Threat actors upgraded Typhon info-stealer to a version that has improved evading features against analysis and anti-virtualization mechanisms. The new Typhon Reborn V2 malware is currently advertised on a dark web forum.
Typhon was first discovered in August 2022 and at the moment the malware was a mix of info-stealer, keylogger, and crypto-miner. At first, hackers sold Typhon on Telegram for only $50/lifetime use.
According to researchers, the new Typhon Reborn V2 version has been promoted and purchased on the dark web since the beginning of 2023.
What Does Typhon Reborn V2 Do
The info-stealing malware comes with a broad series of functionalities:
- Steals system files/information
- Extracts cryptocurrency wallet data
- Exfiltrates data from Chromium and Edge Browser Extensions
- Is able to take screenshots
- Steals passwords, tokens, and other data
After the info-stealer gathers the data, it sends it further to the command-and-control servers. To control the C2, threat actors use Telegram API.
What Are the New Features
After analyzing the codebase, researchers claim the new info-stealer is more robust, reliable, and stable. The malware developers used Base64 encoding and XOR to enhance the obfuscation capabilities of Typhon Reborn V2.
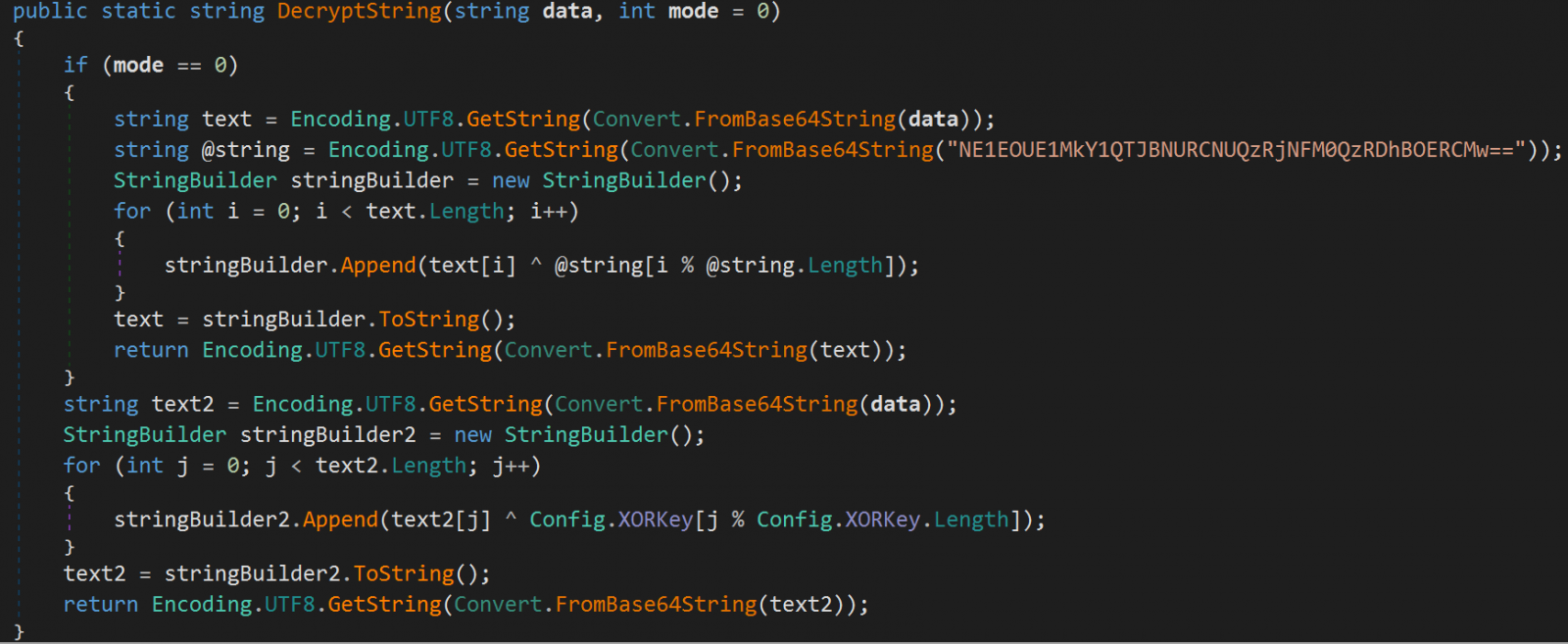
In order to avoid infecting the analyzing machines, the malware evaluates a larger mix of elements:
- Usernames
- CPUIDs
- Applications
- Processes
- Debugger/emulation checks
- Geolocation data
Typhon Reborn V2 is able to exclude Commonwealth of Independent States (CIS) countries and can even check geolocation lists before it decides to execute its malicious routines.
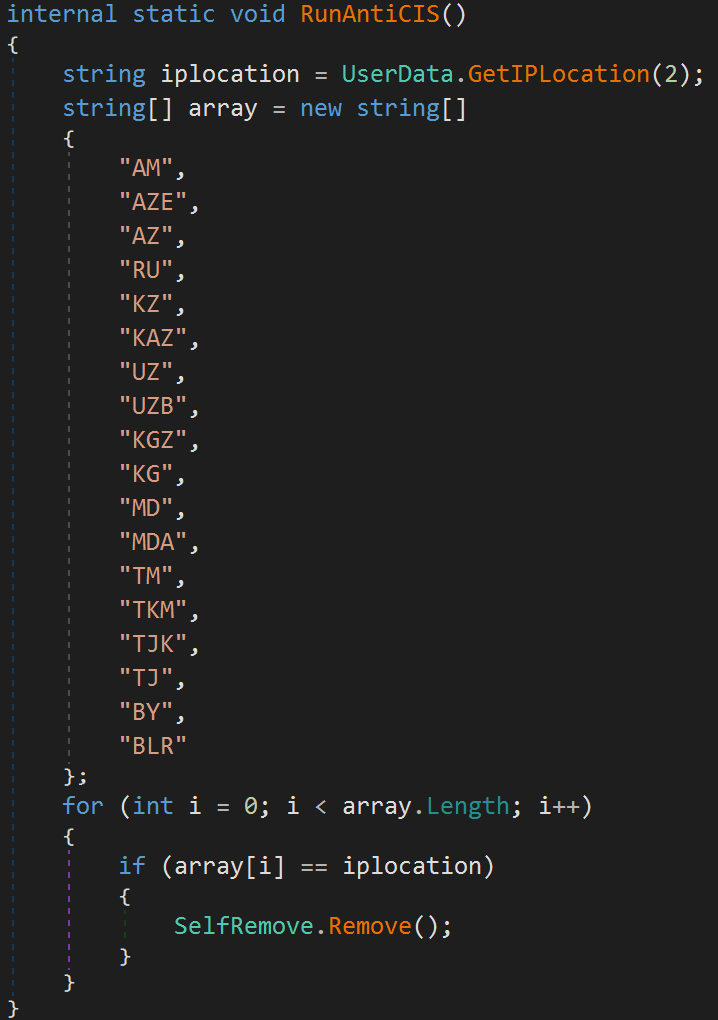
The new info-stealing malware is also able to tell if it runs on a victim’s environment or on a simulated host provided by a researcher`s machine. Here is the check-list the new Typhon version uses before it decides whether to act or not:
- Analyze GPU information
- Check the presence of DLLs associated with security software
- Look after video controllers for VM indicators
- Check the username on the system
- Check for the presence of Wine Windows emulator, etc.
Typhon Reborn V2 also has a new file grabber component. This enables the malicious actors to look for and extract specific files from the machine.
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.




















































