Source: www.bleepingcomputer.com – Author: Bill Toulas

Hackers have been exploiting the two zero-day vulnerabilities in Ivanti Connect Secure disclosed this week since early December to deploy multiple families of custom malware for espionage purposes.
Identified as CVE-2023-46805 and CVE-2024-21887, the security issues allow bypassing authentication and injecting arbitrary commands on vulnerable systems. Ivanti said that the attackers targeted a small number of its customers.
A report from Mandiant, who works with Ivanti investigating the incident, notes that the threat actor behind the attacks is engaged in espionage and is currently tracked internally as UNC5221.
Today, threat monitoring service Shadowserver has posted on X that its scanners detect 17,100 Invanti CS appliances on the public web, most of them in the United States.
However, there is no indication to how many of them are vulnerable.
Deployed malware
Mandiant found that UNC5221 uses a set of tools during the post-compromise stage that includes five custom malware for planting webshells, executing commands, dropping payloads, and stealing credentials.
Here’s a summary of the tools used in the attacks:
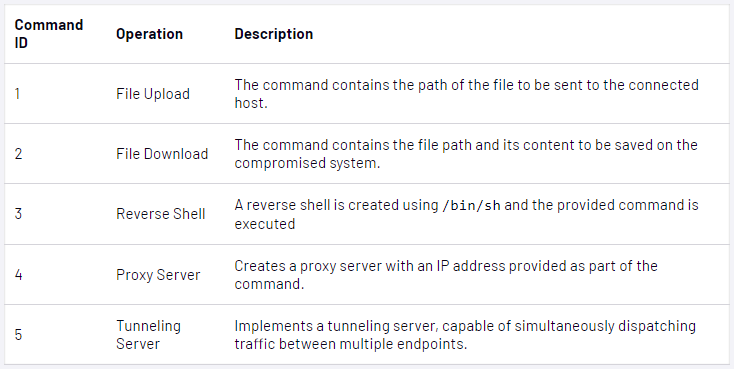
- Zipline Passive Backdoor: custom malware that can intercept network traffic, supports upload/download operations, creating reverse shells, proxy servers, server tunneling
- Thinspool Dropper: custom shell script dropper that writes the Lightwire web shell onto Ivanti CS, securing persistence
- Wirefire web shell: custom Python-based web shell supporting unauthenticated arbitrary command execution and payload dropping
- Lightwire web shell: custom Perl web shell embedded in a legitimate file, enabling arbitrary command execution
- Warpwire harverster: custom JavaScript-based tool for harvesting credentials at login, sending them to a command and control (C2) server
- PySoxy tunneler: facilitates network traffic tunneling for stealthiness
- BusyBox: multi-call binary combining many Unix utilities used in various system tasks
- Thinspool utility (sessionserver.pl): used to remount the filesystem as ‘read/write’ to enable malware deployment
“ZIPLINE is the most notable of these families, it is a passive backdoor that hijacks an exported function accept() from libsecure.so. ZIPLINE intercepts incoming network traffic and supports file transfer, reverse shell, tunneling, and proxying,” stated a Mandiant security researcher on X (formerly Twitter).
Mandiant also found that the attackers used compromised end-of-life Cyberoam VPN appliances as C2 servers, with their location set in the same region as the target, to evade detection.
Volexity previously reported seeing signs of the attacks being conducted by Chinese state-sponsored threat actors. However, Mandiant’s report does not make any attribution or provide information about the potential origin or affiliation of the threat actor.
The Google company says there’s not enough data to assess the origin of UNC5221 with confidence and noted that its activity isn’t linked to any previously known threat groups.
Even without attribution, the use of custom malware that provides continued access indicates that “UNC5221 intended to maintain its presence on a subset of high priority targets” even after a patch became available.
Mandiant suspects that UNC5221 is an advanced persistent threat (APT) that set sight on high-priority targets.
System admins are reminded that there is currently no security update that addresses the two zero-days, but Ivanti provides mitigations that should be implemented immediately.
Original Post URL: https://www.bleepingcomputer.com/news/security/ivanti-connect-secure-zero-days-exploited-to-deploy-custom-malware/
Category & Tags: Security – Security




















































