Imagine you live in Russia and want to use the Tor browser to anonymise your browsing of the web.
There’s a problem. Many people in Russia find their access to the official Tor website is blocked by their ISP.
So, what do you do?
Well, you could try to find somewhere other than the official Tor website to download Tor from.
But is the version of Tor you downloaded from a torrent or third-party site trustworthy?
According to a report from Russian anti-virus outfit Kaspersky, perhaps not.
Kaspersky boffins say that they have seen malware distributed as copies of Tor, which has stolen approximately US $400,000 worth of cryptocurrency from almost 16,000 users worldwide.
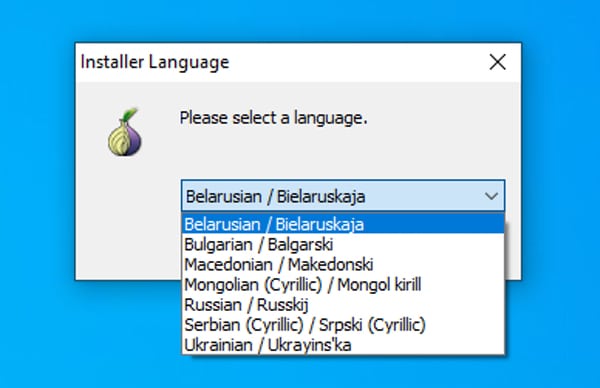
According to the researchers, boobytrapped installers offer Tor with a selection of regional language packs, including Russian.
Once installed, the malware snoops on your Windows clipboard.
If it sees in your clipboard what it believes to be an address for a cryptocurrency wallet, it replaces it with an address controller by the attacker.
The upshot is that you might think you are moving cryptocurrency into your own wallet, but in fact you’re putting it into the hands of a cybercriminal.
Ouch.
I was amused to see the team at Kaspersky suggest a simply method to check whether you system was compromised:
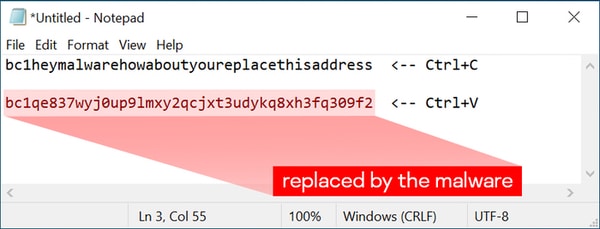
Type or copy the following “Bitcoin address” in Notepad:
bc1heymalwarehowaboutyoureplacethisaddressNow press Ctrl+C and Ctrl+V. If the address changes to something else — the system is likely compromised by a clipboard-injector type of malware, and is dangerous to use.
I don’t think I’d rely on that test alone to tell if my computer was compromised by the clipboard-injecting malware, but it’s an interesting thing to try.
If you’re in any doubt, it’s perhaps safest to always assume your computer is compromised.
Found this article interesting? Follow Graham Cluley on Twitter or Mastodon to read more of the exclusive content we post.
Graham Cluley is a veteran of the anti-virus industry having worked for a number of security companies since the early 1990s when he wrote the first ever version of Dr Solomon’s Anti-Virus Toolkit for Windows. Now an independent security analyst, he regularly makes media appearances and is an international public speaker on the topic of computer security, hackers, and online privacy.
Follow him on Twitter at @gcluley, on Mastodon at @[email protected], or drop him an email.





















































