Source: www.securityweek.com – Author: Kevin Townsend Tel Aviv, Israel based Noma Security has emerged from stealth mode with $32 million in Series A funding led by...
Author: CISO2CISO Editor 2
DEF CON 32 – On Your Ocean’s 11 Team, I’m The AI Guy (Technically Girl) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » DEF CON 32 – On Your Ocean’s 11 Team, I’m The AI Guy (Technically...
How Can FSOs Help with CMMC Compliance? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Max Aulakh As of now, the final rule for the Cybersecurity Maturity Model Certification has been published. The clock is ticking for...
Highlights of New York’s Cybersecurity Regulation 23 NYCRR Part 500 – Source:www.hackerone.com
Source: www.hackerone.com – Author: luke. September 4, 2018 – Eighteen month transitional period ends. Covered Entities are required to be in compliance with the requirements of...
The AWS Shared Responsibility Model: 3 Areas of Improvement to Make Today Part 3: Logging, Monitoring, and Alerting in AWS – Source:www.hackerone.com
Source: www.hackerone.com – Author: Justin Boyer. In the last two parts of this series, we discussed the AWS Shared Responsibility Model. We started with keeping your...
Normalyze to be purchased by Proofpoint – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Data Security, Mergers and Acquisitions October 30, 2024 San Francisco-based data security posture management firm Normalyze is set to be acquired by...
Proofpoint Expands Data Security With Normalyze Acquisition – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Data Loss Prevention (DLP) , Endpoint Security Normalyze’s AI-Powered DSPM Technology Boosts Proofpoint’s Data Visibility, Control Michael Novinson (MichaelNovinson) • October 29,...
Friday Squid Blogging: Squid Sculpture in Massachusetts Building – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Discovering programs is easier than ever with the new and improved Program Directory – Source:www.hackerone.com
Source: www.hackerone.com – Author: Martijn Russchen. Today, we’re excited to announce an overhaul of the HackerOne Program Directory! Since its launch, Hackers have been using the...
NCSC Details ‘Pygmy Goat’ Backdoor Planted on Hacked Sophos Firewall Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine The UK’s National Cyber Security Centre (NCSC) has published technical documentation of a sophisticated network backdoor being planted on hacked...
GreyNoise Credits AI for Spotting Exploit Attempts on IoT Livestream Cams – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Cybersecurity firm GreyNoise Intelligence is crediting an AI-powered tool for capturing attempts to exploit critical vulnerabilities in live streaming IoT...
In Other News: FBI’s Ransomware Disruptions, Recall Delayed Again, CrowdStrike Responds to Bloomberg Article – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy stories that might have slipped under the radar. We provide...
US, Israel Describe Iranian Hackers’ Targeting of Olympics, Surveillance Cameras – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The United States and Israel this week published a cybersecurity advisory describing the latest activities of an Iranian threat group,...
Ex-Disney Worker Accused of Hacking Computer Menus to Add Profanities, Errors – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A former worker hacked servers at Walt Disney World after being fired in order to manipulate computer menus by changing...
Get details right to safely implement DANE in Exchange Online, warn experts – Source: www.csoonline.com
Source: www.csoonline.com – Author: Experts welcome Microsoft’s announcement that Exchange Online can now handle Inbound SMTP DANE with DNSSEC to improve email security, but admins may...
Download the AI in the Enterprise (for Real) Spotlight – Source: us.resources.csoonline.com
Source: us.resources.csoonline.com – Author: Register Download the November 2024 issue of the Enterprise Spotlight from the editors of CIO, Computerworld, CSO, InfoWorld, and Network World. See...
Introducing Hacker Dashboard: Your personalized HackerOne overview – Source:www.hackerone.com
Source: www.hackerone.com – Author: Martijn Russchen. Earlier this month, we introduced the all-new Program Directory with a fresh set of metrics and better filtering. Now, we’re...
Fired Disney worker accused of hacking into restaurant menus, replacing them with Windings and false peanut allergy information – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A disgruntled former Disney employee is facing charges that he hacked into the company’s restaurant menu systems and wreaked havoc...
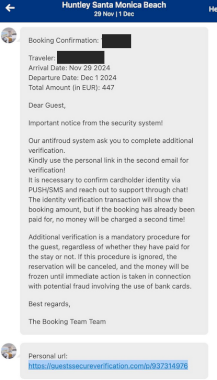
Booking.com Phishers May Leave You With Reservations – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This story...
IoT Security Failures Can Be Sh*tty – Source: securityboulevard.com
Source: securityboulevard.com – Author: John Gallagher It’s hard not to see IoT security failures in the news because they can be dramatic, and this week was...
DEF CON 32 – Welcome to DEF CON 32 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » DEF CON 32 – Welcome to DEF CON 32 by Marc...
GreyNoise: AI’s Central Role in Detecting Security Flaws in IoT Devices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Threat researchers at cybersecurity firm GreyNoise Intelligence discovered two security vulnerabilities in live-streaming cameras used in such sectors as industrial...
October Recap: New AWS Sensitive Permissions and Services – Source: securityboulevard.com
Source: securityboulevard.com – Author: Karen Levy As AWS continues to evolve, new services and permissions are frequently introduced to enhance functionality and security. This blog provides...
Cybersecurity Vulnerability News: October 2024 CVE Roundup – Source: securityboulevard.com
Source: securityboulevard.com – Author: Security Insights Team Keep Your Organization Safe with Up-to-Date CVE Information Cybersecurity vulnerability warnings from the National Institute of Standards and Technology...
Stop Supply Chain Invaders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland The post Stop Supply Chain Invaders appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise. *** This...
Getting the Gist of CJIS – 5.9.5 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland What’s New in CJIS 5.9.5 as it Relates to Firmware Security? n the latest CJIS Security Policy, the FBI is...
Why Supply Chain Security Demands Focus on Hardware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Supply chain security for servers, PCs, laptops, and devices has correctly focused on protecting these systems from vulnerabilities introduced through...
ATT&CK v16: Worry-Free Updates in Tidal Cyber – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tidal Cyber We are thrilled to share that we have migrated Tidal Cyber’s Community & Enterprise platforms to v16 of MITRE ATT&CK®...
Microsoft’s Controversial Recall Feature Release Delayed Again – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt It’s going to be at least another month or more before Microsoft’s much-debated Recall feature for new Copilot+ PCs is...
Chinese Hackers Use Quad7 Botnet for Credential Theft – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Security Operations Hackers Using Password Spraying to Steal User Microsoft Account Credentials Akshaya Asokan (asokan_akshaya) • November 1, 2024 Image:...