Source: www.schneier.com – Author: Bruce Schneier With the world’s focus turning to misinformation, manipulation, and outright propaganda ahead of the 2024 U.S. presidential election, we know...
Author: CISO2CISO Editor 2
5 Best VPNs for Social Media in 2024 (Free & Paid VPNs) – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Best for bypassing censorship: NordVPN Best for TikTok’s location-based algorithm: ExpressVPN Best for remote social media teams: Surfshark Best for...
Google Engineer Steals AI Trade Secrets for Chinese Companies – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: kenary820 via Shutterstock The US Justice Department has charged a former Google software engineer with stealing artificial...
Sam Altman Reinstated to OpenAI Board – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Company Concludes His Ouster Stemmed from ‘Breakdown In Trust’ David...
Webinar | Top SaaS Security Threat Trends in 2024 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Salah Nassar Sr. Director Product Marketing, Zscaler Salah is a passionate and customer-centric marketer with a diverse background in networking and...
Banning Ransom Payments: Calls Grow to ‘Figure Out’ Approach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware As Ransomware Disruption Mounts, More Experts Seek Path to Banning Payments Mathew J. Schwartz (euroinfosec)...
A Close Up Look at the Consumer Data Broker Radaris – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs If you live in the United States, the data broker Radaris likely knows a great deal about you, and they are...
The Week in Ransomware – March 8th 2024 – Waiting for the BlackCat rebrand – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams We saw another ransomware operation shut down this week after first getting breached by law enforcement and then targeting critical...
Critical Fortinet flaw may impact 150,000 exposed devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Scans on the public web show that approximately 150,000 Fortinet FortiOS and FortiProxy secure web gateway systems are vulnerable to...
QNAP warns of critical auth bypass flaw in its NAS devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas QNAP warns of vulnerabilities in its NAS software products, including QTS, QuTS hero, QuTScloud, and myQNAPcloud, that could allow attackers...
UnitedHealth brings some Change Healthcare pharmacy services back online – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Optum’s Change Healthcare has started to bring systems back online after suffering a crippling BlackCat ransomware attack last month that...
Microsoft says Russian hackers breached its systems, accessed source code – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft says the Russian ‘Midnight Blizzard’ hacking group recently accessed some of its internal systems and source code repositories using...
$12.5 billion lost to cybercrime, amid tidal wave of crypto investment fraud – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley If you have been optimistically daydreaming that losses attributed to cybercrime might have reduced in the last year, it’s time...
Smashing Security podcast #362: Ransomware fraud, pharmacy chaos, and suicide – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Is there any truth behind the alleged data breach at Fortnite maker Epic Games? Who launched the ransomware attack that...
Ukraine claims it hacked Russian Ministry of Defence, stole secrets and encryption ciphers – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Ukraine claims to have successfully hacked Russian military servers and gained access to highly sensitive information. According to an official...
The Ongoing Struggle to Protect PLCs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nitzan Daube A programmable logic controllerSource: Warut Sintapanon via Alamy Stock Photo COMMENTARY Ten years have passed since the infamous Stuxnet attack...
NSA’s Zero-Trust Guidelines Focus on Segmentation – Source: www.darkreading.com
Source: www.darkreading.com – Author: David Strom Source: mauritius images GmbH via Alamy Stock Photo The US National Security Agency (NSA) delivered its guidelines for zero-trust network...
Nigerian National Pleads Guilty of Conspiracy in BEC Operation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Gregg Vignal via Alamy Stock Photo Henry Onyedikachi Echefu, one of the three Nigerian men who were involved...
How to Ensure Open-Source Packages Are Not Mines – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer Source: Steven Morris via Alamy Stock Photo Open-source repositories are critical to running and writing modern applications, but...
JetBrains TeamCity Mass Exploitation Underway, Rogue Accounts Thrive – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Valeriy Kachaev via Alamy Stock Vector Attacks targeting two security vulnerabilities in the TeamCity CI/CD platform have...
Silence Laboratories Raises $4.1M Funding to Enable Privacy Preserving Collaborative Computing – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SINGAPORE – 29th February 2024 — In the modern age, large companies are wrestling to leverage their customers’ data to...
Enjoy 2 Years of Unrestricted Access to Your Favorite Content for Only $40 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published March 8, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Dropbox Used to Steal Credentials and Bypass MFA in Novel Phishing Campaign – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A novel phishing campaign leveraged legitimate Dropbox infrastructure and successfully bypassed multifactor authentication (MFA) protocols, new research from Darktrace has revealed....
UnitedHealth Sets Timeline to Restore Change Healthcare Systems After BlackCat Hit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 UnitedHealth Group has published a timeline to restore Change Healthcare’s systems following the BlackCat/ALPHV ransomware attack, which has led to delays...
A Taxonomy of Prompt Injection Attacks – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Researchers ran a global prompt hacking competition, and have documented the results in a paper that both gives a lot...
Do You Know Where Your Data Is? How Law Firms Can Protect Their Most Valuable Asset – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By John A. Smith, CSO, Conversant Group If data is the new oil, this holds especially true for law firms...
Building a Secure Data-Protection Infrastructure to Protect against the MOVEit Hack – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Carl Cadregari, Executive Vice President, FoxPointe Solutions Regardless of the industry in which they operate, organizations have likely witnessed...
AI and the Next Wave of Robocalls: Protecting Carriers and Consumers from Sophisticated Voice Fraud – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team By Tim Ward, Chief Strategy Officer, XConnect Robocalls are relentlessly targeting consumers and causing mistrust for the telecom industry as...
What Happened in Cybersecurity in 2023: A Summary of Security Incidents, Vulnerability Information, and Cybersecurity Trends – Source: securityboulevard.com
Source: securityboulevard.com – Author: NSFOCUS The year 2023 witnessed a dynamic and complex cybersecurity landscape, with various security incidents, vulnerabilities, and trends emerging and evolving. Today,...
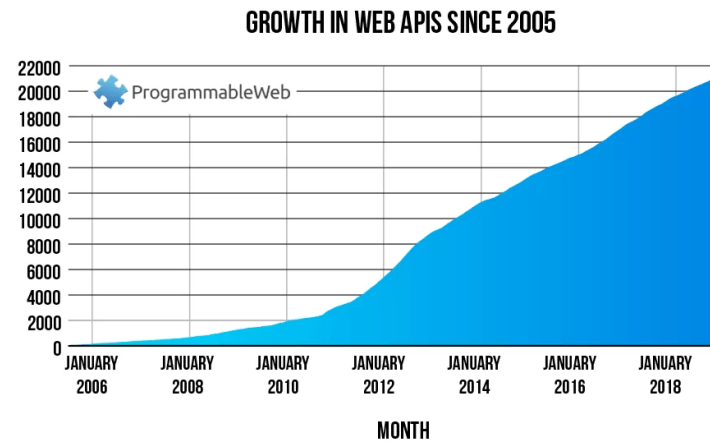
Top 4 Essential Strategies for Securing APIs To Block Compromised Tokens – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jaweed Metz Government bodies are clamping down heavily on institutions and organizations that handle sensitive customer data. For APIs, tokens are used...