The use cases for generative Al in the public sector present an exciting opportunity to improve...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Microsoft
The Incident Response Reference Guide is a comprehensive document spanning 43 pages, offering detailed insights and...
The document provides detailed guidance on managing Network Security Groups (NSGs) in Azure for effective network...
Many organizations will experience a major incident or must respond to difficult questions about preventing, detecting,...
A PRACTICAL GUIDE FOR THE TIME-STRAPPED ADMIN There used to be a saying in the SMB...
In many companies today, data governance has become increasingly important but what exactly is it? What...
The National Cyber Security Centre (NCSC), in coordination with Microsoft and Ekco, have developed this Secure...
In a world where cloud migration has become the norm, data and system security has become...
The National Cyber Security Centre (NCSC), in coordination with Microsoft and Ekco, have developed this Secure...
Digital transformation is shaping the new normal Organizations are embracing digital transformation to manage continuous business...
In the field of forensic computing, the ability to use efficient commands in Windows systems is...
Defending-Ukraine-??-PDFDescarga
AbstractIn this document, we will share guiding principles for implementing a Zero Trust security model and...
IntroductionKeeping your employees and organization secure without compromising productivity is a challenge.Microsoft 365 security solutions are...
AbstractThis document focuses on the resiliency aspect of Azure. It provides guidance on designingresilient applications on...
IntroductionCritical infrastructure and related essential services lie at the core of our societies. They increasingly rely...
Cybercriminals emboldened by underground ransomware economy. While ransomware continues to be a headline-grabbing topic, there’s ultimately...
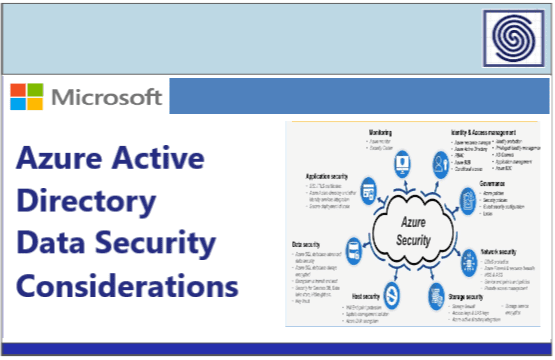
IntroductionThis document explains the following aspects of Azure Active Directory:• Azure AD Components: What are the...
IntroductionThe acceleration of digital transformation and the expansion of both remote and hybridworkplaces brings new opportunities...