Source: www.bleepingcomputer.com – Author: Lawrence Abrams

Microsoft has released Sysmon 15, converting it into a protected process and adding the new ‘FileExecutableDetected’ option to log when executable files are created.
For those not familiar with Sysmon (or System Monitor), it is a free Microsoft Sysinternals tool that can monitor and block malicious/suspicious activity and log events to the Windows Event Log.
By default, Sysmon monitors basic events such as new process creation and the termination of processes. However, it is possible to create advanced configuration files that let you monitor various behavior, such as file deletions, Windows clipboard changes, and detecting and blocking the shredding of files.
Users can find the complete list of directives in the Sysmon schema, which can be viewed by running the sysmon -s command at the command line.
Yesterday, Microsoft released Sysmon 15.0, which includes two new features – the hardening of the program by turning it into a protected process and the ability to detect when executable files are created on the monitored system.
Sysmon is now a protected process
As Sysmon is commonly used to detect malicious behavior, it is in threat actors’ best interest to tamper with or disable the software.
With this release, Microsoft converted the Sysmon.exe executable into a protected process to prevent malicious code from being injected into the process.
“In Windows 8.1, a new concept of protected service has been introduced to allow anti-malware user-mode services to be launched as a protected service,” explains a Microsoft article about the feature.
“After the service is launched as protected, Windows uses code integrity to only allow trusted code to load into the protected service. Windows also protects these processes from code injection and other attacks from admin processes.”
After Sysmon is launched, you can see it is a protected process by using Process Explorer and examining its Security properties, as shown below.
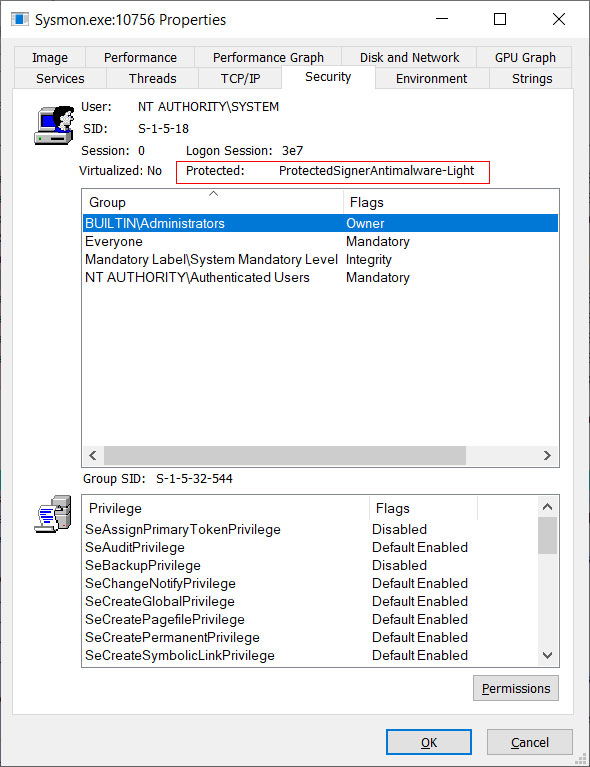
Source: BleepingComputer
Based on Process Explorer, Sysmon is running as a PPL process (PROTECTED_ANTIMALWARE_LIGHT), which is further described in this article by Elastic.
Detecting new executables files
System 15.0 also upgrades the Sysmon schema to version 4.90, which now includes the ‘FileExecutableDetected’ configuration option to detect the creation of executable files on the monitored device.
For example, to use the new FileExecutableDetected directive to detect new executables created under the C:ProgramData and C:Users folders, you can use the following configuration file:
MD5,SHA256 C:ProgramData C:Users
To start Sysmon and direct it to use the above configuration file, you would execute the sysmon -i command and pass the configuration file’s name.
In our example, the configuration file’s name is sysmon.conf, so we would use the following command from an Administrative Command Prompt to start Sysmon:
sysmon -i sysmon.confOnce started, Sysmon will install its driver and quietly collect data in the background.
All Sysmon events will be logged to ‘Applications and Services Logs/Microsoft/Windows/Sysmon/Operational‘ in the Event Viewer.
With the FileExecutableDetected feature enabled, when a new executable file is created under the C:ProgramData or C:Users folder (and any of their subfolders), Sysmon will generated an executable is created and matches a rule, Sysmon will block the file and generate an ‘Event 29, File Executable Detected’ entry in Event Viewer.
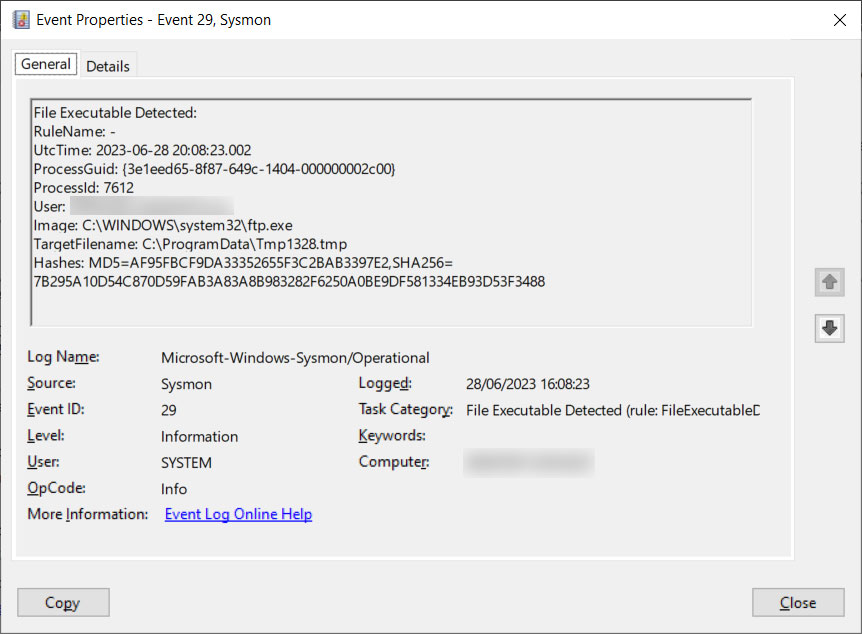
Source: BleepingComputer
The created Event Log entries will contain a lot of valuable information, explained below:
- UtcTime: Time the event was detected.
- ProcessID: The PID of the process attempting to create the executable file.
- User: The user associated with the process creating the file.
- Image: The filename of the program creating the file.
- TargetFilename: The executable file that was created. Note: In our tests, the file was always displayed under a temporary file name.
- Hash: The hash of the file that was being created. The displayed hashes will depend on your HashAlgorithms configuration setting.
For even more information and creative tips on using this new feature, it is strongly recommended that you read Olaf Hartong’s excellent writeup on this new version of Sysmon.
For those who want a premade Sysmon configuration file that uses this feature to detect when known malware or hack tool executables are created, you can use security researcher Florian Roth’s Sysmon config.
Learn more about Sysmon
Sysmon is an advanced network monitoring tool with a ton of directives that allow you to create configuration files that meet your organization’s needs.
Due to the program’s complexity, it is strongly advised that you read the Sysmon documentation and play around with configuration options to see how the various directives work.
Unfortunately, Sysmon is not a well-documented program, requiring users to conduct trial and error to test features and see what events are written to the event log.
The good news is that Sysmon will not load a misconfigured configuration file, so if you see a “Configuration file validated” message when loading Sysmon, you know that you’re at least on the right track.
You should also read Olaf Hartong’s blog posts about Sysmon, as he documents the new features as they are released.
Finally, admins can use or read through the premade Sysmon configuration files from Florian Roth and SwiftOnSecurity to see how directives can be used to block malware.
Original Post URL: https://www.bleepingcomputer.com/news/microsoft/microsoft-sysmon-now-detects-when-executables-files-are-created/
Category & Tags: Microsoft,Security – Microsoft,Security




















































