Source: www.cyberdefensemagazine.com – Author: News team Data breach costs are rising at breakneck speed. IBM reported that the global average security breach cost is $4.9 million, marking...
Author: CISO2CISO Editor 2
The Cost of Ignoring Patches: How State and Local Governments Can Mitigate Damaging Security Breaches – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team According to a recent report released by the Multi-State Information Sharing and Analysis Center, governmental agencies are facing an increase in...
Small Manufacturers, Big Target: The Growing Cyber Threat and How to Defend Against It – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Digital transformation in manufacturing has opened doors to promising possibilities, but not without new risk exposure. With expansive transformation comes...
Securing the Connected Factory Floor – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team As manufacturers strive to keep pace with changing demands and quickly evolving technologies, many are embracing digitalization and increased connectivity...
On Constant Community Improvements – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Stevin The theme of this year’s RSAC is “Many Voices. One Community.” While our field can rightly claim “many voices”, portraying it...
One Piece of the Puzzle: How a Single Digital Identifier Can Unravel Your Entire Online Life – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In an era where our lives are increasingly lived online, our digital identities are sprawling networks of accounts and personal...
Modernizing Critical Infrastructure Security to Meet Today’s Threats – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Ransomware attacks are no longer just a cybersecurity concern – they are a direct threat to national security. A recent study found...
Scaling Smart: Federal Leaders Prioritize AI Security and Resilience – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The biggest threat to artificial intelligence (AI) in government isn’t hype – it’s inertia. As Federal agencies explore opportunities to...
Implementing Effective AI Guardrails: A Cybersecurity Framework – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team As organizations race to implement AI solutions, security leaders face the challenge of enabling progress while protecting sensitive data. Grand Canyon...
How to Use Risk Management to Strengthen Business Cybersecurity – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Cybersecurity is a massive point of emphasis for most businesses in the modern age. You must work diligently to protect...
Critical Vulnerability Exposes Many Mitel MiCollab Instances to Remote Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Mitel this week informed customers about the availability of patches for a critical MiCollab vulnerability that can be exploited remotely...
UK ‘woefully’ unprepared for Chinese and Russian undersea cable sabotage, says report – Source: www.theguardian.com
Source: www.theguardian.com – Author: Patrick Wintour China and Russia are stepping up sabotage operations targeting undersea cables and the UK is unprepared to meet the mounting...
How Can NHIs Enhance Overall System Security? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Can NHIs Serve as the Crucial Backbone in Overall System Protection? What if there was a foolproof method for...
Why Proactive NHI Management is a Must? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Is Proactive NHI Management Our Best Bet Against Cyber Threats? The importance of non-human identities (NHIs) in cybersecurity cannot be...
Are Your Cloud Secrets Safe From Threats? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why Is Secrets Management Crucial for Your Cloud Environment? Do you think your cloud infrastructure is immune to threats? If...
Secure Your Machine Identities Effectively – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why are Machine Identities Crucial to Cybersecurity Strategies? How often do we ruminate about the myriad of digital interactions happening...
Top 10 Challenges Implementing DMARC in GWS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Audian Paxson Let’s talk about the real story behind Google’s DMARC maze, shall we? (You might want to go pour yourself a...
LinuxFest Northwest: See How Far COSMIC Has Come This Year – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenter: Carl Richell (CEO and Founder, System76, Inc.) Our sincere appreciation to LinuxFest Northwest (Now Celebrating Their Organizational 25th Anniversary...
OAuth 2.0 Security Best Practices: How to Secure OAuth Tokens & Why Use PKCE – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajveer Singh Introduction Keeping your applications secure while offering a smooth user experience can be tricky — especially when working with OAuth...
TeamFiltration Abused in Entra ID Account Takeover Campaign – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A large-scale account takeover (ATO) campaign has been abusing the TeamFiltration penetration testing framework to target Entra ID users, Proofpoint...
Friday Squid Blogging: Stubby Squid – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Stubby Squid Video of the stubby squid (Rossia pacifica) from offshore Vancouver Island. As usual, you...
New Way to Covertly Track Android Users – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Researchers have discovered a new way to covertly track Android users. Both Meta and Yandex were using it, but have...
Dutch police identify users as young as 11-year-old on Cracked.io hacking forum – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Dutch police have announced that they have identified 126 individuals linked to the now dismantled Cracked.io cybercrime forum. Cracked.io was...
CISA Reveals ‘Pattern’ of Ransomware Attacks Against SimpleHelp RMM – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
DNS Rebind Protection Revisited – Source: securityboulevard.com
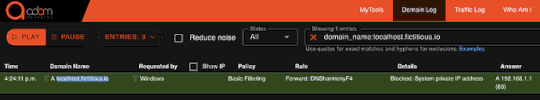
Source: securityboulevard.com – Author: David After this week’s attention to META and Yandex localhost abuses, it is time to revisit a core feature/option of protective DNS...
News alert: Arsen launches AI-powered vishing simulation to help combat voice phishing at scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Paris, Jun. 3, 2025, CyberNewswire–Arsen, the cybersecurity startup known for defending organizations against social engineering threats, has announced the release of...
LinuxFest Northwest: Chaos Testing Of A Postgres Cluster On Kubernetes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenter: Nikolay Sivko (Co-Founder And CEO At Coroot) Our sincere appreciation to LinuxFest Northwest (Now Celebrating Their Organizational 25th Anniversary...
Shadow AI: Examples, Risks, and 8 Ways to Mitigate Them – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mend.io Team What is Shadow AI? Shadow AI refers to the unauthorized or unmanaged use of AI tools, models, frameworks, APIs or...
Meta AI is a ‘Privacy Disaster’ — OK Boomer – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Pundits accuse Zuckerberg’s latest app of having a “dark pattern,” tricking the over 50s into oversharing. The Meta AI app’s public...
HR’s 2025 Guide to Preventing Interview and Onboarding Fraud – Source: securityboulevard.com
Source: securityboulevard.com – Author: Vy Chen A Wake-Up Call for HR in the Age of Deepfakes and Remote Work In 2025, HR leaders are facing a...