Source: www.csoonline.com – Author: News 17 Oct 20244 mins Financial Services IndustryFraud Network announces anomaly detection will go live, while separate system will allow banks to...
Author: CISO2CISO Editor 2
CSO30 Australia 2024 winners unveiled at gala ceremony – Source: www.csoonline.com
Source: www.csoonline.com – Author: Australia’s top cybersecurity leaders and their teams have been recognised at this year’s CSO30 Awards. Held in conjunction with the CIO50, the...
Analysis of the Crypt Ghouls group: continuing the investigation into a series of attacks on Russia – Source: securelist.com
Source: securelist.com – Author: Kaspersky Last December, we discovered a new group targeting Russian businesses and government agencies with ransomware. Further investigation into this group’s activity...
Number of Active Ransomware Groups Highest on Record, Cyberint’s Report Finds – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson This year has seen the highest number of active ransomware groups on record, with 58 attacking global businesses in the...
NIS 2 Compliance Deadline Arrives: What You Need to Know – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson On Oct. 17, the Network and Information Security 2 Directive takes effect. This means that relevant entities in industries such...
How MSSPs and MDRs Can Maximize Threat Detection Efficiency with Uncoder AI – Source: socprime.com
Source: socprime.com – Author: Alla Yurchenko In the face of increasingly sophisticated cyber threats, security service providers such as MSSPs and MDRs strive to enhance threat...
Strategies for Building an Effective, Resilient Security Operations Center – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The modern Security Operations Center (SOC) has morphed and matured since its infancy in the early 1990s. The primary responsibility...
The Evolution of Automated Browser Detection: A Cat & Mouse Game – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eloi Bahuet Throughout the history of bot protection, automated browser detection has always been a top priority. This article traces the history...
CVE-2024-9381 – Ivanti CSA Security Vulnerability – October 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Security Insights Team A critical vulnerability (CVE-2024-9381) in Ivanti’s Cloud Services Appliance allows attackers to bypass security measures and execute arbitrary code. ...
Life in the Swimlane with Abby Shapiro, Customer Success Manager – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore Welcome to the “Life in the Swimlane” blog series. Here we will feature interviews with Swimlaners to learn more about...
Mastering Product-led Onboarding in B2B SaaS: A Comprehensive Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author In the high-stakes world of B2B SaaS, where traditional growth tactics are losing their edge...
ADR Provides Application Visibility for CISOs | Closing Application Layer Gap | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Lindner, Director, Application Security Good cyber defense involves more than blocking and tackling. Without visibility into what’s happening, where and by...
World Economic Forum: AI, Quantum Require ‘Paradigm Shift’ in Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt How emerging technologies like AI, quantum computing, and the Internet of Things (IoT) are developed and deployed is has to...
USENIX NSDI ’24 – EPVerifier: Accelerating Update Storms Verification with Edge-Predicate – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Chenyang Zhao, Yuebin Guo, Jingyu Wang, Qi Qi, Zirui Zhuang, Haifeng Sun, Lingqi Guo, Yuming Xie, Jianxin Liao Our sincere...
Executive Perspectives, Episode 2, Michelle Faylo – Source: securityboulevard.com
Source: securityboulevard.com – Author: Axio Axio CEO, Scott Kannry recently sat down with Michelle Faylo, US Cyber & Technology Leader of Lockton in our executive perspectives...
The CMMC Final Rule is Published: What Contractors Need to Know – Source: securityboulevard.com
Source: securityboulevard.com – Author: Orlee Berlove, reviewed by Noël Vestal, PMP, CMMC RP The Department of Defense (DoD) published the Cybersecurity Maturity Model Certification (CMMC) Final Rule on October...
Ex-Oracle, Google Engineers Raise $7m From Accel for Public Launch of Simplismart to Empower AI Adoption – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE October 17, 2024: OpenAI is projected to generate over $10 billion in revenue next year, a clear sign that the adoption...
Illinois Joins CoSN’s Trusted Learning Environment (TLE) State Partnership Program for Student Data Privacy – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE WASHINGTON, DC (October 15, 2024) – The Consortium for School Networking (CoSN) today announced that the Illinois Learning Technology Center (LTC),...
Swift to Launch AI-Powered Fraud Defence to Enhance Cross-Border Payments – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE Brussels, 16 October 2024 – Swift today announced that it is rolling out new AI-enhanced fraud detection to help the...
Hong Kong Crime Ring Swindles Victims Out of $46M – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Mike via Adobe Stock Hong Kong police arrested 27 people Monday for their involvement in a deepfake scam...
Internet Archive Slowly Revives After DDoS Barrage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Source: Postmodern Studio via Alamy Stock Photo The Internet Archive, a nonprofit digital library website, is...
4 Ways to Address Zero-Days in AI/ML Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan McInerney Dan McInerney, Lead AI Threat Researcher, Protect AI October 17, 2024 3 Min Read Source: Blackboard via Alamy Stock Photo...
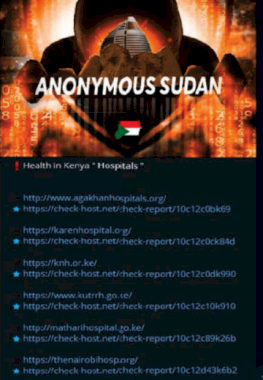
Anonymous Sudan Unmasked as Leaders Face Life in Prison – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Firoze Edassery via Alamy Stock Photo A federal grand jury has indicted two Sudanese nationals for their...
Is a CPO Still a CPO? The Evolving Role of Privacy Leadership – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arlo Gilbert Source: imageBROKER.com GmbH & Co. KG via Alamy Stock Photo COMMENTARY The role of the CPO — chief privacy officer...
Sudanese Brothers Arrested in ‘AnonSudan’ Takedown – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. government on Wednesday announced the arrest and charging of two Sudanese brothers accused of running Anonymous Sudan (a.k.a. AnonSudan),...
A glimmer of good news on the ransomware front, as encryption rates plummet – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley No-one would be bold enough to say that the ransomware problem is receding, but a newly-published report by Microsoft does...
Smashing Security podcast #389: WordPress vs WP Engine, and the Internet Archive is down – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content WordPress’s emperor, Matt Mullenweg, demands a hefty tribute from WP Engine, and a battle erupts, leaving millions...
Hackers breach Pokémon game developer, source code and personal information leaks online – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley In what appears to be one of the biggest leaks in Pokémon history, troves of information related to multiple incarnations...
Be Aware of These Eight Underrated Phishing Techniques – Source: www.securityweek.com
Source: www.securityweek.com – Author: Stu Sjouwerman Email phishing is by far one of the most prevalent forms of phishing. However, there are a number of lesser-known...
CISA, FBI Seek Public Comment on Software Security Bad Practices Guidance – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US cybersecurity agency CISA and the FBI have released new guidance on security bad practices for software manufacturers and...