Source: www.darkreading.com – Author: Jennifer Lawinski, Contributing Writer Source: Zoonar GmbH via Alamy Stock Photo Continuous security assessment platform newcomer Frenos narrowly edged out the competition...
Author: CISO2CISO Editor 2
Varonis Warns of Bug Discovered in PostgreSQL PL/Perl – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: tofino via Alamy Stock Photo Researchers at Varonis discovered a vulnerability within Postgres language extension PL/Perl, allowing a...
Idaho Man Turns to RaaS to Extort Orthodontist – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Gregg Vignal via Alamy Stock Photo Robert Purbeck, 45, received a 10-year prison sentence for hacking into 19...
Trump Picks Kennedy Jr. to Head HHS – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Governance & Risk Management , Government , HIPAA/HITECH Vaccine Skeptic’s Views on Health Privacy Not Well-Known Marianne Kolbasuk McGee (HealthInfoSec) • November...
Iranian Threat Actors Mimic North Korean Job Scam Techniques – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering Tehran Baits Aerospace Sector Into Downloading Malware With Fake Job...
Silverfort Buys Rezonate to Fortify Identity Security Muscle – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Cloud Security , Identity & Access Management , Security Operations Comprehensive Identity Security Platform Expands Protection to Cloud, On-Premises Michael Novinson (MichaelNovinson)...
Hackers Lurking in Critical Infrastructure to Wage Attacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Critical Infrastructure Security , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Australian Government Warns of Nation-State Actors’ Plans to Weaponize...
Live Webinar | From Risk to Resilience: Elevating Cyber Awareness and Human Risk Management – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: Presented by Fortra’s Terranova Security In today’s digital landscape, human behavior is often the weakest link in cybersecurity defenses. This webinar explores...
watchTowr Finds New Zero-Day Vulnerability in Fortinet Products – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Attack surface management provider watchTowr claims to have found a new zero-day vulnerability in cybersecurity provider Fortinet’s products. This flaw would allow...
Fortifying the Future: AI Security Is The Cornerstone Of The AI And GenAI Ecosystem – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The rapid proliferation of AI technologies is bringing about significant advancements, but it has also introduced a wide range of...
ShrinkLocker ransomware: what you need to know – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley What is ShrinkLocker? ShrinkLocker is a family of ransomware that encrypts an organisation’s data and demands a ransom payment in...
IT specialist Jack Teixeira jailed for 15 years after leaking classified military documents on Discord – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Jack Teixeira, the 22-year-old former Air National Guardsman who leaked hundreds of classified documents online, has been sentenced to 15...
GenAI-Security als Checkliste – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die OWASP-Checkliste für AI Cybersecurity und -Governance verspricht schnelle Unterstützung für Unternehmen, um generative KI sicher einzusetzen. Das Open Web Application Security...
Overcome fragmented cloud security operations with unified XDR and SIEM – Source: www.csoonline.com
Source: www.csoonline.com – Author: From fragmentation to focus: Optimizing hybrid cloud security with a unified security operations center. As any security practitioner can attest, it takes...
Hacker brüsten sich mit gestohlenen Destatis-Daten – Source: www.csoonline.com
Source: www.csoonline.com – Author: News 14 November 20243 Minuten Artificial Intelligence Im Darknet sind gestohlene Daten von zahlreichen deutschen Firmen aufgetaucht. Diese stammen vermutlich vom Statistischen...
Implementing zero trust in AI and LLM architectures: A practitioner’s guide to secure and responsible AI systems – Source: www.csoonline.com
Source: www.csoonline.com – Author: Implementing zero trust in AI and LLM architectures: A practitioner’s guide to secure and responsible AI systems Opinion 14 Nov 20248 mins...
US says China conducted massive espionage through breached telcos – Source: www.csoonline.com
Source: www.csoonline.com – Author: FBI and CISA have warned that some US telecommunication companies have been breached by China-backed Salt Typhoon to snoop on US secrets...
Palo Alto Networks Issues AI Red Alert – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jon Swartz SANTA CLARA, Calif. — With great promise comes potential peril. And while artificial intelligence (AI) is looked upon as a...
DEF CON 32 – Redefining V2G: How To Use Your Vehicle As Game Controller – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, November 14, 2024 Home » Security Bloggers Network » DEF CON 32 – Redefining V2G: How To Use Your...
Blinded by Silence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Raven Tait Blinded by Silence: How Attackers Disable EDR Overview Endpoint Detection and Response systems (EDRs) are an essential part of modern cybersecurity...
Randall Munroe’s XKCD ‘Geometriphylogenetics’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Busting Ransomware’s Billion-Dollar Boom with Network Observability and Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mal Fitzgerald Busting Ransomware’s Billion-Dollar Boom with Network Observability and Security by Mal Fitzgerald Ransomware-as-a-service (RaaS) is the first example of a...
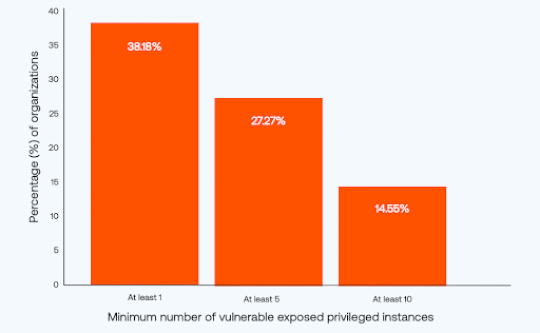
Who’s Afraid of a Toxic Cloud Trilogy? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shai Morag The Tenable Cloud Risk Report 2024 reveals that nearly four in 10 organizations have workloads that are publicly exposed, contain...
Black Friday bots are coming—is your e-commerce site prepared? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kira Lempereur Commerce of all kinds surges around the end-of-year holidays—but e-commerce has been steadily growing year over year. Retail sites are...
NIST Clears Backlog of Known Security Flaws but Not All Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The federal agency that for much of the year has struggled to keep up-to-date a detailed database of vulnerabilities has...
New iOS Security Feature Makes It Harder for Police to Unlock Seized Phones – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Clive Robinson • November 14, 2024 11:01 AM @ Bruce, ALL, With regards, “This is a really good security feature....
1.1 Million UK NHS Employee Records Exposed From Microsoft Power Pages Misconfiguration – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Over a million NHS employee records — including email addresses, phone numbers, and home addresses — were exposed online due...
TunnelBear VPN Review 2024: Pricing, Ease of Use & Security – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares TunnelBear VPN fast facts Our rating: 3.1 stars out of 5 Pricing: Starts at $3.33/mo (annual) Key features: Fun, beginner-friendly...
Iranian Hackers Target Aerospace Industry in ‘Dream Job’ Campaign – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Iranian hackers have been observed targeting the aerospace industry with fake job offers with the goal of infecting victims with...
Bitsight to Acquire Cybersixgill for $115 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cyber risk management firm Bitsight today announced a $115 million deal to acquire threat intelligence data provider Cybersixgill. Boston, Massachusetts-based...