Source: heimdalsecurity.com – Author: Mihaela Marian
You have surely heard before about admin rights. This article will shed some light on what are admin rights, what risks they pose to an organization’s security, the benefits of removing admin rights for your organization, best practices on admin rights management, and of course, how to remove local admin rights with our solution.
This is not about removing admin rights forever, for everyone but yourself, but rather about making the removal of admin rights the default setting in your organizational network. After making sure every employee but a few system administrators have a user profile instead of an admin one, the administrative rights should be managed on a case-by-case basis.
What Are Admin Rights?
Admin rights are the highest permission levels that a computer user can receive. An admin user is also called a privileged user and can get access to all network and system areas to which they have been granted admin rights. To give some examples, a user with admin rights can delete system or network files, install various software or even hardware drivers, perform system settings changes or they can carry on system updates deployment.
Why Removing Admin Rights Is Important?
Unmanaged administrator rights pose a high-security risk for any company. By simply removing the admin rights, you can block the entrance and limit the spread of many forms of malware. The overall impact of any external or internal threats is considerably reduced. Removing admin privileges from your organization is the immediately effective, most powerful protective measure you can take.
1. Removing Admin Rights to Neutralize Insider Threats
You may already be familiar with the concept of neutralizing insider threats by managing admin rights.
First of all, as a disclaimer, you should know that removing admin rights for regular users inside your organization doesn’t completely eliminate risks associated with insider threats. You can’t control every dangerous action a user might be doing, just by de-escalating their administrative rights on the endpoint.
There are still plenty of risky things which an employee can do, both intentionally and unintentionally, even without admin privileges. These include:
- Setting a weak password or a password they also use for other personal accounts;
- Sharing their password with others, who might be targeting the employee for malicious purposes;
- Clicking unsafe links from emails or the web;
- Giving protected information to malicious third parties, because of a scam (like CEO fraud) or intentionally;
- Snooping through the files on a colleague’s workstation when they leave it unattended (risky especially if the colleague has access to more sensitive data than they do);
- Inserting an infected USB stick or external hard drive into a workstation.
Still, removing admin rights by default is often a bare minimum for reducing insider threat considerably. While not a lot of people know that removing admin rights still doesn’t prevent all insider threat risks, almost everyone knows it’s a good thing to do, security-wise.
So why then do some organizations still allow default administrative rights to their users? Because they are still succumbing to some dangerous myths about admin privileges:
- Only employees who hate us could cause harm and we get along well with all employees;
- We have anti-virus and a firewall installed so we’re fine, there’s no harm they could do;
- If admins need to approve all requests they will lose a ton of time;
I have to admit that there may be a grain of truth in some of the myths above, but not in the way people who buy into these myths may think. For example, it does indeed help to have an anti-virus solution and firewall installed, but it’s not enough.
Also, it is true that admins lose a bit of time approving admin rights requests but that’s nothing compared to the risk they help avoid and, more importantly, the time waste can be completely avoided by using an admin rights management software, like our Privileged Access Management.
2. Removing Admin Rights to Neutralize External Threats and Close Vulnerabilities
Few people know this, but removing admin rights and granting them only upon request and within a specific time frame can help close external threats too. It’s not just about managing insider threats. It’s also about closing security gaps which are often found in common B2B software, operating systems, and so on.
Besides classic insider threat scenarios, there are also system vulnerabilities that can be easily abused from a fully-privileged account. Such systemic vulnerabilities are often discovered and patched without a breach having to happen for security researchers to become aware of the threat. But other times, unfortunately, the vulnerabilities are discovered by hackers and exploited before they can be patched up.
So, what can you do to avoid your company becoming the next newsworthy example of a breach?
Since risk is inevitable, the only way to mitigate it is to remove admin privileges for regular users and only grant them upon request and for a limited time frame.
Risks of Granting Admin Rights to Everyone
Here are just some of the risks derived from granting everyone admin privileges. As you’ll see, a user can do even more harm to your organization if they do have access to full administrative rights. Such things include:
- Installing malicious apps like spyware or malware meant to steal money, data, or disrupt activities;
- Creating back-doors for third parties to install malicious apps or to hijack the systems;
- Access or export sensitive data which can then be further mishandled;
- Creating changes to lock legitimate users out of the systems;
- Publishing misleading or embarrassing content in order to cause a PR crisis etc.
Of course, this doesn’t mean that the user would willingly do all of these things, but it’s something that hackers could accomplish by tricking a user with admin privileges. The trick could be accomplished by almost anything – a spam email, a USB stick which the hackers replaced with one of their own, and so on.
Privilege Misuse Statistics
According to a report by Centrify, where 150 IT decision-makers across the U.S. were surveyed, here are some statistics referring to the period between May 2020 and May 2021 on how privileged accounts became popular targets for hackers:
- 52% of organizations were targets of insider threats;
- 53% suffered privileged credentials theft;
- In 85% of the cases where privileged credentials were stolen, the hackers could gain access to critical data;
- 66% of insider threats resulted eventually in admin privilege abuse;
- 48% of organizations that gave too many privileges to a contractor or employee experienced a data breach;
- IT administrator accounts were the most targeted by threat actors.
I could go on, but I think you have a better picture now of what happens when administrative rights are mishandled. You can probably see news of data breaches pop up in the news all the time, but while you learn the tech details and methods used by hackers (DNS hijacking, a Trojan, good old malware, etc.), you rarely hear how it all began and how the hackers gained access in the first place: through abusing an account with administrative privileges.
Best Practices for Managing Admin Rights Securely
Here are a few best practices for managing your admin rights safely and in the most productive way for both your users and your system administrators.
#1. Nurture an environment of ‘least privileges’ possible
Important: Please note that we encourage you to create a security stance of ‘least privileges’, but not necessarily a company culture of ‘need to know basis’. Internal transparency makes employees see beyond their own little grid, understand the purpose of their individual tasks and contribute toward the end goals more effectively. So, except the cases where you are dealing with really sensitive info, don’t fall into the trap of creating a company culture based on secrecy or your overall productivity will drop.
#2. Automate the escalation and de-escalation of admin privileges
Automation is by far the most effective way to escalate and de-escalate admin privileges for all endpoint users within the organization, without occupying most of the sys-admins time with these tasks.
A reliable admin rights management software, such as our Privileged Access Management, not only automates the process of requesting and granting admin rights, but it also automatically de-escalates the admin rights if the endpoint is compromised (when used together with Heimdal Next-Gen Antivirus).
#3. Make sure administrators follow up on each case unless de-escalation is automated
If you’re going to stick to the manual work for escalating and de-escalating admin rights, at least make sure that whenever admin rights privileges are granted to a user, the admins then follow up to deescalate the rights shortly.
The recommended time window is 5 to 15 minutes since that’s enough for the user to install whatever software they need. We also recommend that the system administrator oversees exactly the software that will be installed, because since the admin rights management is not automated there is the risk of unwittingly installing a corrupted file.
#4. Make sure there are procedures in store for endpoint quarantine
What happens if an account gets breached by an insider threat? Can you ensure that there’s no way that account can perform any actions which could have consequences for the security of your company?
Make sure your internal policy and technical safety measures allow your system admins to deescalate any privileges fast and further quarantine the compromised endpoint. Of course, an automated admin rights management software can do that faster and more effectively, but it’s not impossible to be done manually either.
#5. Make sure the super-user accounts are also secured
By super-user accounts I mean the accounts of system administrators who have the privileges to install any software, access any data, escalate or de-escalate the admin rights of other users, and so on.
While it’s important to have one or more system administrators manage the rights of the other users in the organization securely, you must set in place procedures for securing their accounts as well. In the event that one of the admins has their own account hacked, how well will your organization be able to handle the crisis?
The best way to go about it is to talk with your CTO and sys-admins about establishing a crisis management procedure especially for this kind of scenario. Include priorities such as making the activity of system admins transparent for other system admins, allowing the system to trace back their steps (leave breadcrumbs) for accountability, preventing administrative tasks from being done remotely, and allowing the other admins to de-escalate the compromised admin account fast in case of a breach.
System admins waste 30% of their time manually managing user
rights or installations
Heimdal® Privileged Access
Management
Is the automatic PAM solution that makes everything
easier.
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
How to Remove Local Admin Rights with Heimdal® Privileged Access Management
If you’re currently offering admin privileges to all users or some users within your organization, go review the status of these rights ASAP. Create a map of user admin privileges and a procedure for granting them.
Now I’m going to show you how you can remove local admin rights using our Privileged Access Management solution. Here we go:
- Go to your Heimdal Dashboard
- Choose Endpoint Settings
- Click on the policy you want to update
- Choose the Privileged and Access Management tab

- Check Revoke existing local admin rights.
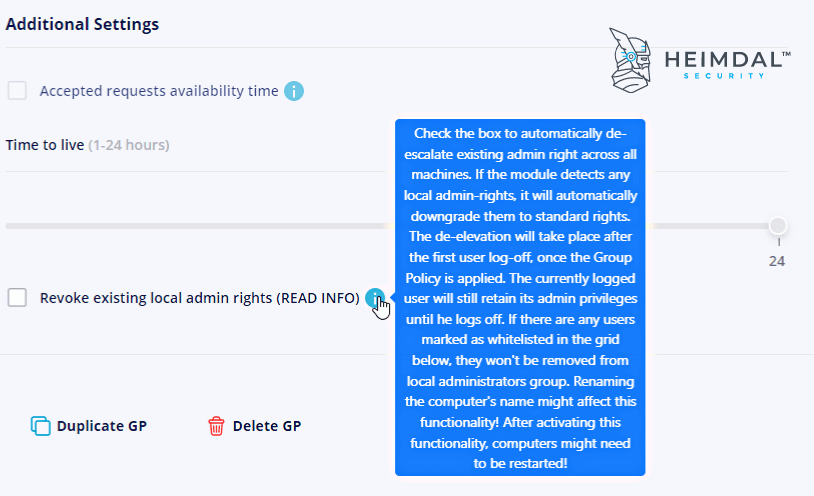
This option lets you reduce both local and domain users, the two categories of privileged users called administrators, to standard users. What the Heimdal Agent does is to take a snapshot that contains the local Administrators’ Group found on every endpoint and then erase all the group members. The one that will not be removed will be the default Administrator user. By ticking this option, all the users in that group will have standard permissions.
Until the first logoff/reboot happens, the logged users will keep the admin rights. When speaking of domain-joined computers, however, you should know the local Administrators’ Group members can be set to standard permissions only if the endpoint shares a communication with the domain controller. If you disable this option, you can add back the local Admin Group members to the service stop.
Update the policy and you’re ready to go. If you have multiple policies and you don’t want to take them one by one, you can use the Global Option to activate this feature.
Wrapping It Up
Removing admin privileges is but a first step to getting more secure, but it’s an essential one. As long as you do it ASAP and create a coherent internal policy for admin rights escalation, you’re definitely on the right track!
Stay up to date with the latest threats and practices (for example, by checking back here and reading our blog). Make sure the rest of your cybersecurity system is ready for any challenge by setting up a multi-layered approach.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, or YouTube, to keep up to date with everything we post!
This article was initially drafted by Miriam Cihodariu.
Original Post URL: https://heimdalsecurity.com/blog/why-removing-admin-rights-closes-critical-vulnerabilities-in-your-organization/
Category & Tags: Access Management,Endpoint security,Vulnerability,admin rights,PAM,privileged access management – Access Management,Endpoint security,Vulnerability,admin rights,PAM,privileged access management