Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Vegan Squid-Ink Pasta It uses black beans for color and seaweed for flavor. As usual, you...
Author: CISO2CISO Editor 2
CISO Corner: CIO Convergence, 10 Critical Security Metrics, & Ivanti Fallout – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Welcome to CISO Corner, Dark Reading’s weekly digest of articles tailored specifically to security operations...
What Using Security to Regulate AI Chips Could Look Like – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer Source: Science Photo Library via Alamy Stock Photo Researchers from OpenAI, Cambridge University, Harvard University, and University of...
Major Tech Firms Develop ‘Tech Accord’ to Combat AI Deepfakes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: WrightStudio via Adobe Stock In what is being referred to as a “Tech Accord,” major technology companies are...
Enterprises Worry End Users Will be the Cause of Next Major Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Edge Editors Source: Strategic Security Survey, Dark Reading The sheer volume of data breaches and cyberattacks means these incidents are now more...
Like Seat Belts and Airbags, 2FA Must Be Mandatory ASAP – Source: www.darkreading.com
Source: www.darkreading.com – Author: Aviad Mizrachi Source: Techa Tungateja via Alamy Stock Photo COMMENTARY One of the few pieces of information that is truly immutable and...
Iran Warship Aiding Houthi Pirates Hacked by US – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff 1 Min Read Source: Ivan Marc Sanchez US officials claim a recent cyberattack on an Iranian military spy ship...
JumpCloud’s Q1 2024 SME IT Trends Report Reveals AI Optimism Tempered by Security Concerns – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE LOUISVILLE, Colo. — JumpCloud Inc., today announced the findings from its Q1 2024 small to medium-sized enterprise (SME) IT Trends Report,...
Perforce to Acquire Delphix, Adding Enterprise Data Management Software to its DevOps Portfolio – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE MINNEAPOLIS, Feb. 14, 2024 /PRNewswire/ — Perforce Software (“Perforce”), a provider of solutions to enterprise teams requiring productivity, visibility, and scale along the development...
Cobalt’s New Report Uncovers a Big Shift in Cybersecurity Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SAN FRANCISCO, Feb. 14, 2024 /PRNewswire-PRWeb/ — Cobalt, the pioneers of Pentest as a Service (PtaaS), empowering businesses to operate fearlessly and innovate...
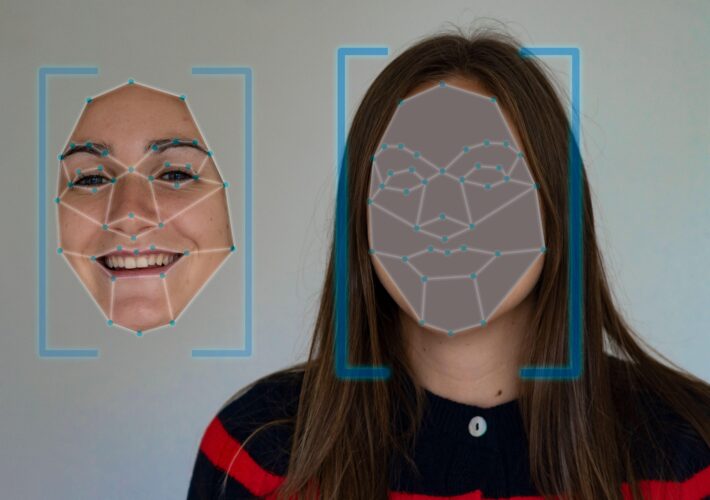
iOS, Android Malware Steals Faces to Defeat Biometrics With AI Swaps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Alfonso Fabio Iozzino via Alamy Stock Photo Chinese hackers have developed a sophisticated banking Trojan for tricking...
State Government Organization Network Breach: SafeBreach Coverage for US-CERT Alert (AA24-046A) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach On February 15th, the Cybersecurity and Infrastructure Security Agency (CISA) and the Multi-State...
USENIX Security ’23 – Xiangyu Qi, Tinghao Xie, Jiachen T. Wang, Tong Wu, Saeed Mahloujifar, Prateek Mittal – Towards A Proactive ML Approach for Detecting Backdoor Poison Samples – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Xiangyu Qi, Tinghao Xie, Jiachen T. Wang,...
Love in the Age of AI: Navigating Online Dating Scams this Valentine’s Day – Source: securityboulevard.com
Source: securityboulevard.com – Author: claude.mandy This blog originally appeared here: https://drj.com/industry_news/love-in-the-age-of-ai-navigating-online-dating-scams-this-valentines-day/ With Valentine’s Day approaching, love is in the air, and so is the buzz of...
AI is the New Major Accomplice for Cyber Crimes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith Within just a couple years, AI seems to have overtaken a head-spinning amount of aspects in our lives. And there...
Daniel Stori’s ‘Clojure Challenge’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US. Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
US Offers $10M for Info on BlackCat/ALPHV Ransomware Leaders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A week after offering a $10 million reward for information about the leaders of the Hive ransomware group, the U.S....
API security for PCI compliance: A deep dive into the PCI DSS 4.0 impact – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alexandra Charikova There are more than 50 new requirements in PCI DSS v4.0 – do you know which ones apply to you and what...
Microsoft’s February 2024 Patch Tuesday Addresses 2 Zero-Days and 73 Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire Microsoft has released a substantial set of patches in its February 2024 Patch Tuesday. This update is particularly significant as...
The Most Dangerous Entra Role You’ve (Probably) Never Heard Of – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Robbins Entra ID has a built-in role called “Partner Tier2 Support” that enables escalation to Global Admin, but this role is...
Achieving IT Compliance Standards: An Essential Ingredient For Securing Successful Deals – Source: securityboulevard.com
Source: securityboulevard.com – Author: Hyperproof Team As the leader of a sales organization, it’s your job to set your team up for success. Great sales leaders...
Ukrainian Behind Raccoon Stealer Operations Extradited to US – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Mark Sokolovsky Has Fought Extradition From the Netherlands Since March 2022 Arrest Mihir Bagwe (MihirBagwe)...
Navigating the AI Career Maze – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Recruitment & Reskilling Strategy CyberEd.io’s Steve King on Job...
Cyberwar: What Is It Good For? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Leadership & Executive Communication CMO Red Curry, CISO Sam Curry on...
US FTC Proposes Penalties for Deepfake Impersonators – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance FTC Says It Should Be...
Webinar | 5 Ways Cybersecurity Leaders Can Leverage GenAI in 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
FDA Ramps Up Resources for Medical Device Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Healthcare FDA’s Dr. Suzanne Schwartz on How New ‘Super Office’ Boosts Agency’s Cyber...
ISMG Editors: What Happened to the Cyberwar in Israel? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Audit , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Also: Potential HIPAA Audit Revival; Security Risks of Sovereign AI...
Alpha ransomware linked to NetWalker operation dismantled in 2021 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers analyzing the Alpha ransomware payload and modus operandi discovered overlaps with the now-defunct Netwalker ransomware operation. Netwalker was a prolific...
North Korean hackers now launder stolen crypto via YoMix tumbler – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The North Korean hacker collective Lazarus, infamous for having carried out numerous large-scale cryptocurrency heists over the years, has switched...