Source: securityboulevard.com – Author: Jeffrey Burt Google is making moves to help developers ensure that their code is secure. The IT giant this week said it...
Author: CISO2CISO Editor 2
Randall Munroe’s XKCD ‘Relationship Advice’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Credential Stuffing: Who Owns the Risk? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Reece Baldwin Kasada was recently in the news after identifying a credential stuffing campaign targeting Australian retail, fast food, and entertainment outlets....
USENIX Security ’23 – Hengkai Ye, Song Liu, Zhechang Zhang, and Hong Hu – VIPER: Spotting Syscall-Guard Variables for Data-Only Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
Lloyd’s of London Announces Investment in Axio – Source: securityboulevard.com
Source: securityboulevard.com – Author: Axio Wednesday, February 7, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features...
China’s Cyberattackers Maneuver to Disrupt US Critical Infrastructure – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading The US Cybersecurity and Infrastructure Security Agency (CISA) has issued a report detailing how the...
Linux Distros Hit by RCE Vulnerability in Shim Bootloader – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Fauzi Muda via Shutterstock Linux shim, a small piece of code that many major Linux distros use...
Fulton County Court System Still Hobbled by Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Gregg Vignal via Alamy Stock Photo After Fulton County, Georgia, suffered a cyberattack and subsequent power outage at...
New Report From Flare Highlights Pervasive Threat of Initial Access Brokers in NATO Countries – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Montreal, Quebec, Canada – February 6, 2024 – Flare, the leading Continuous Threat Exposure Management (CTEM) solution provider, has released a new report...
Patch Now: Critical TeamCity Bug Allows for Server Takeovers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Andre Boukreev via Shutterstock JetBrains has patched a critical security vulnerability in its TeamCity On-Premises server that...
Q&A: Tel Aviv Railway Project Bakes In Cyber Defenses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Source: Oleg Zaslavsky via Alamy Stock Photo Railway networks are suffering an increase in cyberattacks, most...
UAE Banks Conduct Cyber War Games Exercise – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Aleksandar Tomic via Alamy Stock Photo Banks in the United Arab Emirates (UAE) recently participated in a simulated...
How to Prepare for Elevated Cybersecurity Risk at the Super Bowl – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kris Philipsen Allegiant StadiumSource: Kirby Lee via Alamy Stock Photo COMMENTARY Major sporting events such as the Super Bowl are fertile ground...
As Smart Cities Expand, So Do the Threats – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: jamesteohart via Shutterstock For technologists, building smart cities is not an aspirational goal but a matter of...
Cisco Adds New Security and AI Capabilities in Next Step Toward Cisco Networking Cloud Vision – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE AMSTERDAM, Feb. 6, 2024 /PRNewswire/ — CISCO LIVE EMEA — Cisco (NASDAQ: CSCO), the leader in networking and security, today introduced new capabilities and technologies...
4 Threat Hunting Techniques to Prevent Bad Actors in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Nicole Rennolds Today’s cybersecurity threats are highly sophisticated; bad actors are using technology like no-code malware and AI-generated phishing campaigns to breach...
Securden Password Vault Review 2024: Security, Pricing, Pros & Cons – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Securden fast facts Our rating: 3.7 stars out of 5 Pricing: Ask for a quote. Key features Strong activity tracking....
How to Use Enpass: A Step-by-Step Guide for Beginners – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Enpass is an offline password manager that can integrate with third-party cloud services like Google Drive and Dropbox. In this...
To BEC or Not to BEC: How to Approach New Email Authentication Requirements – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 OnDemand | The Tools & Technology You Need to Meet Google/Yahoo Email Authentication Requirements Proofpoint • February 7, 2024 ...
Powering ANZ Grids: Navigating Cyber Threats in the Energy Sector – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Mark Cooper President and Founder, PKI Solutions Mark B. Cooper, president and founder of PKI Solutions, has been known as “The...
Holes Appear in Internet-Connected Toothbrush Botnet Warning – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Don’t Brush in Fear, as Supposed DDoS Dental Trauma Fails to Pass Muster Mathew J. Schwartz (euroinfosec) • February 7, 2024...
How to Win a Cyberwar: Use a Combined Intelligence Strategy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 In times of war, such as the Israel-Hamas war that began on Oct. 7, 2023, intelligence becomes even more important than...
Bolstering Healthcare Cybersecurity: The Regulatory Outlook – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 The Biden administration’s strategy for bolstering health sector cybersecurity, which includes newly released voluntary cyber performance goals and plans to update...
Live Webinar | Utilizing SIEM and MDR for Maximum Protection – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Bill Bernard VP, Security Strategy, Deepwatch Bill Bernard currently serves as Deepwatch’s VP, Security Strategy. He is a seasoned security expert...
Meta Is Being Urged to Crack Down on UK Payment Scams – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Fraud Risk Management , Social Media Banking Fraud Heads Say Facebook Marketplace Is Teeming With Scammers...
Webinar | How Do I Use AI to Enhance My Security? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Ryan Roobian Global Principal Solutions Architect, Google Cloud Security Ryan Roobian has over 20 years of experience in various specialties in...
Chinese Hackers Preparing ‘Destructive Attacks,’ CISA Warns – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Officials Say Hackers Are Evading Detection on Critical...
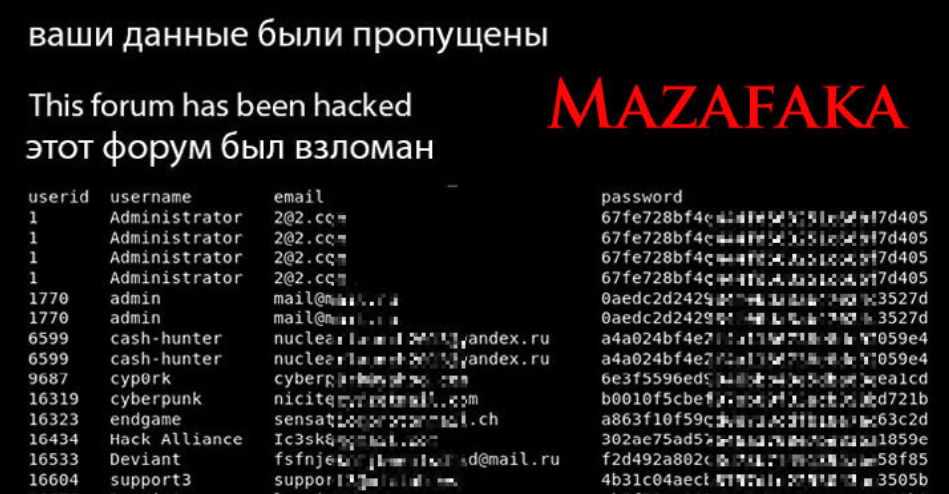
From Cybercrime Saul Goodman to the Russian GRU – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs In 2021, the exclusive Russian cybercrime forum Mazafaka was hacked. The leaked user database shows one of the forum’s founders was...
AnyDesk System Breach Raises Concerns Among MSP Users – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși AnyDesk confirmed recently that a cyberattack has affected their product systems. The hackers accessed the source code and private code...
Spear Phishing vs Phishing: What Are The Main Differences? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb Threat actors love phishing because it works. It is particularly effective in cloud infrastructure—once they’re inside, they gain access to...