600 customers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan VirusTotal apologized on Friday for leaking the information of over 5,600 customers after an employee mistakenly uploaded a CSV file...
GitHub warns of Lazarus hackers targeting devs with malicious projects – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams GitHub is warning of a social engineering campaign targeting the accounts of developers in the blockchain, cryptocurrency, online gambling, and...
Critical AMI MegaRAC bugs can let hackers brick vulnerable servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Bing Image Creator Two new critical severity vulnerabilities have been discovered in the MegaRAC Baseboard Management Controller (BMC) software...
Google Chrome gets Windows 11’s new design – how to enable it – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google’s Chrome 115 has a new feature that allows users to use Windows Mica material, a design element that enhances user...
North Korean Attackers Targeted Crypto Companies in JumpCloud Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Researchers have attributed the recent JumpCloud breach to a branch of North Korea’s Lazarus Group. Early indications...
TrustArc Announces TRUSTe EU-US Data Privacy Framework Verification – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO, July 20, 2023 /PRNewswire/ — On July 10, 2023, the European Commission announced the official adoption of its adequacy decision for the EU-U.S. Data Privacy Framework...
Deloitte Global Expands MXDR Cybersecurity SaaS Solution With Operational Technology and Identity Modules – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 NEW YORK, July 20, 2023 /PRNewswire/ — Deloitte, a leader in global security services and incident response services, has expanded their Managed Extended Detection...
Mallox Ransomware Group Activity Shifts Into High Gear – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A ransomware actor with a penchant for breaking into target networks via vulnerable SQL servers has...
Critical Infrastructure Workers Better At Spotting Phishing – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Phishing simulation training for employees appears to work better at critical infrastructure organizations than it does across...
Kevin Mandia Brings the HammerCon – Source: www.darkreading.com
Source: www.darkreading.com – Author: Edge Editors, Dark Reading HammerCon is a gathering of US military cyber professionals organized by the Military Cyber Professionals Association. One of...
Estée Lauder Breached in Twin MOVEit Hacks, by Different Ransom Groups – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Both the Cl0p and BlackCat ransomware gangs posted messages bragging about breaching Estée Lauder by way of the...
Apache OpenMeetings Wide Open to Account Takeover, Code Execution – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Three separate security vulnerabilities in the Apache OpenMeetings open source Web conferencing application can be strung together...