Source: www.techrepublic.com – Author: Cedric Pernet

New malware dubbed Meduza Stealer can steal information from a large number of browsers, password managers and cryptocurrency wallets, according to a report from cybersecurity company Uptycs. The malware was developed to target Windows operating systems.
Uptycs research indicates that “no specific attacks have been attributed to date” though, probably because Meduza Stealer is new malware. It’s highly suspected that Meduza Stealer is spread via the usual methods used for information stealers, such as compromised websites spreading the malware and phishing emails.
Learn what happens when Medusa Stealer is launched, how the malware is being promoted to cybercriminals and tips on protecting your company from this cybersecurity threat.
Jump to:
- What happens when Meduza Stealer is launched?
- Meduza Stealer’s massive theft capabilities
- How Meduza Stealer is promoted to cybercriminals
- How to stay safe from this cybersecurity threat
What happens when Meduza Stealer is launched?
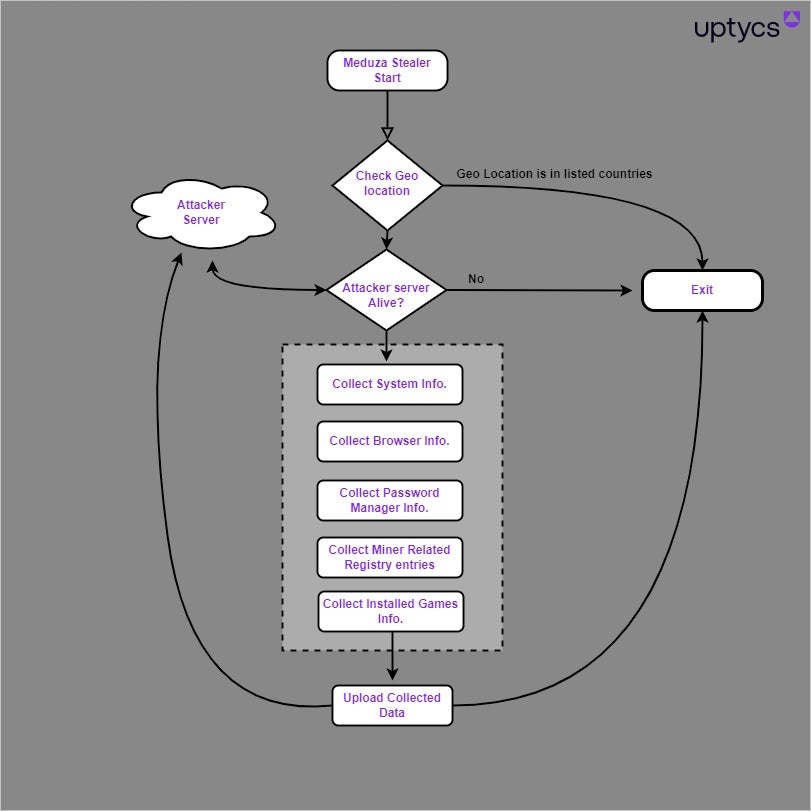
Once Meduza Stealer is launched, the malware starts checking for its geolocation by using the Windows GetUserGeoID function. This function looks for a country value based on the system’s settings and not real geolocation information. The malware stops working if the result indicates one of these 10 countries: Russia, Kazakhstan, Belarus, Georgia, Turkmenistan, Uzbekistan, Armenia, Kyrgyzstan, Moldova and Tajikistan.
The next step for the malware consists of checking if it can reach the attacker’s server before starting to collect basic information on the infected system, such as computer name, CPU/GPU/RAM/Hardware details, operating system version’s precise build details, time zone and current time, username, public IP address, execution path and screen resolution. Meduza Stealer also makes a screenshot. Then, the malware is ready for its stealing operations (Figure A).
Figure A
Meduza Stealer’s massive theft capabilities
Browsers
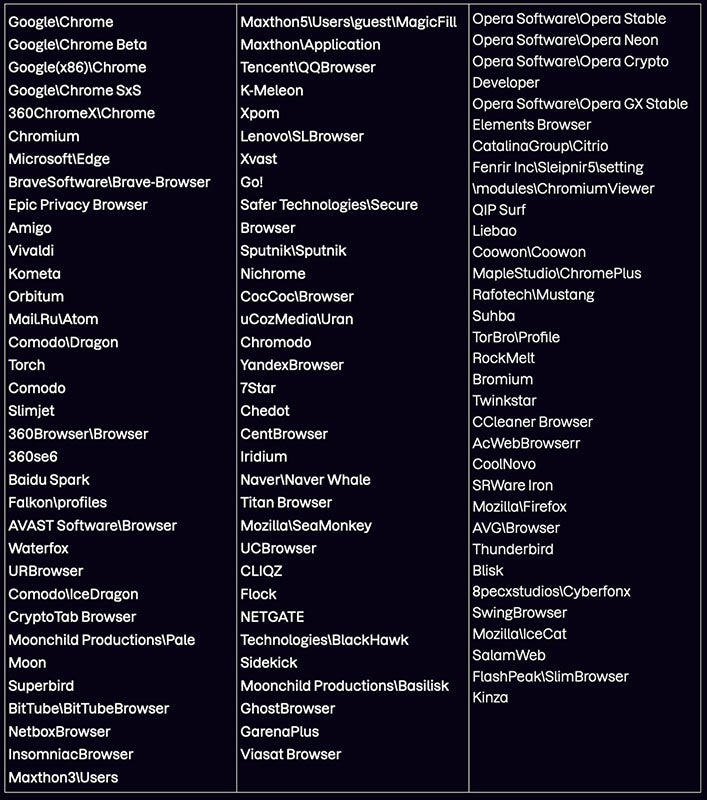
Meduza Stealer hunts for data in the User Data folder; it’s searching for browser-related information such as the browser history, its cookies, login and web data. A list of 97 browser variants is embedded in the malware, showing a huge effort not to miss any data from browsers (Figure B). Chrome, Firefox and Microsoft Edge are just three of the browsers on the list.
Figure B
Password managers
Nineteen password managers are targeted by Meduza Stealer based on their Extension ID (Figure C). LastPass, 1Password and Authy are just three of the password managers listed.
Figure C
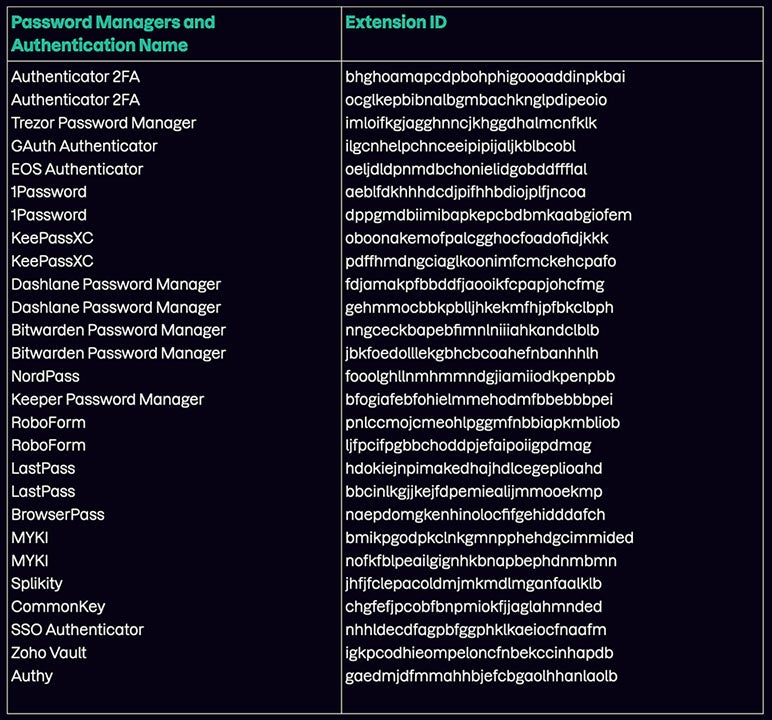
The malware specifically targets extensions associated with two-factor authentication and password managers with the intention of extracting data; these extensions possess significant information and may contain vulnerabilities. Through gaining access to 2FA codes or exploiting weaknesses in password manager extensions, the attacker might be able to evade security protocols and achieve unauthorized access to user accounts.
Cryptocurrency wallets
There are 76 cryptocurrency wallets currently targeted by Meduza Stealer.
From Uptycs Threat Research, “The malware attempts to extract cryptocurrency wallet extensions from web browsers via software plugins or add-ons that enable users to conveniently manage their cryptocurrency assets directly within web browsers like Chrome or Firefox. These extensions provide functionality for tasks such as monitoring account balances, conducting cryptocurrency transactions details.”
The malware gets configuration and related data from different Windows Registry keys:
- HKCUSOFTWAREEtherdyneEtherwallgeth
- HKCUSOFTWAREmonero-projectmonero-core
- HKCUSOFTWAREDogecoinCoreDogecoinCore-Qt
- HKCUSOFTWAREBitcoinCoreBitcoinCore-Qt
- HKCUSOFTWARELitecoinCoreLitecoinCore-Qt
- HKCUSOFTWAREDashCoreDashCore-Qt
More applications targeted
The Telegram Desktop application is being scanned by the malware, which looks for entries in the Windows registry that are specific to this application.
The malware also looks for the Steam gaming system application data that might be stored in the Windows registry. If Steam is installed on the computer, the data that can be fetched from it includes login data, session information, user-specific settings and other configuration data.
Discord is another application targeted by the malware, which accesses the Discord folder and collects information such as configuration and user-specific data.
How Meduza Stealer is promoted to cybercriminals
According to Uptycs researchers, the administrator of Meduza Stealer has been using “sophisticated marketing strategies” to promote the malware on several cybercriminal marketplaces and forums.
For starters, the actor doesn’t hesitate to provide screen captures of a large portion of antivirus software detection results, showing that only one antivirus solution (ESET) out of 26 detect it, whether that’s statically or dynamically.
To attract more customers, access to stolen data is offered through a web panel (Figure D). Different subscription options are shown to the potential customer: one month for $199 USD, three months for $399 USD or a lifetime plan.
Figure D
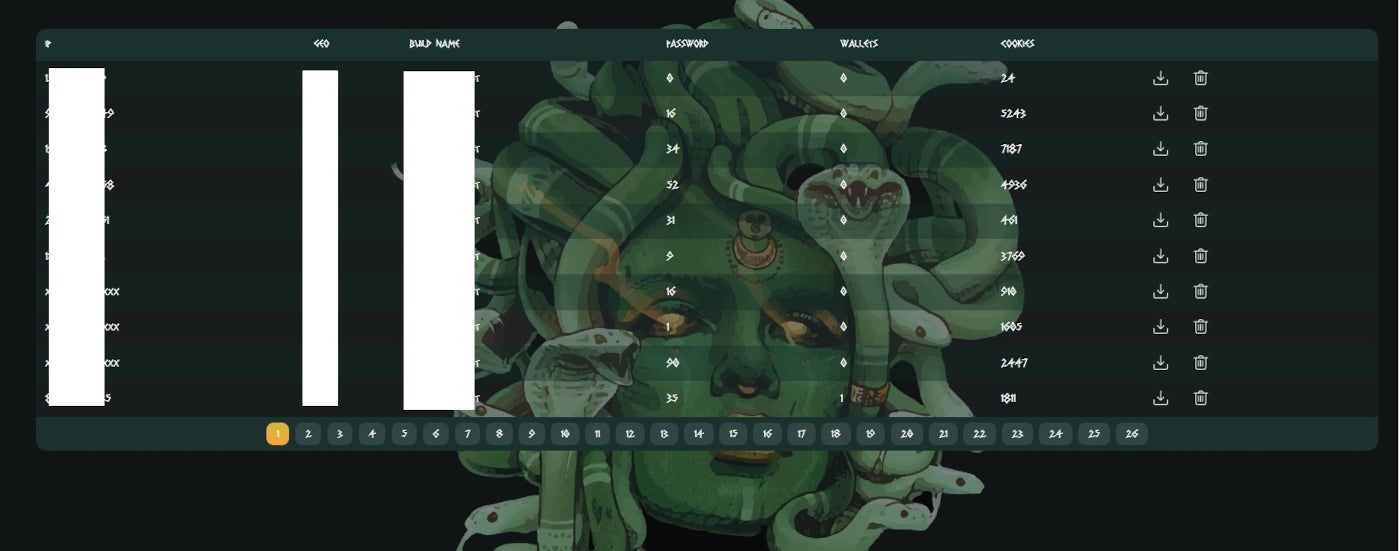
Once the user has subscribed, the person has full access to the Meduza Stealer web panel, which provides information such as IP addresses, computer names, country name, count of stored passwords, wallets and cookies on infected computers. Then, the subscriber can download or delete the stolen data directly from the web panel. This unprecedented feature is very useful because the data deletion guarantees that no other subscriber will be able to use that information because it’s immediately taken off.
How to stay safe from this cybersecurity threat
It’s strongly advised to have all operating systems and software up to date and patched to avoid being compromised by a common vulnerability. Browsers, in particular, need to be up to date; also, run as few plugins as possible to reduce the attack surface.
It’s also advised to deploy multifactor authentication where possible so an attacker cannot gain access to corporate resources, even if they’re in possession of valid credentials.
Security solutions need to be deployed on endpoints and servers, with monitoring capabilities to detect threats. It’s also advised to run YARA detection rules on corporate endpoints, such as the one provided by Uptycs to detect the Meduza Stealer.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
Original Post URL: https://www.techrepublic.com/article/meduza-stealer-targets-browser-variants-crypto-wallets-password-managers/
Category & Tags: International,Microsoft,Security,crypto wallets,cryptocurrencies,cybersecurity,malware,password managers – International,Microsoft,Security,crypto wallets,cryptocurrencies,cybersecurity,malware,password managers




















































