Source: securityboulevard.com – Author: Tova Dvorin
On March 12, 2025, the Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the Federal Bureau of Investigation (FBI) and the Multi-State Information Sharing and Analysis Center (MS-ISAC), issued a joint Cybersecurity Advisory (CSA) titled “#StopRansomware: Medusa Ransomware” (Alert Code: AA25-071A). This advisory provides critical intelligence on the Medusa ransomware variant, including its tactics, techniques, and procedures (TTPs), as well as indicators of compromise (IOCs) identified in recent FBI investigations.
Medusa ransomware has been observed targeting critical infrastructure organizations, demanding ransom payments and threatening to leak stolen data. The advisory details the methods used by Medusa actors to gain access, move laterally, exfiltrate data, and encrypt victim systems. For more information, read the full CISA advisory here.
Understanding the Medusa Ransomware Threat
First identified in June 2021, Medusa operates as a ransomware-as-a-service (RaaS) model, allowing affiliates to deploy the ransomware in exchange for a share of the ransom. Medusa has targeted organizations across finance, healthcare, manufacturing, and government sectors. The ransomware encrypts files and demands payment in cryptocurrency, often using double extortion tactics to threaten the release of sensitive data.
Key Tactics, Techniques, & Procedures (TTPs)
- Initial Access:
- Exploit Public-Facing Application (T1190) – Medusa actors gained access by exploiting vulnerabilities in exposed applications.
- Initial Access Brokers (TA0001) – Medusa actors recruited initial access brokers (IABs) in cybercriminal forums and marketplaces to obtain initial access.
- Phishing (T1566): Phishing emails with malicious attachments or links.
- Defense Evasion:
- Indicator Removal: Clear Command History (T1070.003) & Indicator Removal (T1070) – Medusa actors attempted to cover their tracks by deleting PowerShell command line history and removing traces of their previous activity and tools.
- Obfuscated Files or Information: Encrypted/Encoded File (T1027.013) & Obfuscated Files or Information (T1027) – The attackers used obfuscation techniques, including encoding commands in Base64 and slicing strings into smaller pieces referenced via variables, to evade detection.
- Impair Defenses: Disable or Modify Tools (T1562.001) – Endpoint detection and response (EDR) tools were disabled or deleted to prevent security monitoring and analysis.
- Discovery:
- Network Service Discovery (T1046) & System Network Configuration Discovery (T1016) – Medusa actors utilized living off the land techniques for network enumeration and used OS administrative utilities to gather network configuration information.
- File and Directory Discovery (T1083) & Network Share Discovery (T1135) – Medusa actors employed Windows Command Prompt for filesystem enumeration and queried shared drives on the local system to collect information.
- System Information Discovery (T1082) & Permission Groups Discovery: Domain Groups (T1069.002) – Medusa actors used systeminfo to gather detailed system information and attempted to find domain-level group and permission settings.
- Credential Access:
- Lateral Movement and Execution:
- Lateral Movement (TA0008) – Medusa actors performed techniques to move laterally within the network without detection after gaining initial access.
- Command and Scripting Interpreter: PowerShell (T1059.001) & Command and Scripting Interpreter: Windows Command Shell (T1059.003) – Medusa actors used PowerShell and Windows Command Prompt for ingress, network, and filesystem enumeration, leveraging their interactive command-line interfaces.
- Software Deployment Tools (T1072) & System Services: PsExec (T1569.002) – Medusa actors used tools like PDQ Deploy, BigFix, and Sysinternals PsExec to deploy the encryptor across the network.
- Remote Services: Remote Desktop Protocol (T1021.001) & Windows Management Instrumentation (T1047) – Medusa actors abused Remote Desktop Protocol (RDP) and Windows Management Instrumentation (WMI) to remotely access and control systems for lateral movement and execution.
- Exfiltration and Encryption:
- Command and Control:
- Ingress Tool Transfer (T1105) – Medusa actors used PowerShell, Windows Command Prompt, and certutil for file ingress.
- Application Layer Protocol: Web Protocols (T1071.001) & Remote Access Software (T1219) – Medusa actors communicated using application layer protocols (e.g., HTTPS) to create reverse or bind shells and used remote access software to move laterally through the network.
- Persistence:
- Create Account (T1136.002) – Medusa actors created a domain account to maintain access to victim systems.
- Impact:
- Data Encrypted for Impact (T1486) & Inhibit System Recovery (T1490) – Medusa actors encrypted data on target systems to disrupt availability and terminated services, deleted shadow copies, and encrypted files with AES-256 before dropping the ransom note.
- Financial Theft (T1657) – Victims were required to pay to decrypt files and prevent further release by Medusa actors.
- System Shutdown/Reboot (T1529) & Service Stop (T1489) – Medusa actors manually shut down and encrypted virtual machines, while also terminating services related to backups, security, databases, communication, file sharing, and websites.
Indicators of Compromise (IoCs)
- File Hashes: Unique MD5, SHA-1, and SHA-256 hashes of Medusa ransomware samples.
- IP Addresses: Known command-and-control (C2) server IP addresses.
- Domains: Malicious domains associated with Medusa ransomware campaigns.
SafeBreach Coverage & Playbook Attack Updates
New Attacks Related to US-CERT AA25-071A
The SafeBreach research team has analyzed the latest Medusa ransomware attack techniques and has updated our attack playbooks to reflect the new IoCs outlined in US-CERT AA25-071A. These updates ensure that organizations can proactively simulate Medusa ransomware attacks within their environments and validate their security controls.
The following IoCs have been added:
- #10761 – Write putty (dae4ae) backdoor to disk
- #10762 – Pre-execution phase of putty (dae4ae) backdoor (Windows)
- #10763 – Transfer of putty (dae4ae) backdoor over HTTP/S
- #10764 – Transfer of putty (dae4ae) backdoor over HTTP/S
- #10765 – Email putty (dae4ae) backdoor as a compressed attachment
- #10766 – Email putty (dae4ae) backdoor as a compressed attachment
By running these playbook attacks, security teams can determine whether their existing defenses are effective against Medusa ransomware.
Existing Attacks Related to US-CERT AA25-071A
As soon as details were made available, the SafeBreach Labs teams added attacks based on the advisory and mapped existing attacks in the Hacker’s Playbook to these US-CERT alerts immediately. It is important to note that existing SafeBreach customers already had a good level of coverage against tactics and techniques previously leveraged by the ransomware group identified in the advisory. Please run/re-run the attacks listed below to ensure your environments are protected against these TTPs:
- (100) Covert data asset exfiltration over TCP (Data) (exfiltration)
- (101) Covert data assets exfiltration over UDP (exfiltration)
- (10337) Extract Security information using PowerShell (host level)
- (10338) Extract Windows information using PowerShell (host level)
- (10339) Collect information about antivirus products using CMD (host level)
- (10437) Execute AI Generated sensitive information Infostealer (Windows) (host level)
- (10474) Initiate network connection from startup folder (exfiltration)
- (1693) Collect Windows system data using CMD (host level)
- (192) Brute force attack over RDP protocol (lateral movement)
- (2174) Extract users and groups using net.exe (Windows) (host level)
- (2192) Collect Data from Local Shared Drives using System Commands (host level)
- (2222) Discover Remote Systems using PowerShell (host level)
- (2244) Windows Management Instrumentation Event Subscription (host level)
- (2245) Indicator Removal on Host (Windows) (host level)
- (2389) Modify Firewall Rules using netsh.exe (host level)
- (257) Data Asset Exfiltration using DHCP (exfiltration)
- (2611) Extract system date using PowerShell (host level)
- (3819) Windows Credentials Collection using LaZagne (host level)
- (3828) Credentials collection using PwDump (host level)
- (6127) Extract LSASS memory dump using Rundll32 (host level)
- (6473) Agentless lateral movement via RDP (host level)
- (6580) Discover domain groups using LDAP method (host level)
- (6804) Downgrading powershell version (host level)
- (6909) RDP Connection Between 2 Simulators (lateral movement)
- (6999) Clear Event Logging Policy (host level)
- (7165) Execute generic ransomware from a trusted path on user files (host level)
- (7554) Clear Windows Event Logs (host level)
- (7834) Add Exclusions to Windows Defender (host level)
- (7835) Disable Windows Defender From Registry (host level)
- (8004) Capture Screen using Powershell (host level)
- (806) Collect Files using ZIP (host level)
- (8305) Pack Trickbot trojan using Kiteshield packer and drop to disk (lateral movement)
- (8321) Disable crash memory dump (Windows) (host level)
- (8357) Clear RDP connections history (Windows) (host level)
- (8370) In memory credential extraction via MiniDumpWriteDump (host level)
- (8372) Credential extraction via Pypykatz (host level)
- (8853) Disable rules in Windows Defender to allow credential harvesting using Lazagne (host level)
- (8855) Add exclusion to Windows Defender via writing to registry (host level)
- (8856) Create rule in Windows Defender to delete arbitrary file (host level)
- (912) Start the SSDP discovery service (host level)
- (9413) Enable LMHash Policy (host level)
- (9456) Extract SAM credentials from registry (host level)
What You Should Do Now
SafeBreach customers can now validate their security controls against these TTPs in multiple ways.
Method 1
You can go to the “SafeBreach Scenarios” page and choose AA25-071A (Medusa Ransomware).
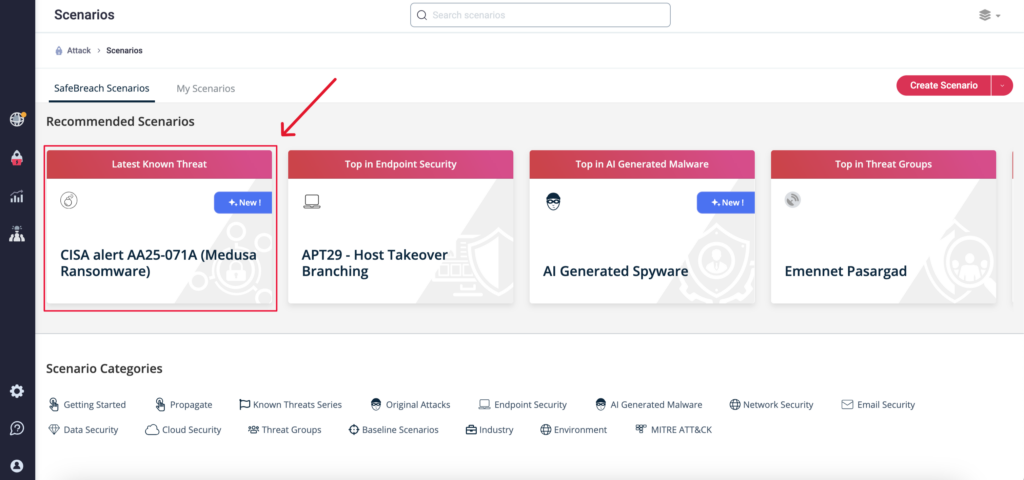
Method 2
From the Attack Playbook, select and filter attacks related to AA25-071A (Medusa Ransomware). Additionally, you can refer to the list above as well to ensure a comprehensive level of coverage.
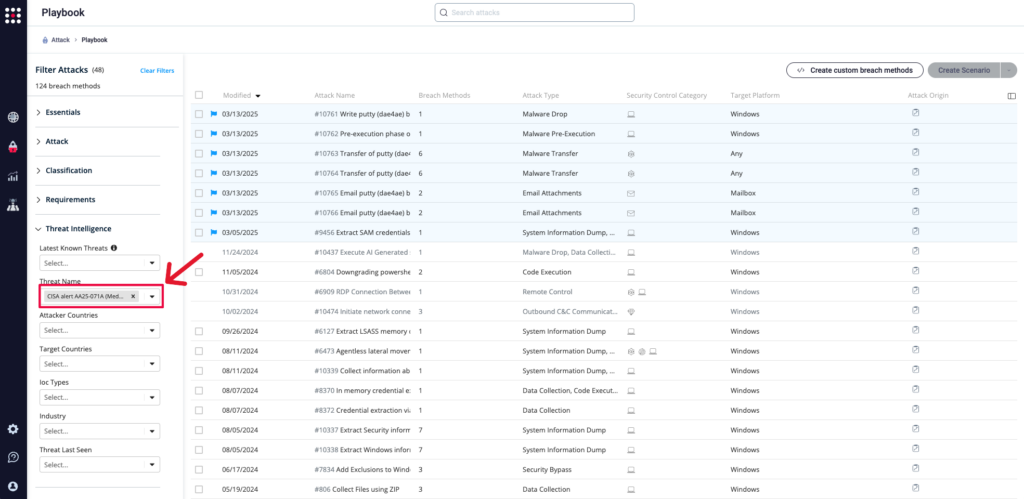
Method 3
From the Known Attack Series report, select the US CERT Alert AA25-071A (Medusa Ransomware) report and select Run Simulations, which will run all attack methods.
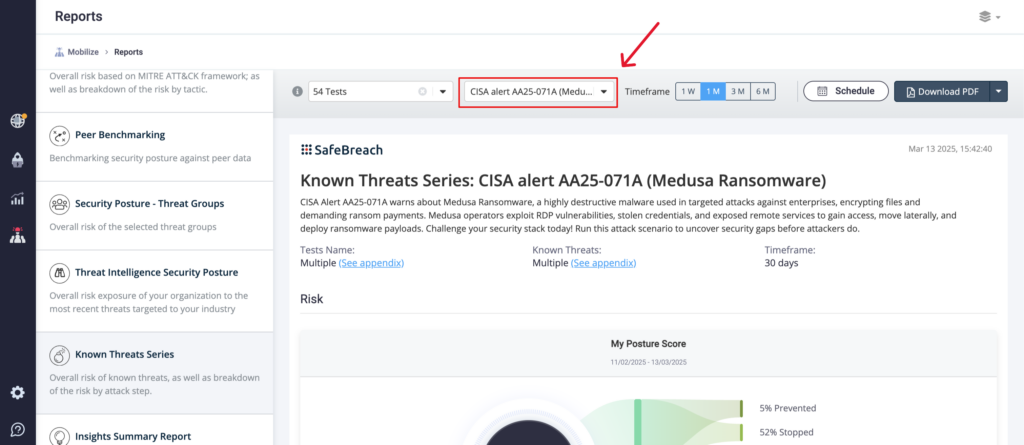
Additional Advisory Steps
To ensure your organization is protected against Medusa ransomware, we recommend the following steps:
- Run the SafeBreach Platform Simulations:
- Log into the SafeBreach platform and navigate to the updated Medusa playbooks.
- Execute the relevant attack simulations to assess your exposure.
- Review the results to identify security gaps.
- Mitigation Strategies:
- Enable Multi-Factor Authentication (MFA): Protect user accounts from credential theft.
- Patch Known Vulnerabilities: Regularly update systems to prevent exploitation.
- Monitor for IOCs: Use threat intelligence feeds to detect Medusa-related activity.
- Segment Networks: Restrict lateral movement by limiting interconnectivity.
- Backup Critical Data: Maintain encrypted, offline backups to restore in case of an attack.
- Leverage SafeBreach Insights:
- Use SafeBreach Labs’ real-time threat intelligence to stay ahead of emerging ransomware threats.
- Schedule a Blitz Call with our research team to discuss specific recommendations for your security posture.
For a complete view of your security gaps against Medusa ransomware, sign into SafeBreach now and test your defenses.
You Might Also Be Interested In
Get the latest
research and news
The post SafeBreach Coverage for US CERT AA25-071A (Medusa Ransomware) appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by Tova Dvorin. Read the original post at: https://www.safebreach.com/blog/safebreach-coverage-for-us-cert-aa25-071a-medusa-ransomware/
Original Post URL: https://securityboulevard.com/2025/03/safebreach-coverage-for-us-cert-aa25-071a-medusa-ransomware/?utm_source=rss&utm_medium=rss&utm_campaign=safebreach-coverage-for-us-cert-aa25-071a-medusa-ransomware
Category & Tags: Security Bloggers Network – Security Bloggers Network
Views: 2






















































