Source: www.cyberdefensemagazine.com – Author: Gary Zero Trust: The Unsung Hero of Cybersecurity Cybersecurity professionals are drowning in complexity. Acronyms fly like digital confetti, vendors promise silver...
Author: CISO2CISO Editor 2
Innovator Spotlight: NetBrain – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Network Visibility: The Silent Guardian of Cybersecurity Network complexity is killing enterprise security teams. Buried under mountains of configuration data, manual...
Innovator Spotlight: Adaptive Security – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary The AI Threat Landscape: How Adaptive Security is Redefining Cyber Defense Cybersecurity professionals are facing an unprecedented challenge. The rise of...
Innovator Spotlight: Portnox – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Network Security Reimagined: How Portnox is Solving the NAC Nightmare Security professionals have long wrestled with network access control (NAC) solutions...
Datenpanne bei Palo Alto Networks, Zscaler und Cloudflare – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die drei Anbieter betonen, dass nicht sie selbst, sondern ein Drittanbieter angegriffen wurden. Betroffen sind ihre Kunden aber allemal. Auch IT-Unternehmen, selbst...
Avnet unlocks vendor lock-in and reinvents security data management – Source: www.csoonline.com
Source: www.csoonline.com – Author: The global distributor decided to take ownership of its security data, liberating engineers and cutting costs. As a leading distributor of electronic...
Principal Financial pioneers biometric authentication to beat online fraud – Source: www.csoonline.com
Source: www.csoonline.com – Author: By swapping knowledge-based questions for biometrics, Principal shut down account takeovers and boosted customer trust. Principal Financial Group helps millions of people...
Automobilbranche fürchtet sich vor Cyberattacken – Source: www.csoonline.com
Source: www.csoonline.com – Author: Editorial Manager CSO Online Deutschland News-Analyse 4. Sept. 20252 Minuten AutomobilbrancheCyberangriffe Die zunehmende Gefahr durch Cyberangriffe bereitet der deutschen Autoindustrie große Sorgen....
Pressure on CISOs to stay silent about security incidents growing – Source: www.csoonline.com
Source: www.csoonline.com – Author: A recent survey found that 69% of CISOs have been told to keep quiet about breaches by their employers, up from 42%...
Malicious npm packages use Ethereum blockchain for malware delivery – Source: www.csoonline.com
Source: www.csoonline.com – Author: Ethereum smart contracts used to hide URL to secondary malware payloads in an attack chain triggered by a malicious GitHub repo. Attackers...
Relief for European Commission as court upholds EU Data Privacy Framework agreement with US – Source: www.csoonline.com
Source: www.csoonline.com – Author: Legal challenge by French MP rejected by the EU’s General Court, but experts predict ruling will be appealed. The controversial Data Privacy...
Sola Security Raises $35M to Bring No-Code App Building to Cybersecurity Teams – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Israeli startup Sola Security has raised a $35 million Series A round, the company announced Thursday, which brings the total...
Threat Actors Abuse Hexstrike-AI Tool to Accelerate Exploitation – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new agentic AI-powered tool for red teams is already being abused by threat actors to rapidly accelerate and simplify vulnerability exploitation,...
Healthcare Sector Takes 58 Days to Resolve Serious Vulnerabilities – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Healthcare organizations (HCOs) are among the slowest at remediating serious vulnerabilities, leaving systems and data exposed for weeks or even months, according...
Is a Recent Windows Update Responsible for SSD Failures? Microsoft Has an Answer – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: J.R. Johnivan Published September 4, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
‘Unprecedented Growth’ by Anthropic: This AI Startup is Now Valued at $183B – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Topic — Artificial Intelligence Published September 3, 2025 Claude AI creator Anthropic plans to use the money from its latest...
Google Says Claims of Mass Gmail Security Breach Are ‘Entirely False’ – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
Iran MOIS Phishes 50+ Embassies, Ministries, Int’l Orgs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer The Homeland Justice APT tried spying on countries and organizations from six continents, using more than 100 hijacked...
Japan, South Korea Take Aim at North Korean IT Worker Scam – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer With the continued success of North Korea’s IT worker scams, Asia-Pacific nations are working with private firms to...
Russia’s APT28 Targets Microsoft Outlook With ‘NotDoor’ Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright The notorious Russian state-sponsored hacking unit, also known as Fancy Bear, is abusing Microsoft Outlook for covert data exfiltration. Original...
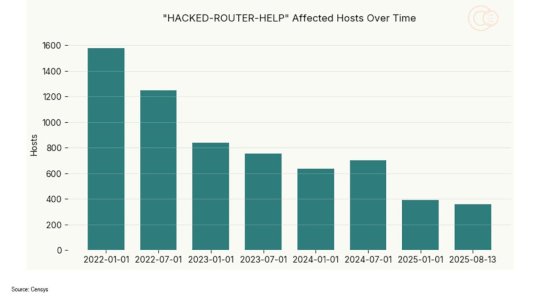
Hacked Routers Linger on the Internet for Years, Data Shows – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid While trawling Internet scan data for signs of compromised infrastructure, researchers found that asset owners may not know for...
WhatsApp Bug Anchors Targeted Zero-Click iPhone Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer A “sophisticated” attack that also exploits an Apple zero-day flaw is targeting a specific group of iPhone users,...
Critical Insight Q&A: As digital trust compresses, resilience will require automation and scale – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido A quiet but consequential change is reshaping the foundations of online trust. Related: CISA on quantum readiness...
California Tax Refund Mobile Phish – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gary Warner A new round of mobile phish is imitating the State of California’s “Franchise Tax Board” in a round of phishing...
Why Misconceptions About Cloud Managed Services Can Cost You – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mary Henry Scaling Kubernetes isn’t just about launching containers—it’s about choosing support models that truly let developers innovate instead of drowning in...
Salesloft Drift Breach Rolls Up Cloudflare, Palo Alto, Zscaler and Others – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Cloudflare, Palo Alto Networks, and Zscaler are the latest among hundreds of victims of an expanding data-stealing attack by the...
Survey Surfaces Raft of WordPress Cybersecurity Concerns – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A survey of 264 professionals that maintain websites based on the WordPress content management system (CMS) finds 96% have been...
Goldilocks: An Open Source Tool for Recommending Resource Requests – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Suderman One of the questions that I get most frequently from our clients at Fairwinds is “How do we know what...
What’s New in Active Threats: Threat of the Month, New AI Search, and Improved Performance – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk SOC Prime’s latest release advances AI-native cybersecurity workflows with milestone updates to Active Threats, which now ingests and aggregates more...
What’s New in Uncoder: AI Chat Bot & MCP Tools – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk SOC Prime’s latest release is focused on improving AI-native cybersecurity workflows, bringing new capabilities to Uncoder AI. Key updates include...