Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Haiming Wang, Zhikun Zhang, Tianhao Wang, Shibo He, Michael Backes, Jiming Chen, Yang Zhang Many thanks to USENIX for...
Author: CISO2CISO Editor 2
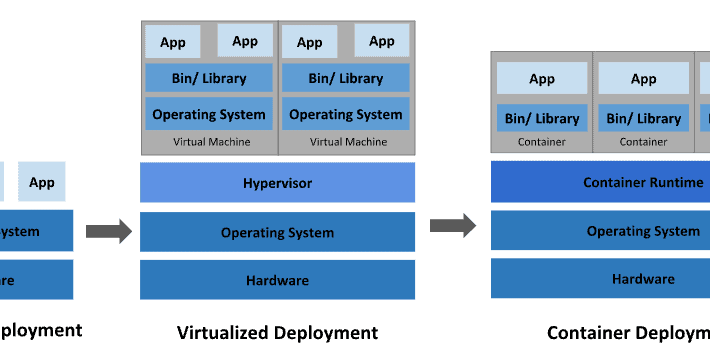
How To Monitor Kubernetes Audit Logs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelsey Gast In today’s fast-paced landscape of container orchestration, Kubernetes is a powerful tool for managing and scaling applications. However, ensuring the...
Learn the Most Essential Cybersecurity Protections for Schools – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith Malicious actors and hacker groups are actively targeting schools. According to reports, there has been a 146% increase in malware...
How ITDR Could Have Helped Microsoft in the Midnight Blizzard Hack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rezonate Identity-based attacks are on the rise, but they can be prevented with the right identity threat detection and response (ITDR) measures. ...
AppSec vendors and CISOs: a love-hate relationship? ⎜Olivia Rose – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Charikova Welcome to the Elephant in AppSec, the podcast to explore, challenge, and boldly face the AppSec Elephants in the room....
Randall Munroe’s XKCD ‘Research Account’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
The Strategic Partnership Elevating API and Endpoint Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tony Bradley Salt Security has announced a pivotal partnership with CrowdStrike. This collaboration marks a significant milestone for businesses seeking robust, integrated...
The Coming End of Biometrics Hastens AI-Driven Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Gallagher Until recently I thought we had a lot of time ahead of us to be secure in using biometrics to...
Complexity and software supply chain security: 5 key survey takeaways – Source: securityboulevard.com
Source: securityboulevard.com – Author: John P. Mello Jr. Organizations are struggling with software supply chain security. That fact was further exposed this month with the Enterprise...
Sophos’ Kris Hagerman Steps Down as CEO, Joe Levy Takes Helm – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Managed Detection & Response (MDR) Hagerman Moves to Advisory Role After Leading Company...
OpenAI and Microsoft Terminate State-Backed Hacker Accounts – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Hackers Used LLMs to Perform Tasks That Non-AI Tools Can...
6 Categories of Modern Threat Landscape | Empowering Business Continuity for Cyber Resilience – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Darren Thomson Field CTO – Security, EMEAI, Commvault Darren is the Field CTO for Security covering EMEA and India, where he...
Harnessing Exploitability Information for Effective Prioritization – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , DevSecOps , Next-Generation Technologies & Secure Development Presented by Mend.io 60 minutes Do you...
Breach Roundup: Zeus Banking Trojan Leader Pleads Guilty – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Also: Polish Prime Minister Says Previous Administration Deployed Pegasus Spyware...
To Avoid Bankruptcy, EMR Firm Settles Lawsuit for $4M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Industry Specific , Legislation & Litigation Pediatric Tech Vendor Hit by 2022 Data Breach Affecting 3 Million – Mostly...
On the Insecurity of Software Bloat – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Good essay on software bloat and the insecurities it causes. The world ships too much code, most of it by...
Microsoft says it fixed a Windows Metadata server issue that’s still broken – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft claims to have fixed Windows Metadata connection issues which continue to plague customers, causing problems for users trying to...
US offers up to $15 million for tips on ALPHV ransomware gang – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. State Department is offering rewards of up to $10 million for information that could lead to the identification...
RansomHouse gang automates VMware ESXi attacks with new MrAgent tool – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The RansomHouse ransomware operation has created a new tool named ‘MrAgent’ that automates the deployment of its data encrypter across multiple VMware...
FBI disrupts Moobot botnet used by Russian military hackers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The FBI took down a botnet of small office/home office (SOHO) routers used by Russia’s Main Intelligence Directorate of the...
OpenAI blocks state-sponsored hackers from using ChatGPT – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas OpenAI has removed accounts used by state-sponsored threat groups from Iran, North Korea, China, and Russia, that were abusing its...
Over 13,000 Ivanti gateways vulnerable to actively exploited bugs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Thousands of Ivanti Connect Secure and Policy Secure endpoints remain vulnerable to multiple security issues first disclosed more than a...
Three critical application security flaws scanners can’t detect – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 In today’s interconnected world, web application security is crucial for business continuity. Yet, web application attacks are now involved...
Turla hackers backdoor NGOs with new TinyTurla-NG malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Security researchers have identified and analyzed new malware they call TinyTurla-NG and TurlaPower-NG used by the Russian hacker group Turla...
New Qbot malware variant uses fake Adobe installer popup for evasion – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The developer of Qakbot malware, or someone with access to the source code, seems to be experimenting with new builds as fresh samples...
New ‘Gold Pickaxe’ Android, iOS malware steals your face for fraud – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new iOS and Android trojan named ‘GoldPickaxe’ employs a social engineering scheme to trick victims into scanning their faces...
Rhysida ransomware cracked! Free decryption tool released – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley Good news for organisations who have fallen victim to the notorious Rhysida ransomware. A group of South Korean security researchers...
North Korea successfully hacks email of South Korean President’s aide, gains access to sensitive information – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The office of South Korean president Yoon Suk Yeol has confirmed that it believes North Korea hacked into the emails...
Smashing Security podcast #359: Declaring war on ransomware gangs, mobile muddles, and AI religion – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Holy mackerel! AI is jumping on the religion bandwagon, ransomware gangs target hospitals, and what’s happened to your old mobile...
Russian APT Turla Wields Novel Backdoor Malware Against Polish NGOs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Science Photo Library via Alamy Stock Photo Russia-sponsored advanced persistent threat group (APT) Turla is now targeting...