Source: www.techrepublic.com – Author: Cedric Pernet
Get technical details about how this new attack campaign is delivered via Microsoft Teams and how to protect your company from this loader malware.

A new report from global cybersecurity company Truesec reveals a new attack campaign leveraging Microsoft Teams to infect companies’ users. While the motivation of the attacker remains unknown, this DarkGate loader malware could allow its perpetrator to go for financial gain or cyberespionage.
Jump to:
- What is the DarkGate malware?
- How new attack spreads DarkGate loader via Microsoft Teams
- DarkGate’s business model
- How to protect from this DarkGate malware threat
What is the DarkGate malware?
DarkGate is a loader malware written in Delphi; the goal is to enable the download and execution of other malware once it runs on an infected computer. The additional malware is downloaded directly in the memory on 32- and 64-bits architectures, which makes it harder to detect because it doesn’t reside on the file system.
Other mechanisms implemented in the malware makes it more difficult to analyze:
- Anti-VM: The malware tests for known hardware/identifiers used in virtual machines.
- Anti-Sandboxes: The malware checks for known identifiers used by sandbox software.
- Anti-AntiVirus: Several antivirus products are being looked for.
- Anti-debug: The malware often checks for a debugger attached to the process.
- Disk space and memory checks: The malware can be set to only run with a minimum disk/memory size.
Depending on the results of all these checks, the malware might alter its behavior and possibly stop running.
DarkGate has persistence capabilities that can be enabled in its configuration. In that case, it stores a copy of itself on the hard drive and creates a registry key to be executed at reboot times.
Although DarkGate is mostly a loader for third-parties’ malware, it still has built-in capabilities.
- Information gathering: DarkGate is able to query the system to get information about the currently logged-in user, running software, processes and more, which it sends to the C2 server. It can also collect files from the system and send it to the C2 server, as well as do screen captures.
- Credentials theft: DarkGate is able to steal passwords and cookies from browsers, email software and other software such as Discord or FileZilla. To achieve that goal, the malware uses multiple legitimate free tools from the popular NirSoft website.
- Cryptomining capabilities: DarkGate is able to start, stop and configure a cryptominer.
- Remote access tool capabilities: DarkGate can initiate a virtual network connection and execute commands.
How new attack spreads DarkGate loader via Microsoft Teams
The attack consists of messages sent on Microsoft Teams by a threat actor who used two compromised Teams accounts for sale on the Dark Web. Those accounts were used to send socially engineered content to convince users to download and open a malicious archive file (Figure A).
Figure A
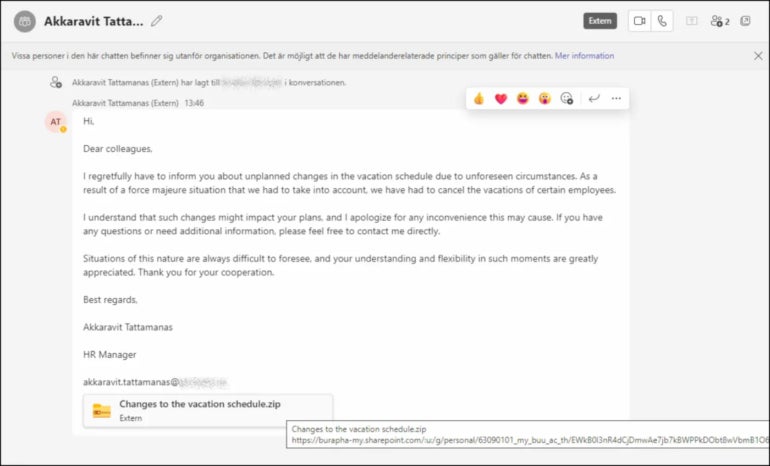
Once the zip file is opened, it shows the user a malicious LNK (shortcut) file posing as a PDF document (Figure B).
Figure B
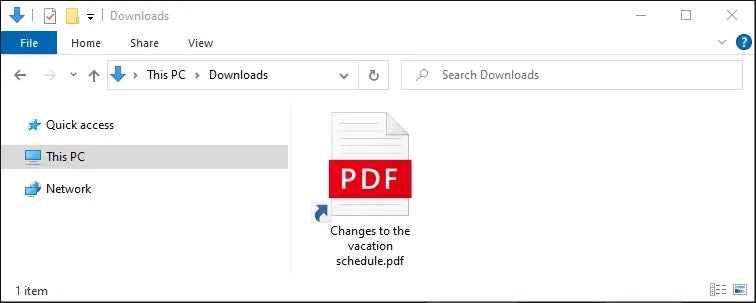
After the LNK file is clicked, it executes a command line that triggers the download and execution of AutoIT via a VBScript file. A precompiled AutoIT script is also downloaded and executed via the AutoIT software.
In this attack campaign, the AutoIT script checks for the presence of the Sophos antivirus; other campaigns might check for other antivirus solutions. If the antivirus isn’t installed, the script downloads a shellcode that in turn downloads a file, byte by byte, using the stacked strings technique in an effort to stay undetected. That final payload is the DarkGate loader malware.
DarkGate’s business model
DarkGate loader was advertised in June 2023 by its developer RastaFarEye (Figure C), as shown in a report from German company Telekom Security.
Figure C
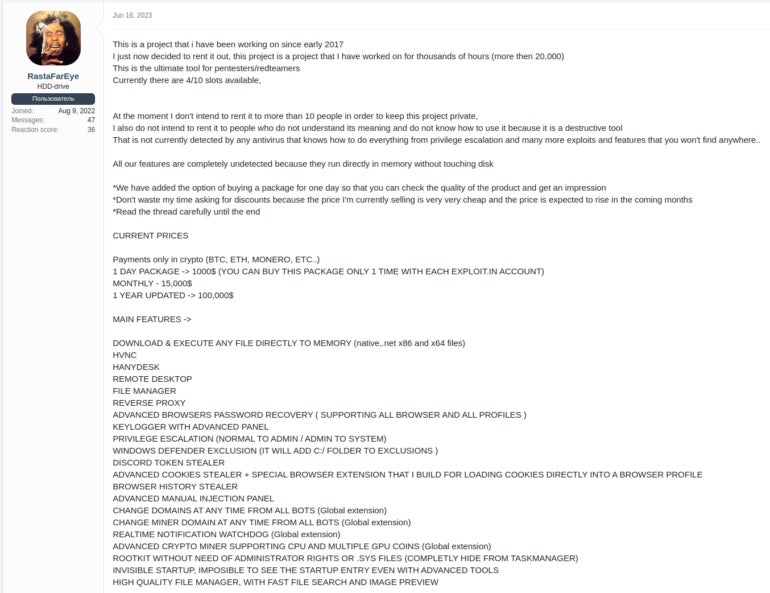
The threat actor limited the malware-as-a-service to only 10 affiliates at a monthly price of $15,000 USD, or $100,000 USD for a full year.
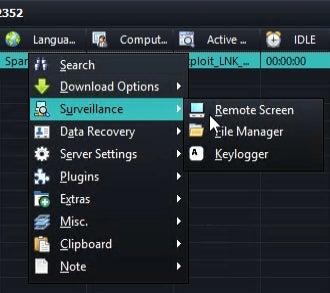
RastaFarEye also provided a video showing the malware builder and control panel (Figure D).
Figure D
DarkGate’s capabilities makes it a tool of choice for cybercriminals interested in financial fraud or threat actors interested in running cyberespionage campaigns.
In addition to developing DarkGate loader, RastaFarEye advertised more malware developed by himself, including on Mac operating systems. The cybercriminal also offered Extended Validation certificate creation services.
How to protect from DarkGate malware threat
In this attack campaign, the threat actor sent messages via Microsoft Teams to organizations using it. So, it’s strongly advised not to allow Microsoft Teams chat requests from external domains that don’t belong to the organization; only whitelisted external domains should be allowed to send chat requests.
Other attack campaigns that delivered DarkGate loader used emails to try to social engineer the target into opening a malicious file, so it’s also advised to deploy security solutions that analyze the URLs contained in emails in addition to attached files.
All operating systems and software should be up to date and patched to prevent being compromised by common vulnerabilities.
Multifactor authentication should be deployed wherever possible, so that even a threat actor in possession of valid credentials still cannot access the corporate environment.
Original Post URL: https://www.techrepublic.com/article/darkgate-loader-malware-microsoft-teams/
Category & Tags: Microsoft,Security,Software,cybersecurity,dark web,malware,Microsoft Teams,phishing – Microsoft,Security,Software,cybersecurity,dark web,malware,Microsoft Teams,phishing




















































