Source: securityboulevard.com – Author: David Michael Berry Over the past 6 months I have been researching ransomware, and not even from the technical angle (which would...
Author: CISO2CISO Editor 2
USENIX NSDI ’24 – Reasoning About Network Traffic Load Property at Production Scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Ruihan Li, Fangdan Ye, Yifei Yuan, Ruizhen Yang, Bingchuan Tian, Tianchen Guo, Hao Wu, Xiaobo Zhu, Zhongyu Guan, Qing Ma,...
DEF CON 32 – AppSec Considerations From The Casino Industry – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Cybersecurity » Application Security » DEF CON 32 – AppSec Considerations From The Casino Industry Authors/Presenters:Aleise McGowan, Tennisha...
DPRK Uses Microsoft Zero-Day in No-Click Toast Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Eric Anthony Johnson via Alamy Stock Photo The North Korea-backed advanced persistent threat known...
USENIX NSDI ’24 – Crescent: Emulating Heterogeneous Production Network at Scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Zhaoyu Gao, Anubhavnidhi Abhashkumar, Zhen Sun, Weirong Jiang, Yi Wang Our sincere thanks to USENIX, and the Presenters & Authors...
USENIX NSDI ’24 – A High-Performance Design, Implementation, Deployment, and Evaluation of The Slim Fly Network – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Nils Blach, Maciej Besta, Daniele De Sensi, Jens Domke, Hussein Harake, Shigang Li, Patrick Iff, Marek Konieczny, Kartik Lakhotia, Ales...
Managing Foreign Government Information (FGI) on a Network – Source: securityboulevard.com
Source: securityboulevard.com – Author: Max Aulakh If you’re a firm that works with foreign governments, in addition to certifications like ISO 27001 that you will generally...
Seceon at GITEX Global 2024: Driving Cybersecurity Innovation with Tech First Gulf – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kriti Tripathi In today’s ever-evolving cybersecurity landscape, organizations are grappling with a delicate balance: safeguarding their digital environments while managing costs and...
The Unsolvable Problem: XZ and Modern Infrastructure – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The ongoing prevalence (and rise) of software supply chain attacks is enough to keep any software developer or security analyst...
Industrial and Critical Infrastructure Defenders to Gather in Atlanta for 2024 ICS Cybersecurity Conference – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s 2024 ICS Cybersecurity Conference kicks off on Tuesday, October 22nd ath the InterContinental Buckhead Atlanta! With 80+ sessions over three days,...
Cyera Acquires Data Loss Prevention Firm Trail Security for $162 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Data security company Cyera announced on Thursday that it has acquired data loss prevention (DLP) startup Trail Security for $162...
BlackBerry Cuts Cylance Spend to Focus on Profitable Areas – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Endpoint Protection Platforms (EPP) , Endpoint Security , Managed Detection & Response (MDR) Company Shifts Cyber Focus to QNX and Secure Communications...
North Korean IT Scam Workers Shift to Extortion Tactics – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Governance & Risk Management Report Reveals North Korean Workers Expanding into Intellectual...
Hacker Poses as Israeli Security Vendor to Deliver Wiper – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering Phishing Emails Impersonating Eset Target Cybersecurity Professionals With Malware Chris...
BianLian Ransomware Gang Claims Heist of Pediatric Data – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Fraud Management & Cybercrime , Healthcare , Industry Specific Boston Children’s Health Physicians Says Incident Involved Unnamed IT Vendor Marianne Kolbasuk McGee...
MacOS Safari ‘HM Surf’ Exploit Exposes Camera, Mic, Browser Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Delphotos via Alamy Stock Photo A security weakness in the Safari browser on macOS devices might have...
Can You Fax a Check? Yes. Follow These Steps to Do it Safely – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Corry Cummings There are probably a dozen ways of sending money that are easier than faxing a check. Even so, it is...
Microsoft: Ransomware Attacks Growing More Dangerous, Complex – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse The number of attempted ransomware attacks on Microsoft customers globally have grown dramatically in the last year, according to Microsoft’s...
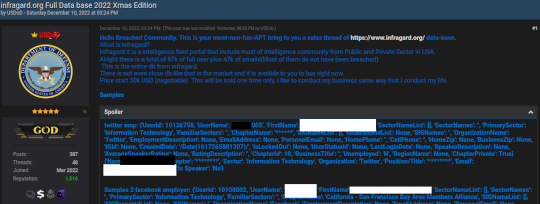
Brazil Arrests ‘USDoD,’ Hacker in FBI Infragard Breach – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Brazilian authorities reportedly have arrested a 33-year-old man on suspicion of being “USDoD,” a prolific cybercriminal who rose to infamy in...
Get an Untrusted Security Advisor! Have Fun, Reduce Fail! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anton Chuvakin Many organizations are looking for trusted advisors, and this applies to our beloved domain of cyber/information security. If you look...
Is End-User Cybersecurity Training Useless? Spoiler Alert: It’s Not! – Source: securityboulevard.com
Source: securityboulevard.com – Author: hmeyers Chris Clements, VP of Solutions Architecture October 18, 2024 Because of the frequency of phishing attacks landing in user mailboxes and...
USENIX NSDI ’24 – MESSI: Behavioral Testing of BGP Implementations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Rathin Singha, Rajdeep Mondal, Ryan Beckett, Siva Kesava Reddy Kakarla, Todd Millstein, George Varghese Our sincere thanks to USENIX, and...
AI-Generated Personas: Trust and Deception – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Michael Berry And the Ethical Dilemma of Using AI to Create Fake Online Personalities In recent years, advancements in artificial intelligence...
Daniel Stori’s Turnoff.US: ‘bash-gptl’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US! Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
USENIX NSDI ’24 – Netcastle: Network Infrastructure Testing At Scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Rob Sherwood, Jinghao Shi, Ying Zhang, Neil Spring, Srikanth Sundaresan, Jasmeet Bagga, Prathyusha Peddi, Vineela Kukkadapu, Rashmi Shrivastava, Manikantan KR,...
The transformation of open source: Lessons from the past decade – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens Over the past decade, the world of open source software has undergone a seismic transformation, both in terms of its...
Celebrating Excellence in Financial Services – Source: securityboulevard.com
Source: securityboulevard.com – Author: Thomas Stoesser Like most businesses, banks are facing a highly competitive future built on digital services. To succeed, they must modernize their...
Army Cloud Program to Help SMBs Meet DoD Cyber Requirements – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The U.S. Army is building a secure cloud environment that small businesses can use to meet increasingly stringent military cybersecurity...
Cybersecurity Snapshot: Tenable Report Warns About Toxic Cloud Exposures, as PwC Study Urges C-Suite Collaboration for Stronger Cyber Resilience – Source: securityboulevard.com
Source: securityboulevard.com – Author: Juan Perez Check out invaluable cloud security insights and recommendations from the “Tenable Cloud Risk Report 2024.” Plus, a PwC study says...
AI-Powered Fraud Detection Systems for Enhanced Cybersecurity – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Artificial intelligence (AI) has many applications in cybersecurity. Automated fraud detection is one of the most impactful of these use...