Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s 2024 ICS Cybersecurity Conference kicks off today at the InterContinental Hotel Buckhead Atlanta. With 80+ sessions over three days, the conference...
Author: CISO2CISO Editor 2
Google Warns of Samsung Zero-Day Exploited in the Wild – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A zero-day vulnerability in Samsung’s mobile processors has been leveraged as part of an exploit chain for arbitrary code execution,...
Critical Vulnerabilities Expose mbNET.mini, Helmholz Industrial Routers to Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Germany’s CERT@VDE has alerted organizations to several critical and high-severity vulnerabilities discovered recently in industrial routers. Impacted vendors have released...
BlackCat Ransomware Successor Cicada3301 Emerges – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Alphv/BlackCat ransomware gang might have pulled an exit scam in early March, but the threat appears to have resurfaced...
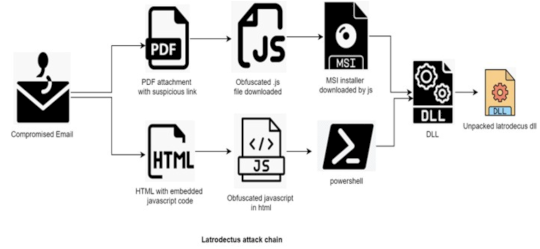
Latrodectus Malware Increasingly Used by Cybercriminals – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Latrodectus malware has been increasingly used by cybercriminals, with recent campaigns targeting the financial, automotive and healthcare sectors, according...
Securing the Supply Chain by Working With Ethical Hackers – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. Software supply chain attacks increasingly create concern among cybersecurity experts as these exploits are becoming more common. But solving the problem...
Socket Accelerates Open-Source Security With $40M Series B – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Application Security , Application Security & Online Fraud , Fraud Management & Cybercrime Socket Plans to Triple Headcount After Big Growth, Deliver...
Researchers Debut AI Tool That Helps Detect Zero-Days – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Artificial Intelligence & Machine Learning , Governance & Risk Management , Next-Generation Technologies & Secure Development Vulnerability Tool Detected Flaws in OpenAI...
CISA Ramping Up Election Security Warnings as Voting Begins – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Election Security , Fraud Management & Cybercrime , Government US Cyber Defense Agency Says Election Is Secure Despite Intensifying Threats Chris Riotta...
Dental Center Chain Settles Data Breach Lawsuit for $2.7M – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Legislation & Litigation , Standards, Regulations & Compliance 2023 Hacking Incident Affected 1.9 Million Patients, Employees Marianne Kolbasuk McGee (HealthInfoSec) • October...
What Today’s SOC Teams Can Learn From Baseball – Source: www.darkreading.com
Source: www.darkreading.com – Author: Mike Mitchell Mike Mitchell, VP, Threat Hunt Intelligence, Intel 471 October 22, 2024 5 Min Read Source: Augustas Cetkauskas via Alamy Stock...
Name That Toon: The Big Jump – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist Need a push? A day for a cybersecurity professional can be full of adrenaline-pumping moments. Come up with a...
Russia-Linked Hackers Attack Japan’s Govt, Ports – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: StudioProX via Shutterstock Two Russian hacking groups leveled distributed denial-of-service (DDoS) attacks at Japanese logistics and shipbuilding...
Unmanaged Cloud Credentials Pose Risk to Half of Orgs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Artur Marciniec via Alamy Stock Photo Almost half of organizations have users with “long-lived” credentials in cloud services,...
Cisco Disables DevHub Access After Security Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: Sergiy Palamarchuk via Shutterstock Cisco has disabled public access to one of its DevHub environments after threat...
Internet Archive Gets Pummeled in Round 2 Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Postmodern Studio via Alamy Stock Photo Just a few days after the Internet Archive told the public it...
AI and the SEC Whistleblower Program – Source: www.schneier.com
Source: www.schneier.com – Author: B. Schneier Tax farming is the practice of licensing tax collection to private contractors. Used heavily in ancient Rome, it’s largely fallen...
Microsoft geht jetzt unter die Phish-Fänger – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 21 Oktober 20244 Minuten CyberkriminalitätPhishing Der Tech-Riese erstellt gefälschte Azure-Tenants, um Phisher in Honeypots zu locken und ihr Verhalten zu analysieren....
Internet Archive breached twice within days – Source: www.csoonline.com
Source: www.csoonline.com – Author: The second breach used stolen tokens from the first attack that remained un-rotated even days later. Internet Archive continues to be in...
Cisco bestätigt Datenklau – Source: www.csoonline.com
Source: www.csoonline.com – Author: Hacker haben Daten von Cisco gestohlen. JRdes – Shutterstock.com In der vergangenen Woche sorgte ein Darknet-Post mit angeblich gestohlenen Cisco-Daten für Aufregung....
Detect Brute Force and Credential Access Activity Linked to Iranian Hackers: The FBI, CISA, and Partners Warn Defenders of Growing Attacks Against Critical Infrastructure Organizations – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk WRITTEN BY Daryna Olyniychuk Team Lead of Marketing [post-views] October 21, 2024 · 5 min read At the end of...
Inside the Dark Web: How Threat Actors Are Selling Access to Corporate Networks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alberto Casares In recent weeks, underground forums on the dark web have continued to flourish as bustling marketplaces where cybercriminals sell unauthorized...
Are Leaders Ready to Break the Ransomware Cycle – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist It is good to see US government leaders realize that ransomware is a growing existential threat to our country, at...
USENIX NSDI ’24 – DISTMM: Accelerating Distributed Multimodal Model Training – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Jun Huang, Zhen Zhang, Shuai Zheng, Feng Qin, Yida Wang Our sincere thanks to USENIX, and the Presenters & Authors...
Types of Security Audits: Overview and Best Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Cybersecurity audits are key to maintaining compliance with regulations and upholding a strong security posture. They evaluate your organization’s systems,...
FedRAMP Certification and Compliance: What It Is and Why It Matters – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Cloud technologies increase access to information, streamline communication between government agencies and citizens, and accelerate information sharing. And that’s why...
Survey Surfaces Depth and Scope of Identity Management Challenge – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A survey of 510 IT security and risk practitioners finds 93% have access to a comprehensive inventory of human and...
DEF CON 32 – AppSec Village – Web2 Meets Web3 Hacking Decentralized Applications – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, October 22, 2024 Home » Cybersecurity » Application Security » DEF CON 32 – AppSec Village – Web2 Meets...
USENIX NSDI ’24 – Accelerating Neural Recommendation Training with Embedding Scheduling – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters:Chaoliang Zeng, Xudong Liao, Xiaodian Cheng, Han Tian, Xinchen Wan, Hao Wang, Kai Chen Our sincere thanks to USENIX, and...
Hurricane scammers: How to stay safe during national emergencies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ryan Healey-Ogden During national weather emergencies, many turn to online platforms to get the latest news but don’t know about the threat...