Source: www.govinfosecurity.com – Author: Presented by Snowflake 60 Minutes Snowflake provides the data foundation and building blocks for enterprise AI and Applications....
Author: CISO2CISO Editor 2
Why Shoring Up Cyber at Rural and Small Hospitals Is Urgent – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: When a large hospital in an urban area is shut down by ransomware, the IT disruption can be significant, but when a...
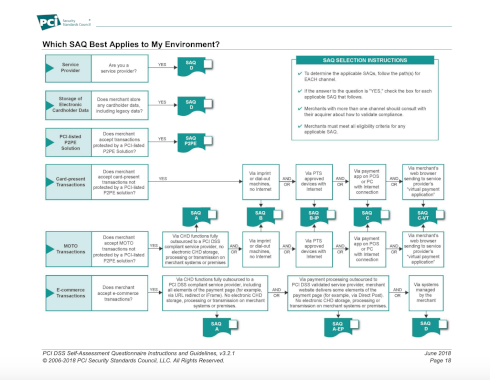
PCI DSS Self-Assessment Questionnaires: Choosing the Right Type – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security If you process credit card payments, you need to prioritize security. One way to guarantee this safety is by complying...
PCI DSS Compliance Levels and Requirements: A Complete Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security If your business processes credit card transactions, it needs to meet the Payment Card Industry (PCI) Data Security Standards (DSS)....
An Introduction to Operational Relay Box (ORB) Networks – Unpatched, Forgotten, and Obscured – Source: securityboulevard.com
Source: securityboulevard.com – Author: S2 Research Team Although not a new concept, Operational Relay Box (ORB) networks—often referred to as “covert,” “mesh,” or “obfuscated” networks—are becoming...
What Is Secrets Management? Best Practices and Challenges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Legit Security Modern apps require hundreds of secrets to function (API keys, cloud credentials, etc.). However, poor management of these secrets can...
Aembit Introduces Google Workload Identity Federation Support – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ashur Kanoon Aembit today announced support for Google Workload Identity Federation (WIF). While Google WIF issues short-lived security tokens for accessing GCP...
Test Data Management Best Practices: Handling Sensitive Data Across Multiple Databases – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Horn Handling large volumes of sensitive data in testing environments is challenging. You need to protect customer information, financial records, and...
DEF CON 32 – AppSec Village – Got 99 Problems But Prompt Injection Ain’t Watermelon – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, October 29, 2024 Home » Cybersecurity » Application Security » DEF CON 32 – AppSec Village – Got 99...
Daniel Stori’s Turnoff.US: ‘Security Engineer Interview’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US! Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
Lessons from the Cisco Data Breach—The Importance of Comprehensive API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eric Schwake In the wake of Cisco’s recent data breach involving exposed API tokens – amongst other sensitive information – the cybersecurity...
Recurring Windows Flaw Could Expose User Credentials – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Source: tdhster via Shutterstock All versions of Windows clients, from Windows 7 through current Windows 11 versions, contain...
China’s ‘Evasive Panda’ APT Debuts High-End Cloud Hijacking – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Source: Design Pics Inc. via Alamy Stock Photo The China-sponsored Evasive Panda hacking crew has...
French ISP Confirms Cyberattack, Data Breach Affecting 19M – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Timon Schneider via Alamy Stock Photo Free, a French telecommunications company and the second largest Internet service provider...
FBI, Partners Disrupt RedLine, Meta Stealer Operations – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: JVPhoto via Alamy Stock Photo The FBI in collaboration with various international law-enforcement agencies has seized the...
How to Find the Right CISO – Source: www.darkreading.com
Source: www.darkreading.com – Author: Martha Heller Source: Borka Kiss via Alamy Stock Photo COMMENTARY The artificial intelligence (AI) investment cycle we are currently in will drive...
UAC-0001 aka APT28 Attack Detection: Leveraging PowerShell Command in Clipboard as Initial Entry Point – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko The notorious Russian state-sponsored hacking group known as APT28 or UAC-0001, which has a history of launching targeted phishing attacks on Ukrainian...
Your First 90 Days as Security Lead, Part 2: Developing a Plan and Getting to Work – Source:www.hackerone.com
Source: www.hackerone.com – Author: johnk. You’ve just been named as your organization’s new head of security. So what do you do first? Read part one of...
Risk reduction redefined: How compromise assessment helps strengthen cyberdefenses – Source: securelist.com
Source: securelist.com – Author: Victor Sergeev, Amged Wageh, Ahmed Khlief Introduction Organizations often rely on a layered defense strategy, yet breaches still occur, slipping past multiple...
The AI Fix #22: Probing AI tongues and ASCII smuggling attacks – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content News and views from the world of artificial intelligence. In episode 22 of “The AI Fix”, our...
French ISP Free confirms data breach after hacker puts customer data up for auction – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley One of the largest internet providers in France, Free S.A.S, has confirmed that it recently suffered a cybersecurity breach after...
New LightSpy Spyware Targets iOS with Enhanced Capabilities – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A newer version of the LightSpy spyware, known for targeting iOS devices, has been expanded to include capabilities for compromising device security...
Chenlun’s Evolving Phishing Tactics Target Trusted Brands – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: An ongoing, sophisticated phishing campaign has been observed targeting individuals with text messages impersonating trusted brands like Amazon. DomainTools researchers linked this...
Law Enforcement Operation Takes Down Redline and Meta Infostealers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A global law enforcement operation has disrupted infrastructure for the Redline and Meta infostealers, malware tools widely used by cybercriminal groups to...
NIS2 Compliance Puts Strain on Business Budgets – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Meeting compliance requirements with the EU’s Network and Information Security (NIS)2 Directive has forced many organizations to divert funds from other areas...
Suspicious Social Media Accounts Deployed Ahead of COP29 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A network of 71 suspicious accounts on X has been deployed ahead of the UN’s COP29 climate change conference. The accounts aim...
Five Eyes Agencies Launch Startup Security Initiative – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The UK, US, Canada, New Zealand and Australian governments have launched a new program designed to help their tech startups improve baseline...
ICO: 55% of UK Adults Have Had Data Lost or Stolen – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The UK’s privacy watchdog has issued a stern warning to the nation’s organizations to improve their data protection posture, after revealing that...
How Hackers Can Help Reduce Your Organization’s Application Risk on AWS – Source:www.hackerone.com
Source: www.hackerone.com – Author: HackerOne. HackerOne recently hosted AWS and a panel of expert ethical hackers to discuss how Server-Side Request Forgery (SSRF) vulnerabilities and cloud misconfiguration are ripe environments...
Guest Essay: Wallarm report shows API exposures rose steeply across all industries in Q3 2024 – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Ivan Novikov Application Programming Interfaces (APIs) have become the backbone of modern enterprises, facilitating seamless communication between both internal systems...