Source: securityboulevard.com – Author: Michael Toback
Introduction
In today’s rapidly evolving digital landscape, the surge of Internet of Things (IoT) devices stands out as a transformative force. As we integrate smart devices into every facet of our daily lives, from our homes to our workplaces, the question arises: What security or other risks might you encounter with IoT? While our previous article delved deep into the intricacies of IoT security, this piece shifts the spotlight to the pressing risks and challenges associated with these devices. As IoT continues to reshape our world, understanding these potential pitfalls becomes paramount for businesses and individuals alike.
The Growing Importance of IoT in Business
In the modern business landscape, the Internet of Things (IoT) is no longer a futuristic concept; it’s a present-day reality. Especially for small businesses, the allure of IoT is hard to resist. With limited resources and a constant drive for efficiency, these enterprises are finding innovative ways to integrate smart devices into their operations.
Seamless Integration and Automation
One of the most significant advantages of IoT for businesses is the ability to automate routine tasks. From smart thermostats that adjust the office temperature based on occupancy to inventory systems that automatically reorder supplies when they run low, IoT devices are taking over tasks that once required manual intervention. This not only saves time but also reduces the margin for human error.
Enhanced Customer Experiences
In the retail sector, for instance, smart fitting rooms equipped with IoT sensors can suggest accessories to go with the outfit a customer is trying on. In restaurants, IoT-enabled tables can allow customers to place orders directly, enhancing their dining experience. Such personalized interactions, powered by IoT, can significantly boost customer satisfaction and loyalty.
Data-Driven Decision Making
IoT devices are prolific data generators. Every interaction, every sensor reading, every feedback loop provides businesses with valuable data. For small businesses, this data is gold. It offers insights into customer behavior, operational efficiencies, and market trends. By analyzing this data, businesses can make informed decisions, tailor their offerings, and predict future trends.
Cost Savings and Efficiency
Operational efficiency is another area where IoT shines. Consider a small manufacturing unit that uses IoT sensors to monitor machinery. These sensors can predict when a machine is likely to fail, allowing for preventive maintenance and reducing downtime. Similarly, smart lighting systems can reduce energy consumption, leading to significant cost savings in the long run.
In conclusion, as the digital and physical worlds continue to merge, the role of IoT in business becomes increasingly pivotal. For small businesses, in particular, the potential benefits of IoT integration are vast, ranging from operational efficiencies to enhanced customer experiences. However, with these benefits come challenges, especially in the realm of security, which we will delve into in the subsequent sections.
Real-life Breaches: A Wake-up Call
The rapid proliferation of IoT devices has undeniably brought about numerous advantages, from increased efficiency to enhanced user experiences. However, with this growth comes an increased risk of cyberattacks. Over the years, several high-profile breaches have served as stark reminders of the vulnerabilities associated with IoT devices.
The 2013 Target Breach: A Chain Reaction
In late 2013, retail giant Target fell victim to one of the most significant data breaches in history. The breach compromised the credit card information of 40 million customers and the personal data of an additional 70 million. But how did this happen? The initial point of entry for the hackers was not through Target’s main systems but via an HVAC company that provided services to Target. The attackers stole login credentials from the HVAC company, which had inadequate cybersecurity measures. Using these credentials, they gained access to Target’s network, eventually reaching the point-of-sale terminals and compromising vast amounts of customer data. This breach highlighted the interconnected nature of modern business ecosystems and the potential risks posed by weak links in the chain.
The Casino Fish Tank Thermometer Hack: An Unexpected Entry Point
In a rather unconventional cyberattack, hackers targeted a casino in 2017. However, their point of entry was not the casino’s main systems or its high-stakes poker tables. Instead, they exploited a vulnerability in a smart thermometer used in an aquarium in the casino’s lobby. Through this seemingly innocuous device, they managed to access the casino’s database, extracting 10GB of data, including information on high-rollers and the casino’s financial operations. This incident underscores the fact that in the world of IoT, even the most unexpected devices can serve as gateways for cybercriminals.
Other Notable Breaches
While the Target and casino breaches are particularly illustrative, they are by no means isolated incidents. Over the years, numerous other breaches have exposed the vulnerabilities of IoT devices:
- Jeep Cherokee Hack (2014): Security researchers remotely controlled a Jeep Cherokee, emphasizing the risks associated with connected vehicles.
- Dyn DDoS Attack (2016): A massive DDoS attack disrupted major websites worldwide, leveraging a botnet of compromised IoT devices.
- St. Jude Medical’s Cardiac Devices (2018): Vulnerabilities in cardiac devices could have allowed hackers to administer incorrect shocks to patients.
- Ring Camera Incidents (2019): Hackers accessed home security cameras, watching and speaking to unsuspecting residents.
In conclusion, as the IoT landscape continues to expand, so does the potential attack surface for cybercriminals. These real-life breaches underscore the importance of robust security measures, not just for individual devices but for entire interconnected ecosystems.

Challenges in Securing IoT Devices
The Internet of Things (IoT) is a vast, intricate web of interconnected devices, each with its own purpose and function. From smart refrigerators and wearable fitness trackers to industrial sensors and connected vehicles, the diversity of IoT devices is staggering. This vastness and variety, while being a testament to the potential of IoT, also present significant challenges when it comes to security.
The Diverse Nature of IoT: A Double-Edged Sword
The beauty of IoT lies in its adaptability. Devices can be tailored to fit specific needs, whether it’s a smart thermostat for a home or a sensor monitoring machinery in a factory. However, this diversity means that there’s no one-size-fits-all solution for security. Each device, depending on its function, manufacturer, and intended use, may have unique vulnerabilities. This makes it challenging to develop a standardized security protocol that can be applied across the board.
Limited Computing Capabilities: A Vulnerability in Disguise
Many IoT devices are designed to be compact and energy-efficient. As a result, they often have limited computing capabilities. Most of these devices run on very basic operating systems, if they have an OS at all. This poses a significant challenge for security. Comprehensive encryption and other advanced security measures often require substantial computational power. Given the limited resources of many IoT devices, implementing robust security measures can be a daunting task.
The Update Conundrum: Keeping Devices Secure
One of the cornerstones of cybersecurity is the regular updating and patching of software to address known vulnerabilities. However, in the world of IoT, this is easier said than done. Many devices are not designed to receive regular updates. Some may not even have a mechanism for updating their software. This means that once a vulnerability is discovered, it may remain unpatched, leaving the device exposed to potential attacks. Furthermore, even when updates are available, the onus often falls on the end-user to initiate them. Given the sheer number of IoT devices in use, ensuring that each one is up-to-date is a monumental challenge.
In conclusion, while the potential of IoT is undeniable, so are the challenges associated with securing these devices. As the number of connected devices continues to grow, addressing these challenges becomes not just important but imperative for businesses and individuals alike.
Best Practices to Mitigate IoT Security Risks
As the digital landscape continues to evolve, so does the sophistication of cyber threats. With the proliferation of IoT devices, businesses and individuals are exposed to a myriad of potential security vulnerabilities. However, by adhering to best practices, many of these risks can be mitigated, ensuring a safer and more secure IoT environment.
Regular Software/Firmware Updates: The First Line of Defense
One of the most effective ways to protect IoT devices from potential threats is to keep their software and firmware up-to-date. Manufacturers often release updates to address known vulnerabilities and enhance device performance. By regularly updating devices, users can ensure that they are protected against known threats. It’s essential to set devices to update automatically, if possible, or to establish a routine check for available updates. Remember, an outdated device is a vulnerable device.
Secure Communications and Encryption: Guarding the Data Highways
IoT devices constantly communicate with each other and with central servers, transmitting vast amounts of data. Ensuring that this data is transmitted securely is paramount. Secure communications can be achieved through encryption, which scrambles data in such a way that only authorized parties can decipher it. Whether it’s a smartwatch transmitting health data or a smart thermostat adjusting the temperature based on user preferences, encryption ensures that this data remains confidential and tamper-proof.
Multi-factor Authentication and Other Security Measures: Adding Layers of Protection
Passwords alone are no longer sufficient to protect devices from unauthorized access. Multi-factor authentication (MFA) adds an additional layer of security by requiring users to provide two or more verification factors to gain access. This could be something they know (password), something they have (a smart card or token), or something they are (fingerprint or facial recognition). Implementing MFA ensures that even if a password is compromised, unauthorized users cannot gain access without the additional verification factor.
In addition to MFA, other security measures such as setting strong, unique passwords, disabling unused features, and regularly monitoring device activity can further enhance the security of IoT devices.
In conclusion, while the challenges associated with IoT security are real and ever-evolving, they are not insurmountable. By adhering to best practices and staying informed about the latest threats and solutions, users can enjoy the benefits of IoT while minimizing the associated risks.
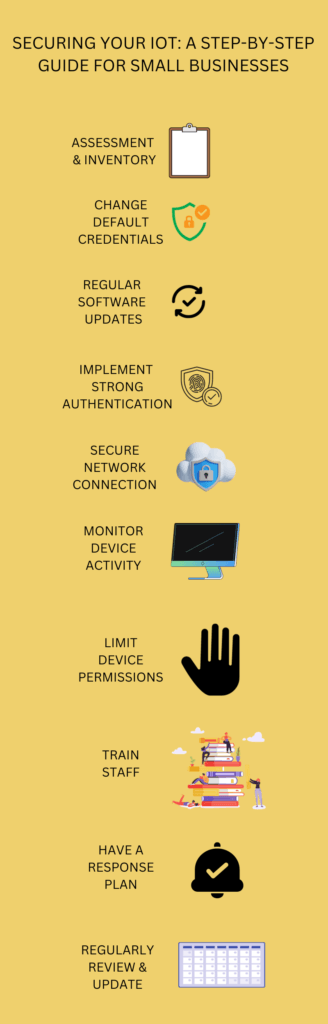
Securing Your IoT: A Comprehensive Guide for Small Businesses
It is essential for small businesses to take proactive steps in securing their IoT devices. The first step in this journey is assessment and inventory. It’s crucial to understand the landscape of your IoT devices. This means knowing what devices you have, their functions, and how they connect to your network. Imagine a detailed checklist, highlighting various devices from smart thermostats to printers.
Once you’ve taken stock, it’s time to change those default credentials. A surprising number of IoT devices come equipped with generic usernames and passwords. It’s like leaving the front door of your house wide open! Ensure you replace these with unique and robust credentials. Picture a lock, initially open, but then securely fastened with a sturdy key.
Next, we can’t stress enough the importance of regular software updates. Just like you’d service a car to keep it running smoothly, your IoT devices need the latest software to guard against potential threats. Think of this as a continuous cycle, always evolving, always improving, symbolized by a circular arrow with a reassuring checkmark at its heart.
In the realm of IoT security, passwords alone won’t cut it. Implementing strong authentication methods, like multi-factor authentication (MFA), is akin to having a double-lock system. It’s an added layer, ensuring that even if one barrier is breached, there’s another line of defense. Visualize a two-tiered security podium, where one level represents the traditional password and the next, a more advanced authentication method.
Your IoT devices are constantly communicating, sending, and receiving data. It’s vital to secure these network connections. Using encrypted pathways, like VPNs, ensures that your data travels safely. Moreover, segmenting your network can prevent IoT devices from directly accessing critical business systems. Picture a fortified data stream, shielded and passing through a secure tunnel.
But securing your devices isn’t a one-time task. Monitoring device activity is an ongoing process. Regular checks can help spot unusual patterns, which might be red flags indicating potential breaches. Envision a vigilant eye, always on the lookout, scanning the intricate web of your network.
Moreover, it’s essential to limit device permissions. Not every device in your arsenal needs unrestricted access. By limiting permissions, you’re essentially controlling the amount of data each device can access, much like adjusting a slider from “full” to “limited” access.
Your team is an integral part of this security framework. Educating and training staff ensures everyone is on the same page. It’s about fostering a culture of security awareness, where every member understands the significance of IoT security. Imagine a collaborative learning environment, where ideas are exchanged, and best practices are shared.
However, even with the best measures in place, breaches can happen. Having a response plan ensures you’re prepared for any eventuality. It’s about knowing the immediate steps to take, the people to contact, and strategies to minimize damage. Think of it as having an emergency toolkit, always ready to tackle unforeseen challenges.
Lastly, security isn’t static. It’s a dynamic, ever-evolving field. Regular reviews and updates ensure you’re always a step ahead, ready to tackle new threats and vulnerabilities. Imagine a calendar, marking regular security check-ins, emphasizing the need for continuous vigilance.
Expert Insights on IoT Security
The realm of IoT security is dynamic, with new challenges and solutions emerging regularly. As we continue to integrate more devices into our daily lives and business operations, understanding the trajectory of IoT security becomes crucial. Here’s what experts are forecasting and the innovations they’re excited about.
Predictions on the Evolution of IoT Security Threats
As IoT devices become more prevalent, the potential attack surface for cybercriminals expands. Experts predict several trends in the evolution of IoT security threats:
- Increased Targeting of Critical Infrastructure: As cities become smarter and industries more connected, critical infrastructures like power grids, transportation systems, and water supplies may become prime targets for cyberattacks.
- Ransomware on IoT: While ransomware attacks on computers and servers are well-known, there’s a growing concern that IoT devices could be the next targets. Imagine a scenario where a hacker takes control of all smart devices in a home or office and demands a ransom for their release.
- Device Spoofing: With the proliferation of IoT devices, there’s a potential for attackers to create fake devices that mimic genuine ones, leading to data theft or network compromise.
The Role of AI and Machine Learning in Enhancing IoT Security
Artificial Intelligence (AI) and Machine Learning (ML) are not just buzzwords; they’re revolutionizing many sectors, including IoT security. Here’s how:
- Real-time Threat Detection: AI algorithms can analyze vast amounts of data from IoT devices in real-time, identifying unusual patterns or behaviors that might indicate a security breach.
- Predictive Analysis: Machine learning can predict potential future threats by analyzing past security incidents and understanding their patterns.
- Automated Response: In the event of a security breach, AI can initiate immediate automated responses, such as isolating affected devices or networks, even before human intervention.
- Enhanced Encryption: AI can be used to develop more robust encryption techniques, ensuring that data transmitted between IoT devices remains secure.
In the words of Dr. John Barrett, “The Internet of Things is not a concept; it is a network, the true technology-enabled network of all networks.” As this network grows and evolves, leveraging the power of AI and ML will be paramount in ensuring its security.
In conclusion, while the future of IoT security presents challenges, it also offers opportunities for innovation and enhancement. By staying informed and proactive, we can navigate this evolving landscape with confidence and foresight.
Conclusion
The digital age has ushered in a plethora of innovations, with the Internet of Things (IoT) standing out as one of the most transformative. As businesses, especially small ones, increasingly integrate IoT devices into their operations, the importance of understanding and addressing the associated security risks cannot be overstated.
While the potential of IoT is vast, so are the challenges. From the diverse nature of devices to the ever-evolving threat landscape, securing IoT is a complex endeavor. However, with awareness, education, and proactive measures, these challenges can be effectively managed.
We encourage you to delve deeper into the world of IoT security. Explore other resources, share your insights, and engage in discussions. The comments section below is a platform for you to voice your thoughts, ask questions, and learn from others. Together, we can foster a community that is well-informed and equipped to navigate the intricacies of IoT security.
| Key Point | Brief Description |
|---|---|
| Rise of IoT Devices | Overview of the increasing integration and significance of IoT devices in the modern digital landscape. |
| IoT Security Breaches | Discussion on real-life breaches, including the Target 2013 breach and the casino fishtank thermometer hack. |
| Challenges in Securing IoT | Exploration of the diverse nature of IoT devices, their limited computing capabilities, and the challenge of regular updates. |
| Mitigating IoT Security Risks | Best practices like regular software updates, secure communications, and multi-factor authentication. |
| Expert Insights | Predictions on the evolution of IoT security threats and the role of AI and machine learning in enhancing IoT security. |
Further Reading and Resources
For more information on IoT Security see our article on Business IoT devices or our deep dive into IoT Security
The post What security or other risks might you encounter with IoT? appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/iot-security-risks/?utm_source=rss&utm_medium=rss&utm_campaign=iot-security-risks
Original Post URL: https://securityboulevard.com/2023/09/what-security-or-other-risks-might-you-encounter-with-iot/
Category & Tags: IoT & ICS Security,Security Bloggers Network,iot – IoT & ICS Security,Security Bloggers Network,iot