Source: www.techrepublic.com – Author: Nicole Rennolds Today’s cybersecurity threats are highly sophisticated; bad actors are using technology like no-code malware and AI-generated phishing campaigns to breach...
Author: CISO2CISO Editor 2
Securden Password Vault Review 2024: Security, Pricing, Pros & Cons – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Securden fast facts Our rating: 3.7 stars out of 5 Pricing: Ask for a quote. Key features Strong activity tracking....
How to Use Enpass: A Step-by-Step Guide for Beginners – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Enpass is an offline password manager that can integrate with third-party cloud services like Google Drive and Dropbox. In this...
To BEC or Not to BEC: How to Approach New Email Authentication Requirements – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 OnDemand | The Tools & Technology You Need to Meet Google/Yahoo Email Authentication Requirements Proofpoint • February 7, 2024 ...
Powering ANZ Grids: Navigating Cyber Threats in the Energy Sector – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Mark Cooper President and Founder, PKI Solutions Mark B. Cooper, president and founder of PKI Solutions, has been known as “The...
Holes Appear in Internet-Connected Toothbrush Botnet Warning – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Don’t Brush in Fear, as Supposed DDoS Dental Trauma Fails to Pass Muster Mathew J. Schwartz (euroinfosec) • February 7, 2024...
How to Win a Cyberwar: Use a Combined Intelligence Strategy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 In times of war, such as the Israel-Hamas war that began on Oct. 7, 2023, intelligence becomes even more important than...
Bolstering Healthcare Cybersecurity: The Regulatory Outlook – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 The Biden administration’s strategy for bolstering health sector cybersecurity, which includes newly released voluntary cyber performance goals and plans to update...
Live Webinar | Utilizing SIEM and MDR for Maximum Protection – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Bill Bernard VP, Security Strategy, Deepwatch Bill Bernard currently serves as Deepwatch’s VP, Security Strategy. He is a seasoned security expert...
Meta Is Being Urged to Crack Down on UK Payment Scams – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Fraud Risk Management , Social Media Banking Fraud Heads Say Facebook Marketplace Is Teeming With Scammers...
Webinar | How Do I Use AI to Enhance My Security? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Ryan Roobian Global Principal Solutions Architect, Google Cloud Security Ryan Roobian has over 20 years of experience in various specialties in...
Chinese Hackers Preparing ‘Destructive Attacks,’ CISA Warns – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Critical Infrastructure Security , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Officials Say Hackers Are Evading Detection on Critical...
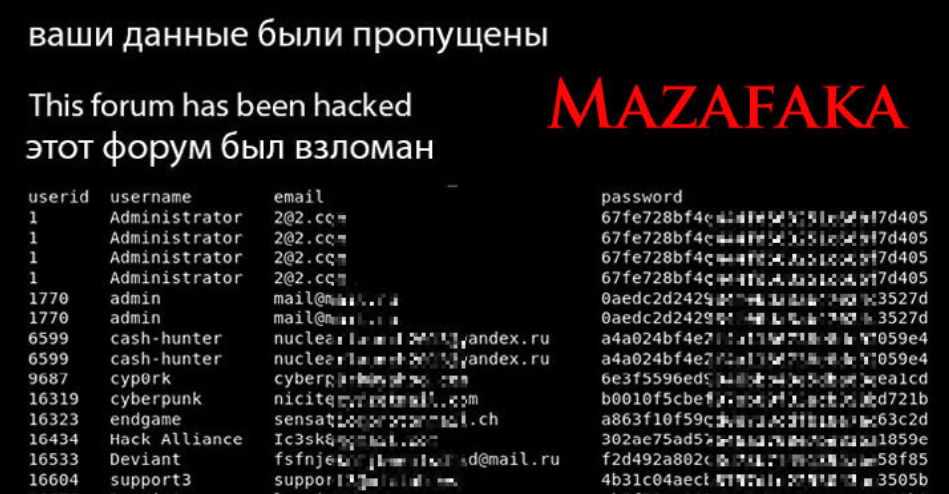
From Cybercrime Saul Goodman to the Russian GRU – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs In 2021, the exclusive Russian cybercrime forum Mazafaka was hacked. The leaked user database shows one of the forum’s founders was...
AnyDesk System Breach Raises Concerns Among MSP Users – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși AnyDesk confirmed recently that a cyberattack has affected their product systems. The hackers accessed the source code and private code...
Spear Phishing vs Phishing: What Are The Main Differences? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb Threat actors love phishing because it works. It is particularly effective in cloud infrastructure—once they’re inside, they gain access to...
Chinese hackers infect Dutch military network with malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan A Chinese cyber-espionage group breached the Dutch Ministry of Defence last year and deployed malware on compromised devices, according to the...
Mastering SBOMs: Best practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Keiana King In our recent webinar, Mastering SBOMs: Best Practices, speakers, including Ilkka Turunen, Field CTO, Sonatype, Roger Smith, Global Testing and...
Chinese Hackers Penetrated Unclassified Dutch Network – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Beijing Used FortiGate Vulnerability to Install Trojan Akshaya Asokan (asokan_akshaya) • February...
Documents about the NSA’s Banning of Furby Toys in the 1990s – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • February 6, 2024 3:23 PM @ Bruce, ALL, I never did pull a genuine one...
Beware: Fake Facebook Job Ads Spreading ‘Ov3r_Stealer’ to Steal Crypto and Credentials – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 06, 2024NewsroomSocial Engineering / Malvertising Threat actors are leveraging bogus Facebook job advertisements as a lure to trick prospective targets...
How Neurodiversity Can Help Fill the Cybersecurity Workforce Shortage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dr. Jodi Asbell-Clarke Source: designer491 via Alamy Stock Photo COMMENTARY One of the most vexing issues in cybersecurity doesn’t have to do...
Automate Routine Operational Workflows With Generative AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security Source: Dariusz Banaszuk via Alamy Stock Photo When you think about your day-to-day responsibilities across security, compliance, identity, and management,...
Microsoft Azure HDInsight Bugs Expose Big Data to Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Tofino via Alamy Stock Photo Three high-risk vulnerabilities have been uncovered in Microsoft Azure’s big-data analytics service...
Google: Govs Drive Sharp Growth of Commercial Spyware Cos – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: metamorworks via Shutterstock Governments around the world, seeking to spy on rights activists, dissidents and others of...
Fresh ‘Mispadu Stealer’ Variant Emerges – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: The Lightwriter via Alamy Stock Photo Researchers stumbled upon a new variant of the stealthy banking Trojan known...
Deepfake-Generating Apps Explode, Allowing Multimillion-Dollar Corporate Heists – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Mike via Adobe Stock Deepfake creation software is proliferating on the Dark Web, enabling scammers to carry...
Pegasus Spyware Targets Jordanian Civil Society in Wide-Ranging Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: COREdesign via Shutterstock Journalists, lawyers, and human-rights activists in the Middle Eastern nation of Jordan face increased...
Google Open Sources AI-Boosted Fuzzing Framework – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: dubassy via Alamy Google has released its fuzzing framework as an open source resource to help developers and...
Nigerian President Dismisses Nation’s ‘Cybercrime Haven’ Image – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nicholas Fearn, Contributing Writer 2 Min Read Source: 3D generator via Alamy Stock Photo The president of Nigeria recently delivered a blistering...
Name That Edge Toon: The Great Escape – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist 1 Min Read Here’s a trick that even Harry Houdini might have struggled to master. Come up with a...