Source: go.theregister.com – Author: Team Register
Some smart cookies at institutions in China and Singapore have devised a technique for reading keystrokes and pilfering passwords or passcodes from Wi-Fi-connected mobile devices on public networks, without any hardware hacking.
The technique is made possible thanks to beamforming feedback information (BFI), which consists of data about wireless signal characteristics that turns out to be useful for ensuring a strong network connection and for applications like Wi-Fi sensing.
Beamforming is a technique that directs radio waves towards the device intended to receive them, instead of transmitting them omni-directionally. It was standardized within Wi-Fi 802.11ac – perhaps without sufficient concern about security because the BFI it generates travels unprotected in cleartext on public networks.
That’s not good on non-password-protected, publicly accessible networks, as might be encountered at a cafe, shopping mall, or airport. If you only care about private, password-protected networks, the rest of this article is literally academic for you.
Also because this relies on public, unprotected Wi-Fi, one assumes the target of the snooping isn’t sending any sensitive information, such as their passwords, over the network in cleartext: that would be a lot easier to capture than screwing around with BFI frames. It’s assumed the target is using HTTPS/TLS and/or a VPN to protect their network traffic, but doing so over public Wi-Fi.
In a preprint paper titled “Password-Stealing without Hacking: Wi-Fi Enabled Practical Keystroke Eavesdropping,” authors Jingyang Hu, Hongbo Wang, Tianyue Zheng, Jingzhi Hu, Zhe Chen, Hongbo Jiang, and Jun Luo describe how they came up with a way to infer numerical passwords by capturing BFI and analyzing the results. Their work has been accepted into the ACM SIGSAC Conference on Computer and Communications Security, to be held in November in Denmark.
“We propose WiKI-Eve to eavesdrop keystrokes on smartphones without the need for hacking,” the computer scientists, who have ties to Hunan University and Fudan University in China, and Nanyang Technological University in Singapore, explained.
“WiKI-Eve exploits a new feature, BFI (beamforming feedback information), offered by latest Wi-Fi hardware: since BFI is transmitted from a smartphone to an AP [access point] in cleartext, it can be overheard (hence eavesdropped) by any other Wi-Fi devices switching to monitor mode.”
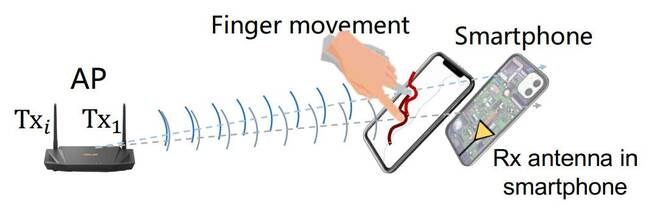
Illustration from the paper showing how finger movements can disrupt signals, and thus be sensed via BFI. Credit: Hu et al
KI is capitalized here to indicate “keystroke inference” – inferring what keystroke occurred from the BFI data. As a surveillance target moves their finger around their phone or tablet to type out things, like a password or passcode, the diffraction pattern of the wireless network’s radio signals between the device and the base station is disturbed enough that it shows up in the BFI, which can be eavesdropped and used to infer which keys are being tapped on screen, it is claimed.
Basically, by recording the BFIs in Wi-Fi frames when the victim – Bob – is typing his password, a nearby spy – Eve – can collect time series data of BFI samples that can be correlated to the typed password using a deep-learning model.
Will this research result in actual practical attacks? We’re willing to bet no, but still: it’s a pretty fun technique, and one Reg readers may find interesting.
- Warning: Your wireless networks may leak data thanks to Wi-Fi spec ambiguity
- Tech industry quietly patches FragAttacks Wi-Fi flaws that leak data, weaken security
- With ICMP magic, you can snoop on vulnerable HiSilicon, Qualcomm-powered Wi-Fi
- Let there be light … based wireless networks: LiFi spec OK’d as Wi-Fi complement
Side-channel attacks aimed at learning Wi-Fi passwords have are not new, the boffins say, noting that these have involved acoustic measurements, indirect vision (reading passwords from eye movements), and motion sensors, among other techniques. But these have practical limitations and remain largely academic exercises, it’s claimed.
One side channel that doesn’t have these obstacles to practical use is Wi-Fi CSI (channel state information), which the researchers say can also be used to infer passwords through signal measurements.
CSI exploitation is described in a 2015 paper [PDF], “Keystroke Recognition using WiFi Signals,” and in a 2016 paper that describes the WindTalker attack, “When CSI Meets Public WiFi: Inferring Your Mobile Phone Password via WiFi Signals,” among others.
The eggheads in China and Singapore say that evolving Wi-Fi technology has meant that CSI eavesdropping isn’t particularly easy as it may require hacking or special hardware. BFI, they assert, is easier and has advantages in terms of being less sensitive to channel variation that make it hard to infer keystrokes.
The technique isn’t perfect and has limitations. The authors claim, “WiKI-Eve achieves 88 percent accuracy for identifying single numerical keys, and a top-100 accuracy of 85.0 percent for inferring a 6-digit numerical password.”
Note the term “numerical.” The focus of the research was on numeric passwords, because alphanumeric passwords are more complicated and are thus more difficult to decipher from BFI signals.
Stay in character(s)
When letters and numbers (but not special characters) are considered, WiKI-Eve manages to accurately classify 40 percent of keystrokes. But the technique, the researchers claim, outperforms other attacks such as WindTalker and WINK.
The distance of Bob, the victim, from the Wi-Fi access point also matters – average accuracy drops by about 23 percent when the distance increases from one meter to ten meters – though in this scenario Eve’s distance from the access point doesn’t matter.
“Consequently, Eve can eavesdrop stealthily from a long distance without compromising inference accuracy, clearly demonstrating the advantage of WiKI-Eve’s o-IKI method,” the researchers argue.
As for defenses, try encryption: using a password-protected Wi-Fi network will wrap the BFI frames in encryption, as we understand it, preventing others nearby from eavesdropping on the data. Sticking to private, protected wireless networks is generally recommended anyway.
“Since WiKI-Eve achieves keystroke eavesdropping by overhearing Wi-Fi BFI, the most direct defense strategy is to encrypt data traffic, hence preventing attackers from obtaining BFI in cleartext,” the researchers wrote. ®
Original Post URL: https://go.theregister.com/feed/www.theregister.com/2023/09/13/wifi_beamforming_side_channel_attack/
Category & Tags: –