Trends and insights to drive an integrated multicloud security strategy Executive Foreword The advent of cloud...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Microsoft Security
From plan to deployment: Implementing a cloud-native application protection platform(CNAPP) strategy
The document emphasizes the importance of Cloud Security Posture Management (CSPM) and the utilization of Defender...
The advent of cloud computing ushered in a new ra of innovation, empowering organizations to rapidly...
Security Program and Strategy The document focuses on cybersecurity aspects, including the importance of integrated security...
How often to refresh a playbook?Playbooks are most effective when they stay current, evolve with organizational...
What: Guide organizations through an end-to-end security modernization from strategy and program level through architecture and...
Executive SummaryRansomware and extortion attacks are a high profit, low-cost attacker business model that have a...
As a CISO, nobody understands the security risks that your organisation faces better than you. You’ve...
IntroductionOrganizations have seen a massive increase in their digital footprint with hybrid work, extending well beyond...
Why Prepare The benefits of proactive threat hunting Like wilderness survival experts, threat hunters succeed because...
5 elements that help companies have stronger data protection and security while protecting user trust. Why...
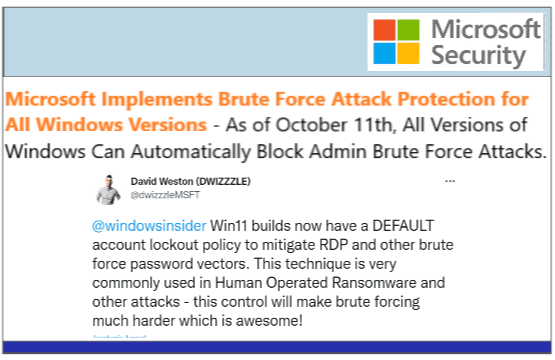
Yesterday, Microsoft announced that IT administrators can now set up group policies to automatically prevent brute...
Table of Content Why prepare ? Modern Attacks Know the terrain Identify the signs of an...
How solutions have evolved and why you should too ForwardRudra MitraCVP, Microsoft data security and privacy...