Source: heimdalsecurity.com – Author: Mihaela Marian
The Mallox ransomware group, also known as TargetCompany, Fargo, and Tohnichi, has become increasingly active, signaling a significant shift in its operations. According to recent findings, Mallox’s ransomware activities in 2023 have seen a staggering 174% increase compared to the previous year.
Researchers` Findings
Security researchers from Palo Alto Networks Unit 42, reported that Mallox, like other ransomware actors, is adopting the double extortion tactic. They steal sensitive data from breached organizations before encrypting their files and then threaten to leak the stolen data on a leak site to coerce victims into paying the ransom.
This ransomware group is linked to a broader threat actor associated with various ransomware strains, including TargetCompany, Tohnichi, Fargo, and Xollam.
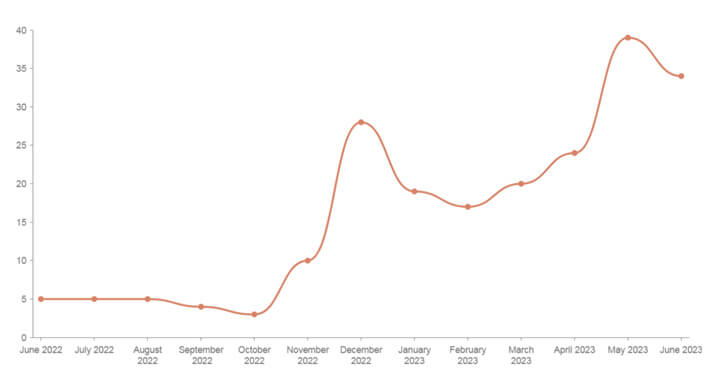
Characteristics
One noteworthy characteristic of Mallox is its modus operandi of exploiting poorly secured MS-SQL servers through dictionary attacks. These vulnerable servers act as a penetration vector to infiltrate victims’ networks. However, researchers have also observed Mallox deviating from this norm by using malicious OneNote file attachments for initial access.
Furthermore, once Mallox gains a foothold on the compromised host, it executes a PowerShell command to retrieve the ransomware payload from a remote server. The binary then takes measures to hinder recovery efforts by stopping and removing SQL-related services, deleting volume shadow copies, clearing system event logs, and terminating security-related processes. After encrypting the victim’s data, Mallox drops a ransom note in every directory.
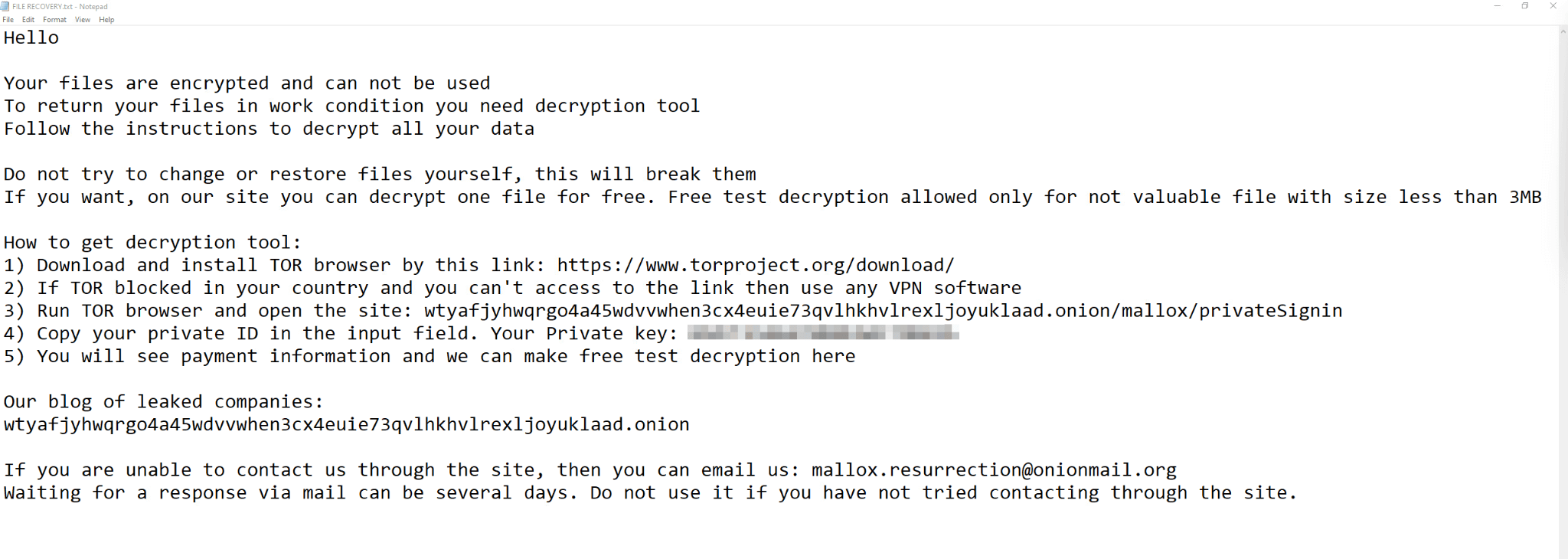
Despite being a relatively small and closed group in the past, Mallox has been actively recruiting affiliates for its ransomware-as-a-service (RaaS) program, which might explain the recent surge in its activities.
Further Context and Mitigations
The sudden escalation in Mallox infections is part of a broader trend in the ransomware landscape. Ransomware attacks, in general, have surged by 221% year-over-year as of June 2023, with a total of 434 attacks reported in June 2023 alone, largely driven by the Clop ransomware group’s exploitation of the MOVEit file transfer software vulnerability.
The researchers warned that the heightened activity of the Mallox ransomware group, coupled with the recruitment efforts, could lead to more attacks on organizations if successful.
To defend against such threats, organizations are advised to ensure the proper configuration of internet-facing applications, keep all systems patched and up to date, and implement endpoint security controls for detecting suspicious activities. Being proactive in cybersecurity measures remains the best defense against ransomware threats like Mallox.
You can find the full, comprehensive, article on How to Mitigate Ransomware, here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/mallox-ransomware-surge-in-activity/
Category & Tags: Cybersecurity News – Cybersecurity News




















































