Source: www.bleepingcomputer.com – Author: Bill Toulas

A ransomware operation targets Russian players of the Enlisted multiplayer first-person shooter, using a fake website to spread trojanized versions of the game.
Enlisted is a legitimate game published by Gaijin Entertainment in 2021, having between 500,000 and a million active monthly players.
The game is free, so threat actors could easily download the installer from the publisher and modify it to distribute malicious payloads to unsuspecting users.
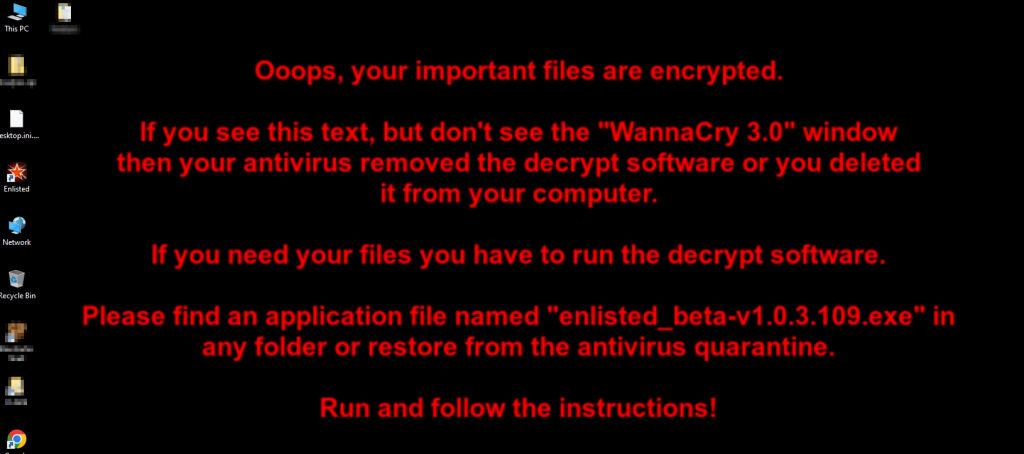
The ransomware bundled with the game installer pretends to be the third major version of the notorious WannaCry, even using the ‘.wncry’ file extension on encrypted files.
Conscripted into ransomware
According to Cyble’s researchers who analyzed the strain, this new “WannaCry” variant is based on the open-source ‘Crypter’ Python locker, of course, made for educational purposes.
It should be noted that this is not the first time someone has attempted to imitate WannaCry, probably to intimidate victims and secure a quick ransom payment.
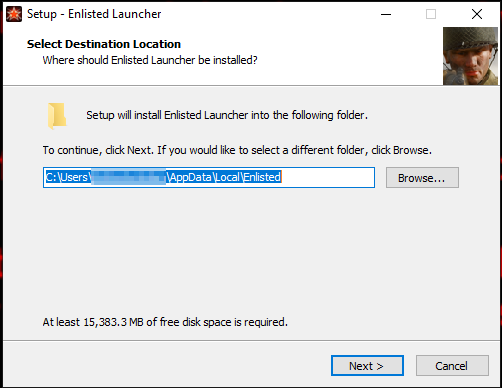
The installer downloaded from the fake website is “enlisted_beta-v1.0.3.115.exe,” which drops two executable files on the user’s disk if launched, namely “ENLIST~1” (the actual game) and “enlisted” (the Python ransomware launcher).
The ransomware creates a mutex upon initialization to avoid multiple running instances on the infected computer.
Then it parses its JSON configuration file, which determines what file types are targeted, which directories should be skipped, what ransom note to generate, which wallet address is to receive the ransom, and other attack parameters.
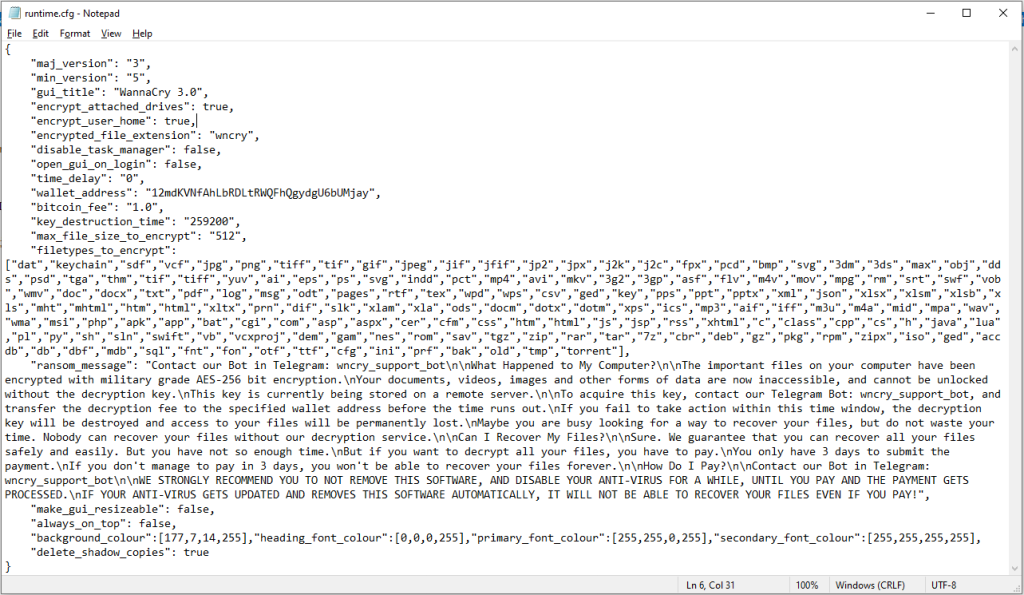
Next, the Crypter ransomware scans the working directory for a “key.txt” file to use in the encryption step, and if there isn’t one, it generates it.
The encryption uses the AES-256 algorithm, and all locked files receive the “.wncry” filename extension.
Interestingly, the ransomware does not attempt to terminate processes or stop services, which is standard practice in modern lockers.
However, it follows the common strategy of deleting the shadow copies from Windows to prevent easy data restoration.
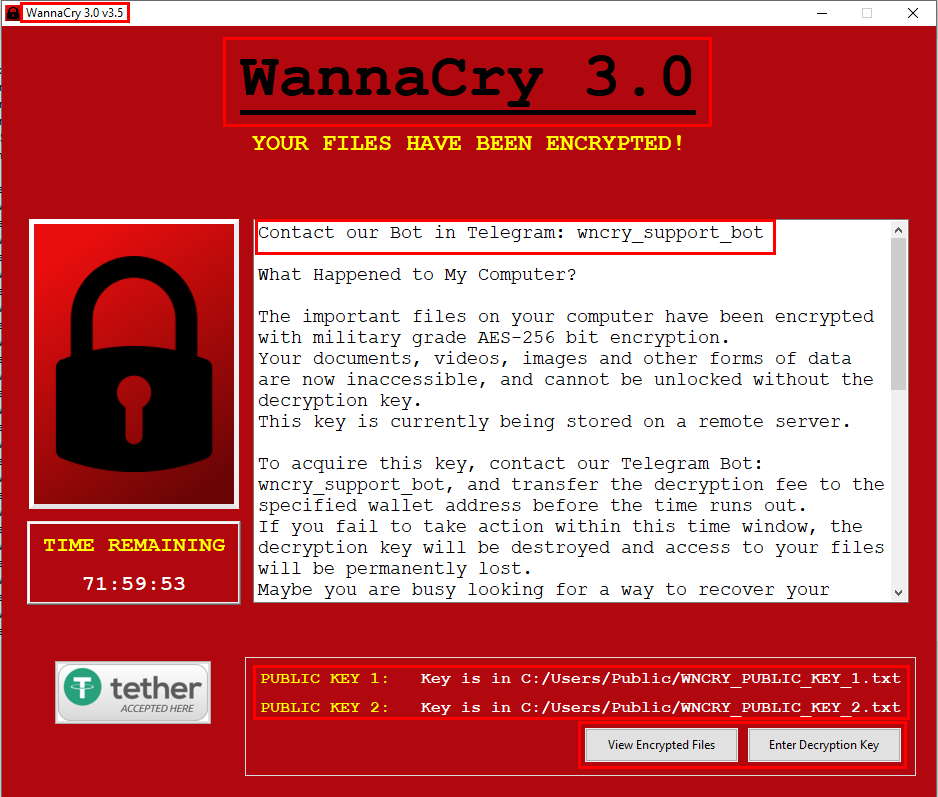
After the encryption process has been completed, the ransomware displays the ransom note on a dedicated GUI app, giving the victim three days to respond to the demands.
The threat actors also modify the victim’s background image to ensure their message gets across even if the victim’s antivirus blocks the launch of the GUI-based ransom note.
The attackers do not use a Tor site or provide a secure chat link to the victims but instead use a Telegram bot for communications.
National bans on popular FPS titles in Russia have forced local gamers to look elsewhere for entertainment, and Enlisted is one of the explored alternatives.
It appears that threat actors have jumped onto this opportunity, and it’s not unlikely they will create other fake sites for similar games with Russian localization.
Original Post URL: https://www.bleepingcomputer.com/news/security/fake-wannacry-ransomware-targets-russian-enlisted-fps-players/
Category & Tags: Security,Gaming – Security,Gaming




















































