Source: securityboulevard.com – Author: Dev Kumar Imagine you’re building a sophisticated apartment complex that needs to accommodate thousands of different businesses, each with their own unique...
Author: CISO2CISO Editor 2
Randall Munroe’s XKCD ‘Alert Sound’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, June 17, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
LinuxFest Northwest: Beyond ARIA Labels What A Blind Film Enthusiast Can Teach Us About Open Source – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: José Ibañez (CEO at Blind Penguin), Raissa Ibañez (Manager At Blind Penguin) Our sincere appreciation to LinuxFest Northwest (Now...
The founder’s survival guide to B2B SaaS growth – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author Here’s the brutal truth: 90% of B2B SaaS companies fail because founders try to scale...
Automated Guard Rails for Vibe Coding – Source: securityboulevard.com
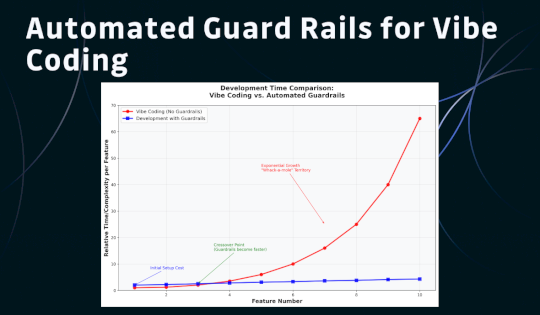
Source: securityboulevard.com – Author: Andy Rea There are countless warnings and horror stories about “vibe coding”—that flow state where you’re cranking out features and everything feels...
App Store Security Threats in 2025: Why Hackers Target Mobile Ecosystems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alex Vakulov Mobile devices are now the primary gateway to the digital world. From banking to healthcare, users rely on apps for...
Washington Post Journalists’ Microsoft Email Accounts Hacked – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Several journalists with The Washington Post were targeted in a cyberattack that compromised their Microsoft email accounts, an echo of...
GUEST ESSAY: The AI illusion: Don’t be fooled, innovation without guardrails is just risk–at scale – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Artificial intelligence is changing everything – from how we search for answers to how we decide who gets hired, flagged, diagnosed,...
Ongoing Money Laundering Insights – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Abstract Money laundering is a major financial crime that involves introducing illicitly obtained funds into legitimate financial systems to disguise...
The Impact of Quantum Decryption – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Executive Summary Quantum computing’s rapid progress poses a significant threat, potentially rendering current encryption methods and nearly all encrypted data...
High-Severity Vulnerabilities Patched in Tenable Nessus Agent – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Tenable has released patches for three high-severity vulnerabilities in Nessus Agent for Windows that could be exploited to perform file...
CVE-2025-4123 Vulnerability: “The Grafana Ghost” Zero-Day Enables Malicious Account Hijacking – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko WRITTEN BY Veronika Telychko Technical Writer [post-views] June 16, 2025 · 5 min read June has been a turbulent month...
What Are the Predictions of AI in Cybersecurity? – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko According to Gartner, by 2029, agentic Artificial Intelligence (AI) will autonomously handle 80% of routine customer service inquiries, cutting operational...
New quantum system offers publicly verifiable randomness for secure communications – Source: www.csoonline.com
Source: www.csoonline.com – Author: Quantum breakthrough delivers verifiable randomness as researchers develop globally scalable ‘uncheatable’ system rooted in physics rather than algorithms. In our digital world,...
Erster Zero-Click-Angriff auf Microsoft 365 Copilot – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 16. Juni 20255 Minuten Eine einzige E-Mail kann Copilot unbemerkt dazu bringen, sensible Unternehmensdaten zu exfiltrieren – ohne Klicks, ohne Warnungen,...
‘Grafana Ghost’ XSS flaw exposes 47,000 servers to account takeover – Source: www.csoonline.com
Source: www.csoonline.com – Author: The vulnerability enables attackers to load malicious plugins, hijack sessions, and create administrative accounts on unpatched systems. A newly discovered cross-site scripting...
Cyberangriff auf „Washington Post“ – Source: www.csoonline.com
Source: www.csoonline.com – Author: Hacker haben Journalisten der „Washington Post“ angegriffen. Die Täter könnten aus China stammen. Die “Washington Post” wurde Ziel einer Cyberattacke. Dennis Diatel...
Salesforce Industry Cloud riddled with configuration risks – Source: www.csoonline.com
Source: www.csoonline.com – Author: AppOmni researchers found 20 insecure configurations and behaviors in Salesforce Industry Cloud’s low-code app building components that could lead to data exposure....
What CISOs are doing to lock in cyber talent before they bolt – Source: www.csoonline.com
Source: www.csoonline.com – Author: As perks and pay only go so far, CISOs are turning to upskilling and career pathways to benefit both cyber professionals and...
Operationelle Resilienz – Koordination & Kooperation im Fokus – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISOs sollten operationelle Resilienz als strategisches Führungsziel etablieren. Um Unternehmen auf Cybervorfälle vorzubereiten, brauchen CISOs operationelle Resilienz. https://www.shutterstock.com/g/AndryDj Die Aufgabe des CISOs...
‘Water Curse’ Targets Infosec Pros Via Poisoned GitHub Repositories – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Security Is Only as Strong as the Weakest Third-Party Link – Source: www.darkreading.com
Source: www.darkreading.com – Author: Shimon Modi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
NIST Outlines Real-World Zero-Trust Examples – Source: www.darkreading.com
Source: www.darkreading.com – Author: Fahmida Y. Rashid Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
Drive Innovation Through Advanced NHI Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why is Advanced NHI Management Crucial for Driving Innovation? Where data is the new gold, organizations must ensure the safety...
Scalable Secrets Management for Growing Businesses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why is NHI Management Crucial for Growing Businesses? Growing businesses face the continuous challenge of ensuring their cybersecurity measures scale...
Gain Full Control Over Your Digital Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why does Digital Identity Control Matter in Cybersecurity? Do you fully control your digital identities? Managing Non-Human Identities (NHIs) and...
Introducing Guernsey Cyber Security Centre – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Palmer Since 2021, I’ve been building Jersey Cyber Security Centre (JCSC). As a cyber defence capability for an island state and...
LinuxFest Northwest: Clonezilla Live On RISC-V Crafting Open Source Live Systems For Open Hardware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Steven Shiau (Clonezilla Project Leader); Yu-Chin Tsai (Clonezilla NCHC Partclone); Chen-Kai Sun (Clonezilla Project / Engineer In NCHC) Our...
Guardrails Breached: The New Reality of GenAI-Driven Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity Lohrmann on Cybersecurity From vibe hacking to malware development to deepfakes, bad actors are discovering more vulnerabilities to attack...
EU AI ACT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deborah Erlanger What is the EU AI Act? The EU AI Act (European Union Artificial Intelligence Act) is the world’s first comprehensive...