Source: securityboulevard.com – Author: Chris Garland
Microsoft Threat Intelligence has issued new reporting about tactics being used by Silk Typhoon (also called APT27 or HAFNIUM by some researchers). Silk Typhoon is a Chinese espionage group, observed targeting Microsoft Exchange Servers in 2021, now reported to be targeting common IT solutions for initial access. Microsoft reports that Silk Typhoon exploits unpatched applications, abuses stolen API keys and credentials, and targets remote access solutions. In particular, Ivanti appliances were targeted with exploits for the recently disclosed vulnerability CVE-2025-0282, a remotely exploitable stack-based buffer overflow in Ivanti Connect Secure, Policy Secure, and ZTA Gateways.
Targeting IT infrastructure providers such as Ivanti, Citrix, Palo Alto, and Microsoft itself has the potential to grant cyberattackers access to a broad swath of targets, making supply chain attacks an appealing approach. When global enterprises, governments, and critical infrastructure providers all rely on the same set of network infrastructure providers, attackers are highly incentivized to target those providers. This behavior is not restricted to state sponsored APTs targeting telecommunications, either. Recent chat log leaks from the prolific Black Basta ransomware group contained extensive discussion of CVEs and potential zero days against the same IT supply chain targets being pursued by the Typhoons.
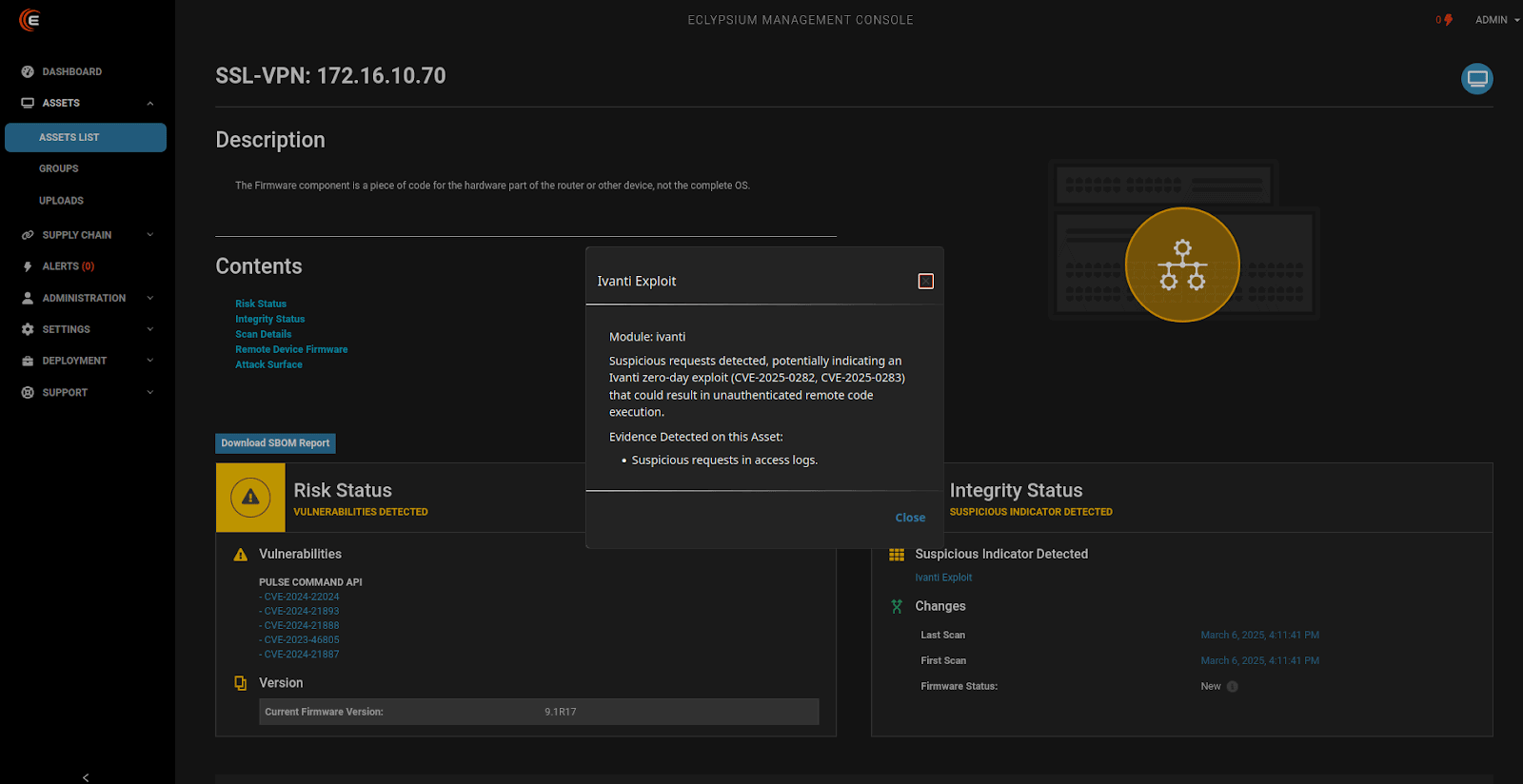
Eclypsium’s supply chain security platform can help detect initial exploitation of Ivanti devices by Silk Typhoon, providing detection of unauthorized changes or malicious implants and visibility into device configurations and vulnerabilities.

Keeping Up With The Typhoons

These latest Silk Typhoon revelations are just the most recent in a torrent of headlines about advanced persistent threat (APT) groups, likely sponsored by the People’s Republic of China, targeting global telecommunications companies, IoT devices, firmware and software supply chains, and critical infrastructure.
The various APT groups carrying the Typhoon moniker all have their own hallmark tactics that have been gradually discovered and revealed by security researchers. Volt Typhoon is known for living-off-the-land (LOTL) techniques, and using command-line tools like PowerShell and Windows Management Instrumentation to stay under the radar and extend the length of time they can maintain access to a target network. Flax Typhoon is known for targeting compromised IoT devices for Command & Control activity.
But while their tactics may differ, the strategic similarities between the Typhoons (and other Chinese APTs such as Velvet Ant) show distinct, worrisome trends:
- Targeting U.S. and global communications infrastructure such as telecommunications companies and internet service providers.
- Exploiting known vulnerabilities and zero days in widely deployed, common IT infrastructure and network devices from major vendors like Cisco, Juniper, F5, and Citrix.
- Exploiting trusted IT vendor relationships and under-secured areas of network infrastructure for espionage.
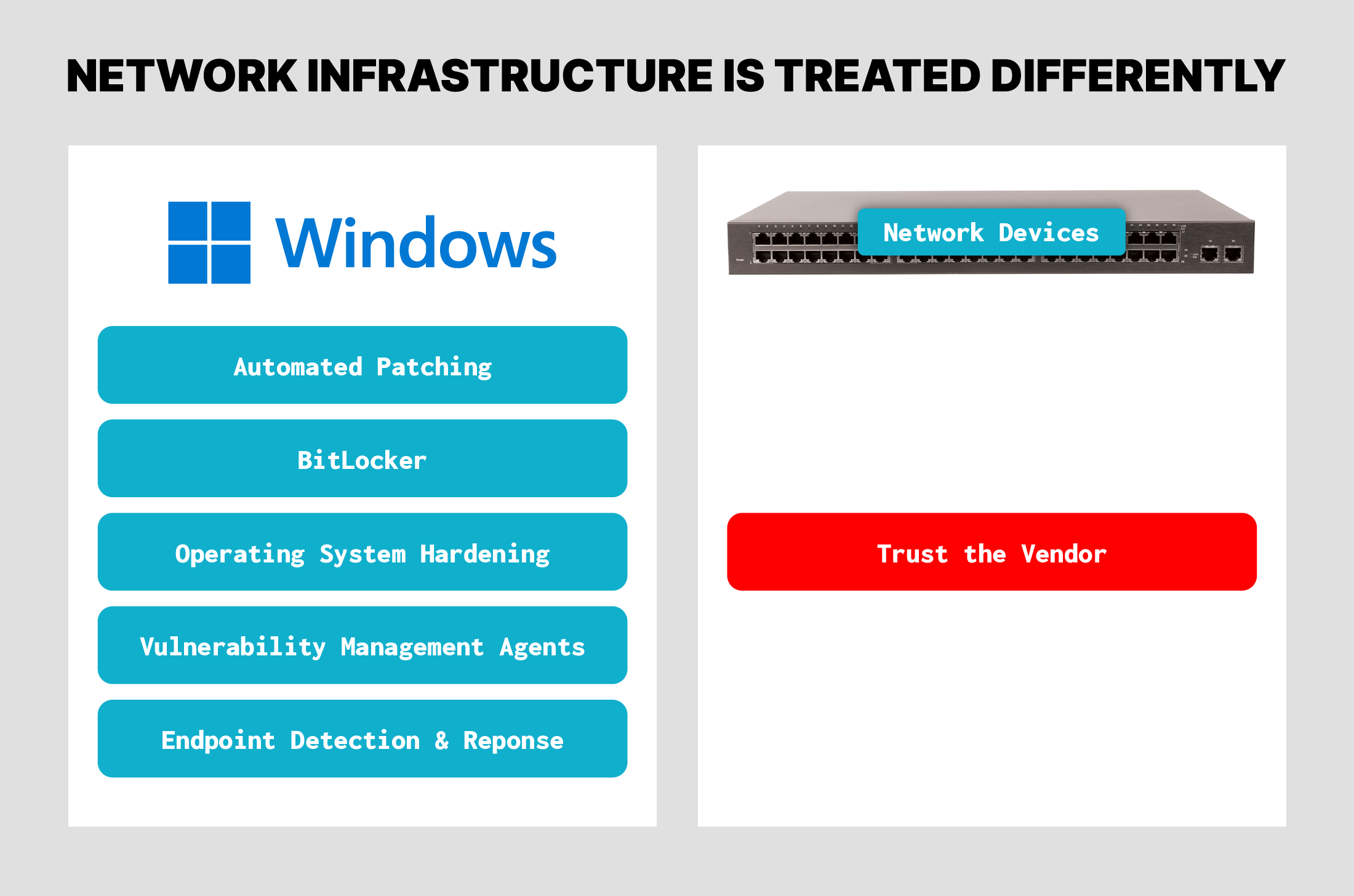
Attackers targeting network infrastructure this way are succeeding in part due to the comparative lack of security measures on these devices. While endpoints and user workstations are subject to many cybersecurity requirements, tests, scans, and regulations, network device security is often assumed to be the responsibility of the vendor. But with over half of the most routinely exploited vulnerabilities affecting network infrastructure, and new vulnerabilities such as this Ivanti Connect Secure CVE being targeted by Silk Typhoon, it is time to start securing network devices more rigorously.
Eclypsium Detects Vulnerabilities and Attacks in Network Devices
The Eclypsium IT Infrastructure Supply Chain Security Platform can discover vulnerabilities and detect indicators of compromise being targeted by the Typhoons and other advanced threat actors. To see the growing list of Typhoon-associated CVEs detected by Eclypsium, read our extensive reporting on the rise of Chinese APT campaigns including Volt Typhoon, Salt Typhoon, Flax Typhoon, Velvet Ant, and more. We also offer a free risk assessment for telecommunications companies and other organizations potentially impacted by Salt Typhoon.
The post Silk Typhoon Targeting IT Supply Chains and Network Devices, Microsoft Reports appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.
*** This is a Security Bloggers Network syndicated blog from Eclypsium | Supply Chain Security for the Modern Enterprise authored by Chris Garland. Read the original post at: https://eclypsium.com/blog/silk-typhoon/
Original Post URL: https://securityboulevard.com/2025/03/silk-typhoon-targeting-it-supply-chains-and-network-devices-microsoft-reports/?utm_source=rss&utm_medium=rss&utm_campaign=silk-typhoon-targeting-it-supply-chains-and-network-devices-microsoft-reports
Category & Tags: Security Bloggers Network,Blog – Security Bloggers Network,Blog
Views: 2





















































