Source: www.bleepingcomputer.com – Author: Mayank Parmar Brave has seen a sharp increase in users installing its privacy-focused Brave Browser on iPhones after Apple introduced changes to...
Author: CISO2CISO Editor 2
Windows KB5035849 update failing to install with 0xd000034 errors – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The KB5035849 cumulative update released during today’s Patch Tuesday fails to install on Windows 10 and Windows Server systems with...
Stanford: Data of 27,000 people stolen in September ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Stanford University says the personal information of 27,000 individuals was stolen in a ransomware attack impacting its Department of Public...
Acer confirms Philippines employee data leaked on hacking forum – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Acer Philippines confirmed that employee data was stolen in an attack on a third-party vendor who manages the company’s employee...
Windows 11 KB5035853 update released, here’s what’s new – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Microsoft has released the KB5035853 cumulative update for Windows 11 23H3 and 22H2, with 21 fixes and changes, including fixing...
Windows 10 KB5035845 update released with 9 new changes, fixes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has released the KB5035845 cumulative update for Windows 10 21H2 and Windows 10 22H2, which includes nine new changes...
Microsoft March 2024 Patch Tuesday fixes 60 flaws, 18 RCE bugs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Today is Microsoft’s March 2024 Patch Tuesday, and security updates have been released for 60 vulnerabilities, including eighteen remote code...
Tor’s new WebTunnel bridges mimic HTTPS traffic to evade censorship – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The Tor Project officially introduced WebTunnel, a new bridge type specifically designed to help bypass censorship targeting the Tor network...
Google paid $10 million in bug bounty rewards last year – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google awarded $10 million to 632 researchers from 68 countries in 2023 for finding and responsibly reporting security flaws in...
Over 12 million auth secrets and keys leaked on GitHub in 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas GitHub users accidentally exposed 12.8 million authentication and sensitive secrets in over 3 million public repositories during 2023, with the...
Jailbreaking LLMs with ASCII Art – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Peter A. • March 12, 2024 9:07 AM The whole concept of questions that shall never be asked...
Study Reveals Top Vulnerabilities in Corporate Web Applications – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A recent study conducted by Kaspersky Security Assessment experts has revealed the most prevalent vulnerabilities in corporate web applications developed in-house....
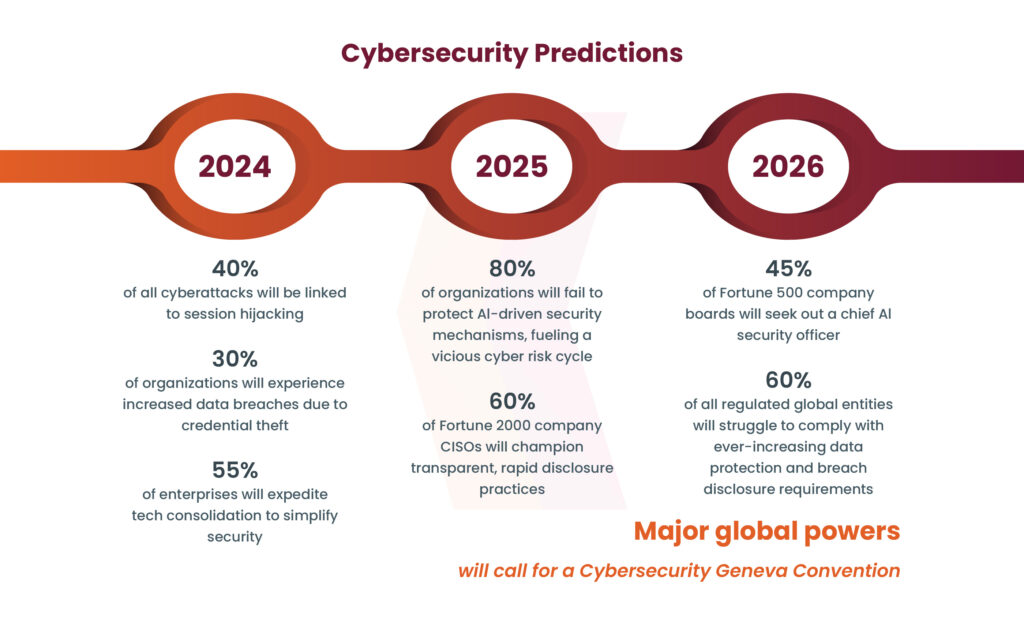
US Intelligence Predicts Upcoming Cyber Threats for 2024 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Accelerating competition between nation-states, regional conflicts with far-reaching impact, and non-state threat actors with unprecedented capabilities are three of the main...
New Cloud Attack Targets Crypto CDN Meson Ahead of Launch – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A malicious campaign has been observed exploiting the blockchain-based Meson service for illicit gains ahead of the crypto token unlock planned...
Three-Quarters of Cyber Incident Victims Are Small Businesses – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Over three-quarters of cyber incidents impacted small businesses in 2023, with ransomware having the biggest impact on these firms, according to...
Lawmakers Slam UK Government’s “Ostrich Strategy” for Cybersecurity – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK will remain “exposed and unprepared” for a potentially catastrophic ransomware attack if it continues to adopt a head-in-the-sand approach...
Victims Lose $47m to Crypto Phishing Scams in February – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Impersonated accounts on X (formerly Twitter) have been blamed for the majority of cryptocurrency phishing attacks last month, with victims losing...
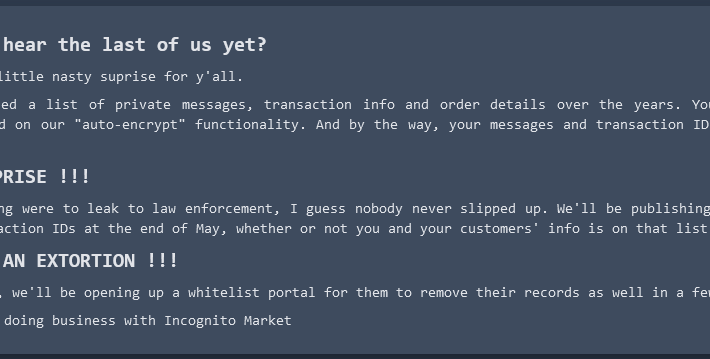
Incognito Darknet Market Mass-Extorts Buyers, Sellers – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Borrowing from the playbook of ransomware purveyors, the darknet narcotics bazaar Incognito Market has begun extorting all of its vendors and...
Sophisticated Vishing Campaigns Take World by Storm – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Mohd Izzuan Roslan via Alamy Stock Photo Voice phishing, or vishing, is having a moment right now,...
The Rise of AI Worms in Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shikha Dhingra The swift advancement of generative AI systems like OpenAI’s ChatGPT and Google’s Gemini has brought about a new era of...
CISA Lacks Staff with Skills Needed to Safeguard OT – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Governance & Risk Management , Information Sharing GAO Report Criticizes CISA’s Info Sharing Programs for Critical Infrastructure Prajeet...
Why Wiz Is Pursuing Its 2nd Massive Funding Round in 2 Years – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Security Operations Cloud Security Vendor Wiz Eyes Unprecedented $800M Funding Round at $10B+ Valuation Michael Novinson (MichaelNovinson) •...
Importance of Resilience in Mitigating Supply Chain Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Business Continuity Management / Disaster Recovery , Cybercrime Nitin Natarajan of CISA on Emerging Lessons From...
Dropbox Used in Latest Exploit for Phishing Attacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Anti-Phishing, DMARC , Fraud Management & Cybercrime , Social Engineering Darktrace Warns of Malware Hidden in PDF Stored in Dropbox Prajeet...
US Federal Budget Proposes $27.5B for Cybersecurity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybersecurity Spending , Government , Industry Specific Budget Proposes Incremental Increases, Not Leaps, But Small Budget Cut for CISA David Perera...
Tuta Mail adds new quantum-resistant encryption to protect email – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Tuta Mail has announced TutaCrypt, a new post-quantum encryption protocol to secure communications from powerful and anticipated decryption attacks. Tuta...
Microsoft says Windows 10 21H2 support is ending in June – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft announced today that it would end support for Windows 10 21H2 in June when the Enterprise and Education editions...
Okta says data leaked on hacking forum not from its systems – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Okta denies that its company data was leaked after a threat actor shared files allegedly stolen during an October 2023...
Researchers expose Microsoft SCCM misconfigs usable in cyberattacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu Security researchers have created a knowledge base repository for attack and defense techniques based on improperly setting up Microsoft’s Configuration...
Equilend warns employees their data was stolen by ransomware gang – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan New York-based securities lending platform EquiLend Holdings confirmed in data breach notification letters sent to employees that their data was...