Source: www.hackerone.com – Author: johnk. New York City during the holidays. Magical. Bringing together hackers from around the world to legally hack the U.S. Air Force....
Author: CISO2CISO Editor 2
Patch Tuesday Update – November 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by Fortra CVE/Advisory Title Tag Microsoft Severity Rating Base Score Microsoft Impact Exploited Publicly Disclosed CVE-2024-43530 Windows Update Stack Elevation...
6 Ways to Save Money on CMMC Costs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Orlee Berlove, reviewed by Jamie Leupold The DoD’s CMMC Final Rule becomes effective on December 16, 2024, and requires organizations who handle...
DEF CON 32 – The Hack, The Crash And Two Smoking Barrels – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, November 12, 2024 Home » Security Bloggers Network » DEF CON 32 – The Hack, The Crash And Two...
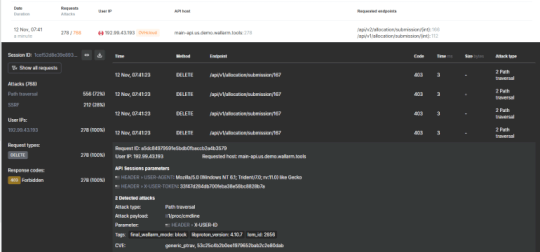
Context is King: Using API Sessions for Security Context – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tim Erlin There’s no doubt that API security is a hot topic these days. The continued growth in API-related breaches and increase...
Randall Munroe’s XKCD ‘Proterozoic Rocks’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored by Marc Handelman. Read the original post...
Scaling Global Protection: DataDome Expands to Over 30 Points of Presence (PoP) Worldwide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andrew Hendry At DataDome, our mission is clear: deliver unmatched bot protection with the highest performance standards for our customers. To this...
Is the latest book on “Pentesting APIs” any good? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dana Epp The folks over at Packt Publishing sent me a gift recently. It was a copy of one of their latest...
Infostealer Malware: An Introduction – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flare Infostealer malware represents one of the most underrated threats to corporate and consumer information security today. These sophisticated remote access Trojans...
DEF CON 32 – Optical Espionage: Using Lasers to Hear Keystrokes Through Glass Windows – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Tuesday, November 12, 2024 Home » Security Bloggers Network » DEF CON 32 – Optical Espionage: Using Lasers to Hear...
Fake IP checker utilities on npm are crypto stealers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ax Sharma Recently identified npm packages called “node-request-ip“, “request-ip-check” and “request-ip-validator“ impersonate handy open source utilities relied upon by developers to retrieve...
Top 5 Google Authenticator Alternatives in 2024 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Andrew Wan We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
The AI Fix #24: Where are the alien AIs, and are we being softened up for superintelligence? – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 24 of The AI Fix, Mark makes an unforgivable error about the Terminator franchise, our...
Winter Fuel Payment scam targets UK citizens via SMS – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley Scammers have leapt at the opportunity to exploit vulnerable UK residents by sending bogus messages telling them they need to...
Pentagon Secrets Leaker Jack Teixeira Sentenced to 15 Years in Prison by a Federal Judge – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A federal judge on Tuesday sentenced a Massachusetts Air National Guard member to 15 years in prison after he pleaded...
Microsoft Confirms Zero-Day Exploitation of Task Scheduler Flaw – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Microsoft’s security response team on Tuesday pushed out fixes for at least 90 vulnerabilities across the Windows ecosystem and called...
Patch Tuesday: Critical Flaws in Adobe Commerce, Photoshop, InDesign, Illustrator – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Enterprise software maker Adobe on Tuesday rolled out fixes for a wide swathe of critical security flaws across product lines,...
GitLoker Strikes Again: New “Goissue” Tool Targets GitHub Developers and Corporate Supply Chains – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend An actor claiming membership in the Gitloker hacking group is offering a new GitHub phishing tool for sale or rent. ...
Ahold Delhaize Cybersecurity Incident Impacts Giant Food, Hannaford – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Several US pharmacies and supermarket chains owned by Dutch food giant Ahold Delhaize have been affected by a cybersecurity incident...
SAP Patches High-Severity Vulnerability in Web Dispatcher – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Enterprise software maker SAP on Tuesday announced the release of eight new and two updated security notes as part of...
Form I-9 Compliance Data Breach Impacts Over 190,000 People – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Employee eligibility verification solutions provider Form I-9 Compliance has suffered a data breach and its impact is far bigger than...
Millions of Hot Topic Customers Impacted by Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Roughly 57 million unique email addresses allegedly stolen from fashion retailer Hot Topic have been posted online, data breach notification...
Criminals Exploiting FBI Emergency Data Requests – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier I’ve been writing about the problem with lawful-access backdoors in encryption for decades now: that as soon as you create...
Malicious Python Package Exfiltrates AWS Credentials – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Security Operations Developers’ Credentials Stolen via Typosquatted ‘Fabric’ Library Prajeet Nair (@prajeetspeaks) • November 11, 2024 Image: Shutterstock A malicious...
How Global Threat Actors May Respond to a Second Trump Term – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cybercrime , Fraud Management & Cybercrime , Government Experts Warn of Intensifying Global Cyber Threats During a Second Trump Presidency Chris Riotta...
Snyk Acquires Probely to Strengthen API Security for AI Apps – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Application Security , Application Security & Online Fraud , Fraud Management & Cybercrime Snyk Boosts API Security with Enhanced Dynamic App Security...
CHERI Alliance Adds to Memory Safety Hardware Coalition – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Endpoint Security , Hardware / Chip-level Security UK Government Agencies, Google Join Group that Promotes Akshaya Asokan (asokan_akshaya) • November 12, 2024...
The Power of the Purse: How to Ensure Security by Design – Source: www.darkreading.com
Source: www.darkreading.com – Author: Gary Barlet Gary Barlet, Public Sector Chief Technology Officer, Illumio November 12, 2024 5 Min Read Source: Zoonar GmbH via Alamy Stock...
Incident Response, Anomaly Detection Rank High on Planned ICS Security Spending – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jennifer Lawinski, Contributing Writer Source: SANS State of ICS/OT Cybersecurity 2024, Figure 18 In the “SANS 2024 State of ICS/OT Cybersecurity” report,...
Halliburton Remains Optimistic Amid $35M Data Breach Losses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Todd Strand via Alamy Stock Photo Halliburton Company, a multinational corporation known for its oil and gas products...