Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Tofino via Alamy Stock Photo Three high-risk vulnerabilities have been uncovered in Microsoft Azure’s big-data analytics service...
Author: CISO2CISO Editor 2
Google: Govs Drive Sharp Growth of Commercial Spyware Cos – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: metamorworks via Shutterstock Governments around the world, seeking to spy on rights activists, dissidents and others of...
Fresh ‘Mispadu Stealer’ Variant Emerges – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: The Lightwriter via Alamy Stock Photo Researchers stumbled upon a new variant of the stealthy banking Trojan known...
Deepfake-Generating Apps Explode, Allowing Multimillion-Dollar Corporate Heists – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Mike via Adobe Stock Deepfake creation software is proliferating on the Dark Web, enabling scammers to carry...
Pegasus Spyware Targets Jordanian Civil Society in Wide-Ranging Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: COREdesign via Shutterstock Journalists, lawyers, and human-rights activists in the Middle Eastern nation of Jordan face increased...
Google Open Sources AI-Boosted Fuzzing Framework – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: dubassy via Alamy Google has released its fuzzing framework as an open source resource to help developers and...
Nigerian President Dismisses Nation’s ‘Cybercrime Haven’ Image – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nicholas Fearn, Contributing Writer 2 Min Read Source: 3D generator via Alamy Stock Photo The president of Nigeria recently delivered a blistering...
Name That Edge Toon: The Great Escape – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist 1 Min Read Here’s a trick that even Harry Houdini might have struggled to master. Come up with a...
A Guide to Effective Cloud Privileged Access Management – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Over the last decade, the cloud has gone from being a radical, disruptive new technology to becoming the default setting...
Main Types of Patch Management Solutions: A Decision-Making Guide – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Choosing between the different types of patch management solutions impacts the effort your IT team must make to keep the...
Privileged Accounts 101: Everything You Need to Know – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Privileged accounts are one of the most common entry points for hackers. The profusion of accounts in an organization and...
Weekly Update 385 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt I told ya so. Right from the beginning, it was pretty obvious what “MOAB” was probably going to be and...
Enpass Review 2024: Pricing, Features, Pros, & Cons – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Enpass fast facts Our rating: 4.0 stars out of 5 Pricing: Starts at $1.99 Key features Offline password manager. Can...
Deepfake Fraud – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments B.J. Herbison • February 5, 2024 11:36 AM Was the call recorded? On the call we have a...
AnyDesk Compromised, Passwords Revoked – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading 1 Min Read Source: Seemanta Dutta via AlamyStock Photo AnyDesk, which provides a remote desktop application providing...
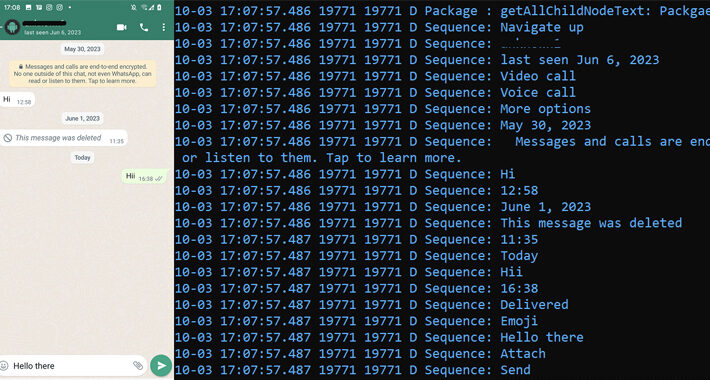
Patchwork Using Romance Scam Lures to Infect Android Devices with VajraSpy Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 05, 2024NewsroomCyber Espionage / Cyber Extortion The threat actor known as Patchwork likely used romance scam lures to trap victims...
How Spoutible’s Leaky API Spurted out a Deluge of Personal Data – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Ever hear one of those stories where as it unravels, you lean in ever closer and mutter “No way! No...
USENIX Security ’23 – MorFuzz: Fuzzing Processor Via Runtime Instruction Morphing enhanced Synchronizable Co-simulation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Jinyan Xu, Yiyuan Liu, Sirui He, Haoran Lin, Yajin Zhou, Cong Wang Many thanks to USENIX for publishing their...
US government imposed sanctions on six Iranian intel officials – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US government imposed sanctions on six Iranian intel officials Pierluigi Paganini February 04, 2024 The US government issued sanctions against...
AnyDesk Confirms Cyber Incident, Pushes Out Password Reset – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Cybercrime , Fraud Management & Cybercrime Company Says Problem Remediated, All Security-Related Certificates Revoked Prajeet Nair (@prajeetspeaks) •...
Microsoft is bringing the Linux sudo command to Windows Server – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft is bringing the Linux ‘sudo’ feature to Windows Server 2025, offering a new way for admins to elevate privileges...
Leaky Vessels flaws allow hackers to escape Docker, runc containers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Four vulnerabilities collectively called “Leaky Vessels” allow hackers to escape containers and access data on the underlying host operating system....
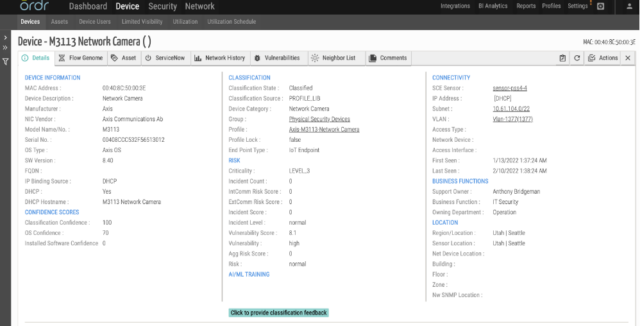
Ordr Security Bulletin – Volt Typhoon State-Sponsored Cyber Actor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pandian Gnanaprakasam Authors: Pandian G, Gowri Sunder Ravi, Srinivas Loke Summary of Advisory from FBI/CISA Actors with malicious intentions, particularly the People’s...
Dispute data, consumer insights, and emerging trends from 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team The first several months of the year are known as ‘chargeback season’ for fraud practitioners globally, as...
Clorox estimates the costs of the August cyberattack will exceed $49 Million – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Clorox estimates the costs of the August cyberattack will exceed $49 Million Pierluigi Paganini February 03, 2024 Cleaning products giant...
Mastodon fixed a flaw that can allow the takeover of any account – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Mastodon fixed a flaw that can allow the takeover of any account Pierluigi Paganini February 03, 2024 A vulnerability impacting...
Iranian hackers breached Albania’s Institute of Statistics (INSTAT) – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Iranian hackers breached Albania’s Institute of Statistics (INSTAT) Pierluigi Paganini February 02, 2024 Albania’s Institute of Statistics (INSTAT) announced that...
Clorox says cyberattack caused $49 million in expenses – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Clorox has confirmed that a September 2023 cyberattack has so far cost the company $49 million in expenses related to...
Check if you’re in Google Chrome’s third-party cookie phaseout test – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google has started testing the phasing out of third-party cookies on Chrome, affecting about 1% of its users or approximately...
Mastodon vulnerability allows attackers to take over accounts – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Mastodon, the free and open-source decentralized social networking platform, has fixed a critical vulnerability that allows attackers to impersonate and...