Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts at Kaspersky have uncovered a new phishing campaign that specifically targets small and medium-sized businesses (SMBs). The attack method...
Author: CISO2CISO Editor 2
Change Healthcare Cyber-Attack Leads to Prescription Delays – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Health tech firm Change Healthcare, part of Optum, has been hit by a cyber-attack, leading to delays in prescriptions being issued...
Russian-Aligned Network Doppelgänger Targets German Elections – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A joint effort by SentinelLabs and ClearSky Cyber Security has uncovered a significant propaganda and disinformation campaign, possibly orchestrated by the...
OWASP Releases Security Checklist for Generative AI Deployment – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Written by Chief information security officers now have a new tool at their disposal to get started with AI securely. The...
Cyber Pros Embrace AI, Over 80% Believe It Will Enhance Jobs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Most cybersecurity professionals believe that AI will have a positive impact on their jobs, helping alleviate pressures caused by the cyber...
Chinese Duo Found Guilty of $3m Apple Fraud Plot – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Two Chinese nationals have been found guilty of running a sophisticated fraud scheme in which they attempted to con Apple out...
Ransomware Warning as CVSS 10.0 ScreenConnect Bug is Exploited – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 IT admins have been urged to patch any on-premises ScreenConnect servers immediately, after reports that a recently published maximum severity vulnerability...
Businesses Increase Cybersecurity as Budgets Surge in 2024 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity is a top concern for businesses in 2024, with over two-thirds of IT decision-makers reporting increased budgets. This positive trend...
6 Best Open Source IAM Tools in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
New Image/Video Prompt Injection Attacks – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog New Image/Video Prompt Injection Attacks Simon Willison has been playing with the video processing capabilities of the new Gemini...
‘Lucifer’ Botnet Turns Up the Heat on Apache Hadoop Servers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Cultura Creative Ltd via Alamy Stock Photo A threat actor is targeting organizations running Apache Hadoop and...
‘VoltSchemer’ Hack Allows Wireless Charger Takeovers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Fusssergei via Adobe Stock Researchers from the University of Florida, alongside CertiK, have come up with a theoretical...
Critical ConnectWise RMM Bug Poised for Exploitation Avalanche – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: RGB Ventures/SuperStock via Alamy Stock Photo Users of the ConnectWise ScreenConnect remote desktop management...
El Al Flight Crew Suffers Midflight Communication Disruption – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Markus Mainka via Alamy Stock Photo “Hostile elements” last week reportedly tried to take over communications on an...
DoT, White House Tackle the Chinese Threat to US Port Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Jack Sullivan via Alamy Stock Photo The Department of Transportation (DoT) issued a warning today about the...
Smashing Security podcast #360: Lockbit locked out, and funeral Facebook scams – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Heaven’s above! Scammers are exploiting online funerals, and Lockbit – the “Walmart of Ransomware” – is dismantled in style by...
Cloud-Native Data Security Posture Management Deployments on AWS with Symmetry Systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: claude.mandy This blog originally appeared here: https://aws.amazon.com/blogs/apn/cloud-native-data-security-posture-management-deployments-on-aws-with-symmetry-systems/ With Amazon Web Services (AWS), you can manage the privacy of your data, control how it’s...
Frontline PCI-ASV Scanning Datasheet – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by Fortra Any business that accepts credit card payments is subject to a set of security guidelines in the Payment...
Why SBOMs are essential for every organization – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens Wednesday, February 21, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
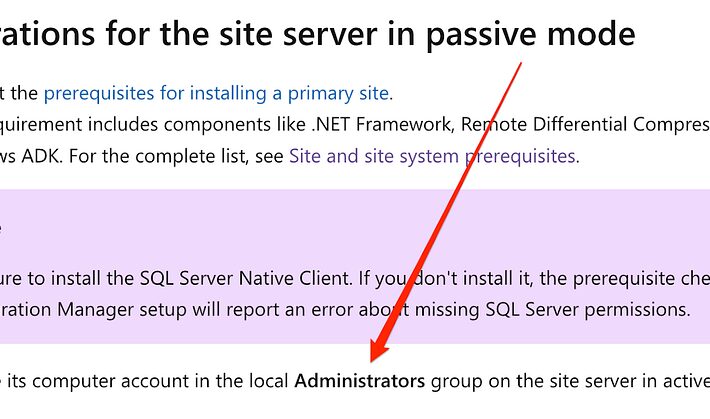
SCCM Hierarchy Takeover with High Availability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Garrett Foster TL;DR: SCCM sites configured to support high availability can be abused to compromise the entire hierarchy I previously wrote about...
How is a Container Scan Done? – Source: securityboulevard.com
Source: securityboulevard.com – Author: AJ Starita Containers offer many benefits, including lightweight portability from one environment to another, but they add a layer of complexity to...
USENIX Security ’23 – William E. Bodell III, Sajad Meisami, Yue Duan – Proxy Hunting: Understanding and Characterizing Proxy-based Upgradeable Smart Contracts in Blockchains – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
How Schools Can Comply with the Three Biggest Online Student Privacy Laws – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith Keeping students’ data safe from prying eyes and malicious actors isn’t as simple as it used to be. Students are...
Threat Hunting Workshop 10: Hunting for Initial Access – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cyborg Security Get ready to elevate your threat hunting skills with Cyborg Security’s exhilarating and interactive workshop, focusing on the pivotal MITRE...
What to Look for in a Secrets Scanner – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tal Zacks Find out the key capabilities of secret scanners and what to consider when searching for a solution. Background In today’s...
CISA Mitigation Guide for Healthcare Organizations: Part Three – Source: securityboulevard.com
Source: securityboulevard.com – Author: Wes Wright Identify and address at-risk assets to protect your healthcare enterprise On November 20, 2023, the Cybersecurity Infrastructure and Security Agency...
Experts Praise White House Port Cybersecurity Initiatives – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management , Operational Technology (OT) Cyber Actions Reflect ‘Positive Step’ in Addressing Overlooked Issues,...
Hack at Services Firm Hits 2.4 Million Eye Doctor Patients – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Cybercrime , Fraud Management & Cybercrime As Vendor Breaches Surge, Medical Practices Need 20/20 Visibility on Third Parties...
Live Webinar | Secrets Detection: Why Coverage Throughout the SDLC is Critical to Your Security Posture – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Joe Nicastro Field CTO, Legit Security Joe Nicastro is a seasoned cybersecurity expert with over a decade of experience in the...
Wyze Security Incident Exposes Private Cameras – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Internet of Things Security 13,000 Users Received Incorrect Thumbnails; 1,504 Tapped on Them, Risking Privacy Prajeet Nair (@prajeetspeaks)...