Source: go.theregister.com – Author: Team Register
In seizing and dismantling LockBit’s infrastructure, Western cops are now making a mockery of the ransomware criminals by promising a long, drawn-out disclosure of the gang’s secrets.
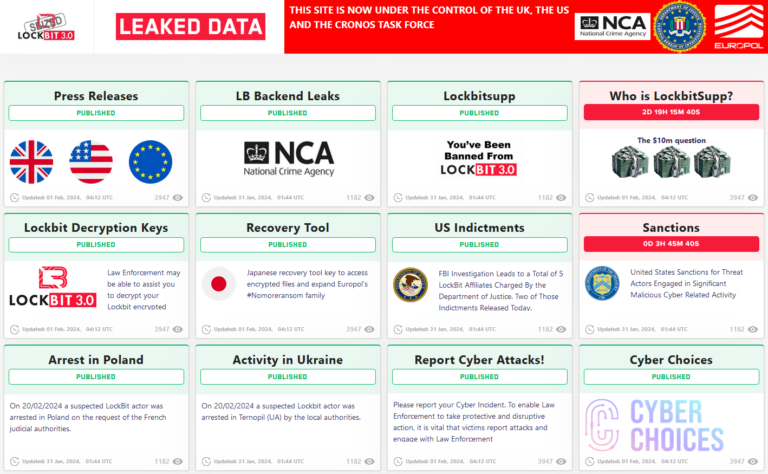
After the infosec world was invigorated by the announcement of LockBit’s site being seized yesterday, the authorities involved in the takedown operation – dubbed Operation Cronos – have now completely taken over the extortionists’ dark-web leak site and turned it into an exposé hub.
The site retains the same general format it did when it displayed all of the group’s victims, but instead of children’s hospitals, schools, and charities, each post now leads to new revelations about the case with more to come.
The UK’s National Crime Agency (NCA) is the authority that has taken control of LockBit’s site and administration environment, and is the body behind the slow dissemination of information throughout this week.
In typical LockBit style, its countdown timers have been hijacked to reveal the times at which various pieces of information will be revealed, including what appears to be the identity of LockBit’s leader. Nobody does a middle finger – digital or analog – quite like the British.
While we wait for the rest of the information to trickle out, the ten authorities involved in Cronos said today that two arrests of LockBit affiliates have been made in Ukraine and Poland.
It builds upon the previous two made by the US and Canada in recent years. Both Mikhail Vasiliev and Ruslan Magomedovich Astamirov, arrested in 2022 and 2023 respectively, remain in custody and await trial in the US for their roles in developing and deploying LockBit ransomware.
The US Department of Justice (DoJ) also unsealed an indictment today charging Russian nationals Artur Sungatov and Ivan Kondratyev with deploying LockBit ransomware against US victims.
These are just indictments, though, and unless the pair are silly enough to venture out of Russia, which will never extradite its people to the US, and into a country with a US extradition agreement, it’s likely they’ll never see the inside of a US prison.
Making key arrests is the toughest aspect of disrupting ransomware operations since many criminals reside in Russia, China, Iran, and North Korea – countries that also won’t extradite their own to the US to face trial.
Arresting a few affiliates may feel like a win for law enforcement, but it rarely offers the significant impact it may suggest on the surface.
Unless the leadership team and brains behind the operations are captured, the rinse-repeat cycle of ransomware gangs going dark for a few months only to return under a new guise will continue.
LockBit was active for more than four years. Disrupting ransomware gangs involves a great deal of effort from the top minds of many countries working together, and they often cannot keep pace with the rate at which ransomware groups emerge.
However that shouldn’t put too much of a dampener on what was achieved with Lockbit, which has been the most prolific ransomware gang for the past two years, netting more than $120 million in ransom payments and extorting more than 2,000 victims. It’s great news they’ve been taken down.
Plus, if they do try to come back, the NCA’s director general Graeme Biggar offered some fighting talk.
“Our work does not stop here,” he said. “LockBit may seek to rebuild their criminal enterprise. However, we know who they are, and how they operate. We are tenacious and we will not stop in our efforts to target this group and anyone associated with them.”
Among the other headline revelations today, the Cronos team said 34 LockBit servers have been taken down in the Netherlands, Germany, Finland, France, Switzerland, Australia, the US, and the UK.
Among these servers were three hosted in the US that were responsible for hosting LockBit’s StealBit data exfiltration malware used by affiliates during attacks.
More than 200 cryptocurrency accounts were also frozen and a “vast amount of data” was gathered after taking control of the operation’s backend. This includes more than 1,000 decryption keys. UK victims will be contacted directly by the NCA while those in the US are advised to visit the new dedicated FBI portal to determine whether their files can be decrypted.
In addition, decryptors will be added to Europol’s “No More Ransom” portal and made available in 37 languages.
“The NCA has also obtained the LockBit platform’s source code and a vast amount of intelligence from their systems about their activities and those who have worked with them and used their services to harm organizations throughout the world,” the NCA said.
In analyzing this data, it also found evidence of data held on victims that had paid ransoms, exemplifying why victims cannot trust criminals to delete their data, as they often promise, once a ransom is paid.
- LockBit ransomware gang disrupted by global operation
- Infosys subsidiary named as source of Bank of America data leak
- LockBit shows no remorse for ransomware attack on children’s hospital
- Subway’s data torpedoed by LockBit, ransomware gang claims
“This operation demonstrates both our capability and commitment to defend our nation’s cybersecurity and national security from any malicious actor who seeks to impact our way of life,” said FBI director Christopher A Wray.
“We will continue to work with our domestic and international allies to identify, disrupt, and deter cyber threats, and to hold the perpetrators accountable.”
What to expect this week
As the NCA said, more information about the LockBit operation is slated to be released day by day this week, and it includes some interesting stuff.
Tomorrow, February 21, the countdown timers are set to unlock information about LockBit’s affiliate infrastructure, how StealBit worked, and more information about the gang’s affiliates.
The following day will see information about “account closures” (not much else to go on there), and what appears to be an assortment of technical reports from Trend Micro, Prodaft, and Secureworks.
It’s all going to culminate on Friday, February 23, with what appears to be the grand reveal of LockBitSupp’s identity.
The public spokesperson for and presumed leader of the ransomware gang has previously said they would pay $1 million to anyone who could send LockBitSupp’s real full name over a direct message.
Also being revealed are further insights into LockBit’s frozen and analyzed cryptocurrency wallets, including details about the amount of profit it generated over its time in business.
At 2300 UTC on Saturday, February 24, the NCA’s final action will be to shut down the site for good. So get those laughs in and marvel at the brilliantly defaced site while you still can.
What about the rumors?
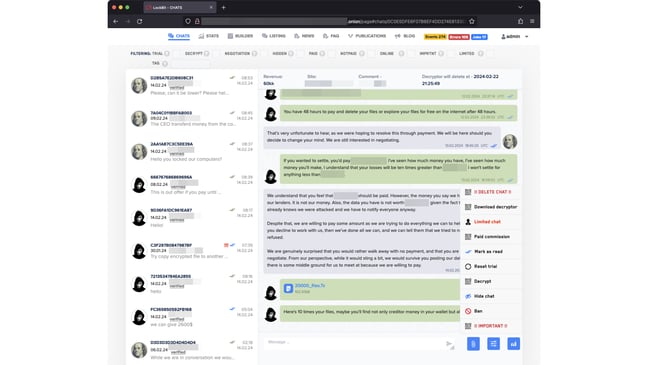
According to alleged messages exchanged between LockBit and malware collectors vx-underground, LockBit believes only servers running PHP elements were impacted and that its backups were untouched, which could mean a recovery is on the cards.
“LockBit have proven themselves in the past to be a resilient ransomware variant, surviving major leaks and rebrands, we do not yet know the impact that these takedowns will have on operations,” said Tim West, director of threat intelligence and outreach at WithSecure.
“LockBit themselves are claiming that only servers running PHP elements were impacted, data is safe, and backup servers were unaffected which, if true, will probably mean Lockbit (as well-resourced actors) can recover fairly swiftly.”
LockBit also claimed that law enforcement was able to break into the criminals’ servers by exploiting CVE-2023-3824, a buffer overflow vulnerability in PHP that can lead to remote code execution. This has not been confirmed by authorities.
If LockBit is able to recover, it will be the second failed major ransomware takedown in recent months after the FBI’s attempt to shutter ALPHV/BlackCat led to the criminals taking back control of their infrastructure within a few days. Pretty embarrassing stuff, especially given the press releases lauding the effort were distributed while the wrestle for control was still ongoing.
However, given the degree to which we can already see the NCA taking over LockBit’s site, West at WithSecure said perhaps a more likely scenario is one where LockBit is unaware of the extent to which it’s been compromised and won’t ever recover.
“One thing we do know is the collective of law enforcement agencies will certainly have carefully weighed short-term and long-term impact opportunity to ensure maximum disruption and impose maximum cost on LockBit and we support any and all action that dents or impedes their continued operation,” West added.
“For this reason, we celebrate what would no doubt have been a complex and difficult operation and offer congratulations to those involved.” ®
Original Post URL: https://go.theregister.com/feed/www.theregister.com/2024/02/20/nca_lockbit_takedown/
Category & Tags: –